Hack Yahoo! password!
Yahoo! mail is not safe!

Hack Yahoo! password!
Yahoo! mail is not safe!

According to hackers, cracking a Yahoo! is very easy. There are no less than 1 billion Yahoo! cracked. It's huge when you think about it, especially when it was done by one person. Yahoo! is one of the most visited web platforms in the world. At some point in the history of the Internet, almost every user had at least one Yahoo! account. If today GMail has largely passed in front of it, one cannot also deny that there are many users who continue to use Yahoo! and that almost every day. Therefore, let's discuss the security of a Yahoo! account.
It is obvious that before talking about any type of hacking, the most important thing is to know how to bypass the password. Why the password?
Quite simply because it is the first identifier that serves as a barrier when trying to hack a person. It is for this reason that you must first think about cracking it. There are many password cracking methods. While some use software to successfully circumvent this security, there are direct practices that just require a certain mastery.
So here are some methods that can be used to bypass your Yahoo! password security:
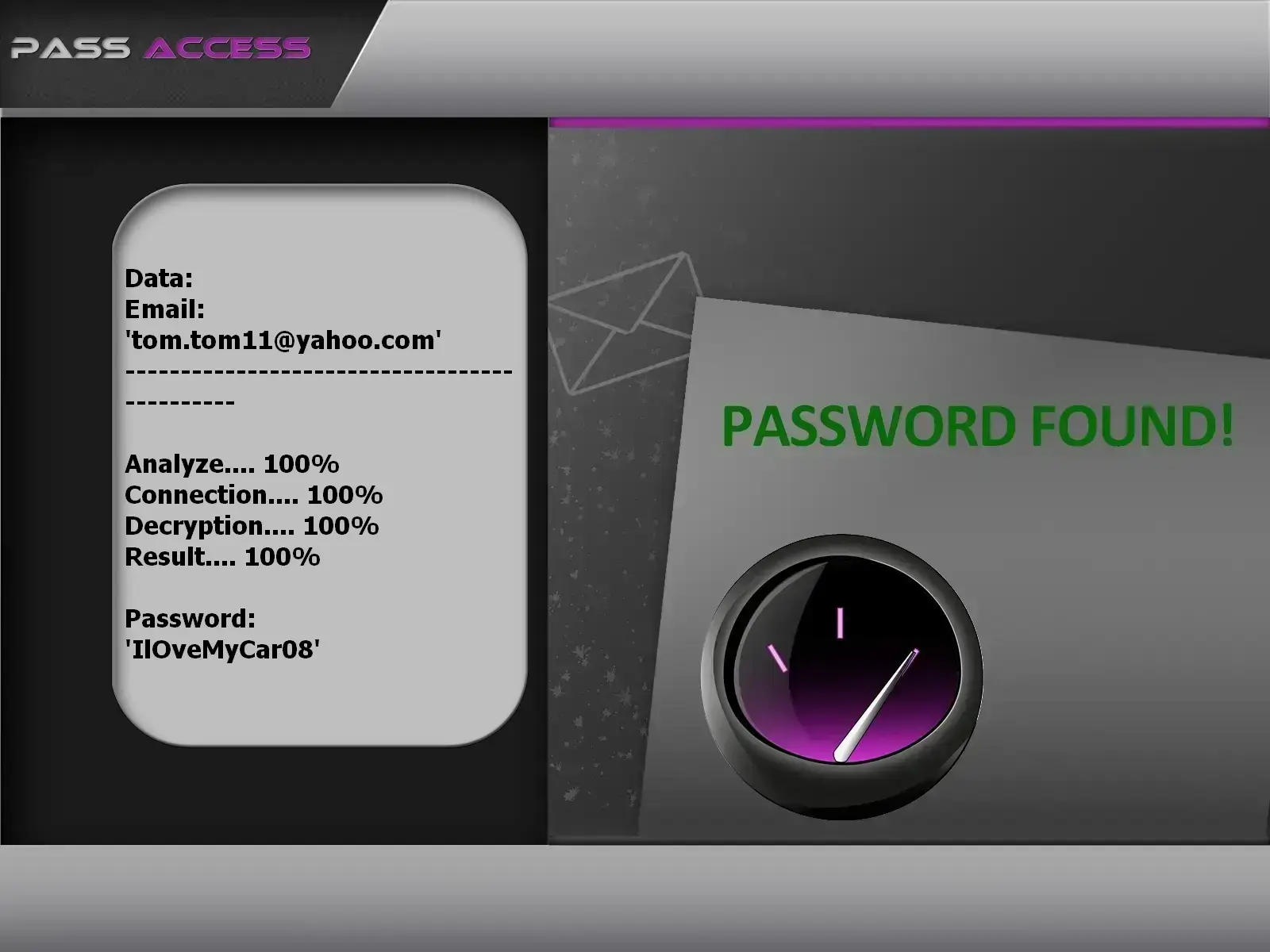
using PASS ACCESS.
PASS ACCESS is software for accessing Yahoo! while maintaining his anonymity. It bypasses double authentication protections and displays the password in plain text on your screen. Whether the password is encrypted or not, PASS ACCESS will be able to decrypt it. This is a program designed specifically to help you find the PASSWORD of any Yahoo! account. It is primarily useful for people who have forgotten their password or are looking to test their account security.
Designed by cybersecurity specialists, it allows in a few minutes to be able to decode the password and facilitate the connection in just a few clicks.
Unlike most apps that are supposed to help you crack Yahoo! passwords, this one doesn't really require any special information or knowledge. In other words, anyone with a computer background can use it without fear.
To do this, you just need to follow the three steps mentioned below:
We must mention the ease of use of this application. Indeed, you do not need to install it on another computer device than yours, which does not put you in embarrassing situations. In addition, you have a one-month trial and at the end of this trial period, you are either satisfied or refunded.
Try PASS ACCESS now by downloading it from its official website: https://www.passwordrevelator.net/en/passaccess
More often than not, not much is said about this cybercrime technique which is the interception of network traffic. Therefore, you will hardly find documentation allowing you to learn about the subject. The most important thing is that it is a practice that is organized with the aim of stealing sensitive data, spying and perhaps sabotaging.
First of all, the hacker who wants to initiate a traffic interception must first seek to collect information on the targeted network. It's usually something that can be done quite easily by going over WiFi for example or by monitoring a user in relation to his actions and his computer practices. Some cybercriminals use sniffing software to investigate a remote network. Thanks to the information collected, the next step will consist in collecting the IP addresses that are present in the LAN network. This is not only IP addresses but also information relating to the equipment used as well as the servers used if possible. With all of this data, cybercriminals can divert traffic to devices whose signatures they will steal. In this data theft, personal data such as passwords and other connection identifiers are concerned.

Packet sniffing is a practice that consists of monitoring and capturing all the data packets that pass through a network using computer programs and hardware designed specifically for this purpose. This method allows a hacker to be able to spy on and even access an entire computer network from their location. Of course, such possibilities can have the immediate consequence of the theft of sensitive data, namely passwords. It's not just about passwords. In addition to your login credentials, the activity of your computer devices may be spied on and your communications diverted.
You have to go through several steps. In the beginning, the hacker must connect his computer terminal to a switch port. The second step will consist of using discovery tools that will allow him to know what type of network he intends to target. Once the analysis is complete, it tries to find a way to attack its victim directly. For this he will poison, thanks to a malicious program, the computer terminal of his target. Especially through ARP spoofing. If he succeeds in this step, all of the traffic that is supposedly destined for his target's machine will be diverted by him. The hacker will simply have to collect the data that interests him.

In a down-to-earth way, it's a way to monitor another person's phone conversation through the various tools that victims use. This can be both a telephone communication or a communication via the Internet. In the context of computer hacking, the cyber malevolent will use listening devices or spyware which will be directly connected to the circuit of the targeted network. In order to intercept data, it must record all the information it is going to intercept and record all this data flow between the target and its host. It should be noted that the technique of telephone tapping can have two variants:

A good malicious technique which consists in creating a Yahoo! similar to yours. The hacker will collect information about you to make their account look genuinely legit. His account will be equivalent to yours except for a few spelling changes. It may deceive your vigilance and that of your contacts and acquaintances. This is very annoying because the hacker can contact them and make them believe that he has lost access to his Yahoo! account. If one of his friends has a recovery email, you can imagine that behind your back, you will immediately lose control of your Yahoo! account.

IRDP (ICMP Router Discovery Protocol) is a router protocol that allows a host terminal to highlight the IP addresses of active routers after having received the solicitation messages from these computer terminals through their network.
In this situation the hackers have discovered a possibility of being able to spoof the host. Their technique is simply to send a warning message through an IRDP router that has been spoofed from a subnet host terminal. They can therefore change the default routers by specifying the one that the hacker has chosen. In this condition, the latter can simply collect the data that will pass through this terminal.

When we have a computer device, there is one piece of information that we do not have or that we constantly neglect: the reality and persistence of security breaches. Security vulnerabilities are inherent design flaws in all computer devices and software. In other words, there is no such thing as a computer device or computer programs without security flaws. It is for this reason that manufacturers and application publishers always do their best to offer updates that correct these design flaws. This is an essential thing to understand as a digital service user. Security vulnerabilities are dangerous since hackers can use them to hack into us on a daily basis. As they are design flaws, these vulnerabilities are used to circumvent the security policies that we deploy in our smartphones, computers and tablets. Note that the most dangerous flaws are Zero Click exploits. Zero Click flaws are used to qualify a practice of cyber malice which consists of infecting, corrupting, spying on, destroying a computer device remotely without its user knowing or even doing anything. In other words, it's the ultimate computer attack that takes place in absolute silence and in total invisibility.

It is not uncommon for users to use their Google Chrome or Microsoft Edge browser to sign in to their Yahoo! account. During these connections, we are often asked to save the passwords. Sometimes registration is done automatically. This feature is quite handy because it ensures that the next time the user logs in, he won't have to waste time entering his own login credentials again. However there is a problem with the use of such methods. Indeed, passwords are not really secure on these browsers. Unfortunately, each time you save your password on a browser, it is stored directly without any protection or encryption. Moreover, if a person manages to access your computer terminal and your browser, it will be quite easy for the latter to recover your identifier without making great efforts.

A botnet is the set of computer programs (computers, smartphones, connected objects, etc.) that have been connected to each other thanks to a malicious program that controls them remotely, allowing them to perform specific tasks. The word botnet derives from the English expression " roBOT NETwork ".
Connecting enough devices together allows hackers to generate enough computing power that can help them carry out computer attacks of considerable magnitude. Most often cybercriminals behind botnets are very popular and known to be the cause of high-impact cyberattacks.
When a computing device is infected with a botnet, it can be used in different ways by hackers. Useful to know:

After knowing all these cracking techniques, you must seek to better protect your Yahoo! account.
Security is then essential. The problem that arises most in this context is to know what are the best practices to improve your security. You have to know that everything lies in discipline. Using an online account means being constantly on the alert, having the latest information on the evolution of cyber malware and the methods needed to counter it. But first of all, here are some basics: