Hack Facebook Passwords Tutorial
Understand how
to hack Facebook

Hack Facebook Passwords Tutorial
Understand how
to hack Facebook

Please note that what we are revealing here is for informational purposes only and should not be reproduced on anyone's account!
Hacking a Facebook password is really simple. Hackers most of the time don't even have a majority when they hack into their first Facebook account.
So how do they go about doing it? There aren't as many solutions as you might think and the TV shows only make people believe false ideas about Facebook hacking.
When an account is hacked, the user does not notice it. He is far from imagining what happened to him simply because everything is virtual, the hacker only enters his information virtually, behind a computer screen. It is not comparable to a burglary, even if the term is psychologically the same thing, but here nothing was definitely stolen. Except in an extreme case where the account is deleted, most of the time, the hacker duplicates the data.
The hacker then wants to use it to make money. And yes, don't think he's going to do this just for fun... his goal after a Facebook hack is to get a reward.
For example, he will contact the friends of the victim's profile and ask for financial assistance by usurping his identity. Or he will simply post links on the wall to advertising sites (spam, sale of drugs, etc.) and make his friends believe that it's really the best. The victim's friends will believe that he is the one who posted this link and will click on it. They will fall into the hacker's trap. Hackers can also sell hacked Facebook accounts on the black market for a few US dollars.
Here are some techniques commonly used by hackers to hack into your Facebook account. These methods may be able to help you better protect yourself or a hack on your side for educational purposes.
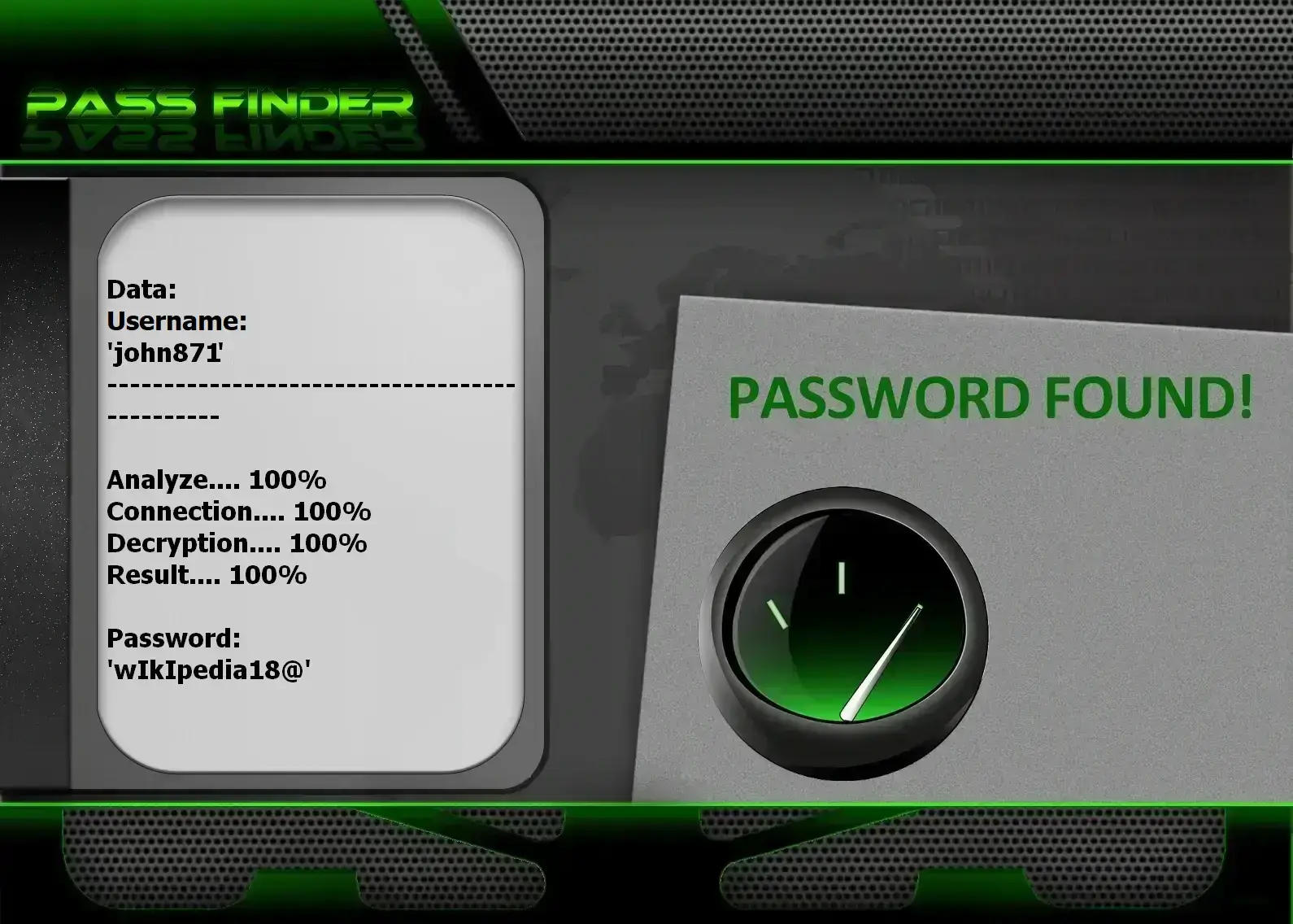
using PASS FINDER and @username
(also works with a phone number or email address).
This technology enables you to access a Facebook profile using an email address, a @username, or a phone number. It’s a solution for cracking Facebook passwords, allowing you to log into the account afterward. To begin recovering your password or securing your account, go to the target Facebook profile, locate the email address displayed on the user’s info page, and enter it into the software’s input field.
PASS FINDER works on mobile devices and eliminates tedious steps like switching to a computer and navigating to Facebook’s login page to decrypt the password. It’s completely straightforward.
The goal is to ensure that anyone can use PASS FINDER. That’s why you can try it directly from its official website—PASS FINDER is designed for a broad audience who want to quickly regain access to their login credentials and passwords.
Official website link: https://www.passwordrevelator.net/en/passfinder
Among those that can constitute a real cyber threat, there are security breaches. These vulnerabilities are not user dependent. No matter what IT we use, there is always a security hole that can be exploited against us. Of course, cybercriminals know this. There are even a lot of security vulnerabilities that are in circulation sold at certain prices or even made available for free. A security breach is a design flaw that can be used to gain access to a computer terminal without the knowledge of the main user. Thanks to technological development in hacking, it is even possible today to hack someone without the latter even having to lift a finger. In this context we speak of a zero-click exploit. These vulnerabilities which, when properly exploited, can expose the user to many surprises. It is this situation that was highlighted with the Pegasus scandal which demonstrated that these security breaches can be a real plague for our online privacy.

Session hijackings are classics in hacking. They have the merit of allowing the user to be hacked without the latter even realizing the exact problem he is going through. As the name so clearly suggests, session hijacking is exactly about driving the user who wants to connect to a particular web platform to another platform for various reasons. The first session hijacking may be aimed purely at infecting the infected with a malicious program following its connection to the corrupted platform. This can be seen in several cases when you click on a link or a tab while visiting an unsafe website.
In another case of assignment hijacking, hackers aim to monitor user traffic. For this, it uses cookies saved by the latter on its browser. The diversion here is only temporary because once the connection is intercepted, the hacker will then send the user to the platform he wants to use. Obviously after collecting all the information it needs for other purposes. As part of DNS poisoning, session hijacking will consist in making the user believe that he is on the exact platform he wants. Here its hijacking starts from the browser when it enters the URL address of the web platform. Thanks to the DNS cookies already corrupted by the cyber criminals, the latter is immediately directed to another platform which is under the control of the hackers but which usurps the identity of the first.
Thanks to these highly advanced hacking methods, it is easy for a malicious hacker to hack social media accounts such as Facebook. Because all it takes is a few clicks to get all of your personal data.

SIM card hacking is not widely known as a common hacking method. However, it is as dangerous as any technique that can be used by hackers. The SIM card is above all a computer tool with data inputs and outputs. In the current era, knowing that almost everyone uses smartphones, the SIM card is an essential or even essential tool today in our access to the Internet and social networks. Today there are two methods of hacking SIM cards that can have serious consequences on our habits:

Malware is at the heart of hacking. It is very likely that a Facebook account hacker will require the intervention of one or more malware. It is for this reason that we cannot discuss this selection of hacking methods without mentioning the use of malicious computer programs. In the category of " how to hack a Facebook account?" there are a couple of malware you should be aware of that are used in this context:

Dataleaks occur when an organization loses control and management of a set of digital information that it is supposed to manage and protect. Nowadays, Dataleaks are very common, especially in social networks which are generally the biggest companies for centralizing personal data. It is legitimate for you to wonder how data leaks can be used against you to hack your Facebook account. When there is a data leak, you have to know that there is a lot of information that becomes available and usable by anyone. Therefore, your passwords can also be recovered as well as all your login credentials.
The first piece of advice is of course to be disciplined. The discipline will consist in knowing how to properly manage the use of these passwords. As you know, it is generally not recommended to use the same password on several accounts at the same time. Then, the composition of your password must be done with seriousness and avoid that it is easily guessed. Today we speak of a passphrase instead of a password. Also, seriously consider protecting your connections with some essential tools. In particular, we think:
If by chance, you are caught off guard and are looking for an effective way to hack a password regardless of the Facebook account, use PASS FINDER. It is an efficient software adapted to your needs. Thanks to this computer program, you are sure to never lose control of your Facebook account again. It can let you find any Facebook account password in just a few minutes.
Hacking a Facebook password might seem simple to some, but it requires a certain level of skill and knowledge. There are various techniques and methods used by hackers and the ease of hacking depends on factors such as the security measures in place and the vulnerability of the target.
No, hacking into someone's Facebook account without their consent is illegal and considered a violation of privacy and cybersecurity laws in most countries. It can lead to severe consequences, including legal action and criminal charges.
There are several steps you can take to enhance the security of your Facebook account:
If you suspect that your Facebook account has been hacked, take immediate action: