Hack a Yahoo! account
No password is infallible

Hack a Yahoo! account
No password is infallible

It is important to understand the methods used by hackers to protect yourself against them.
Discover methods of hacking Yahoo!:
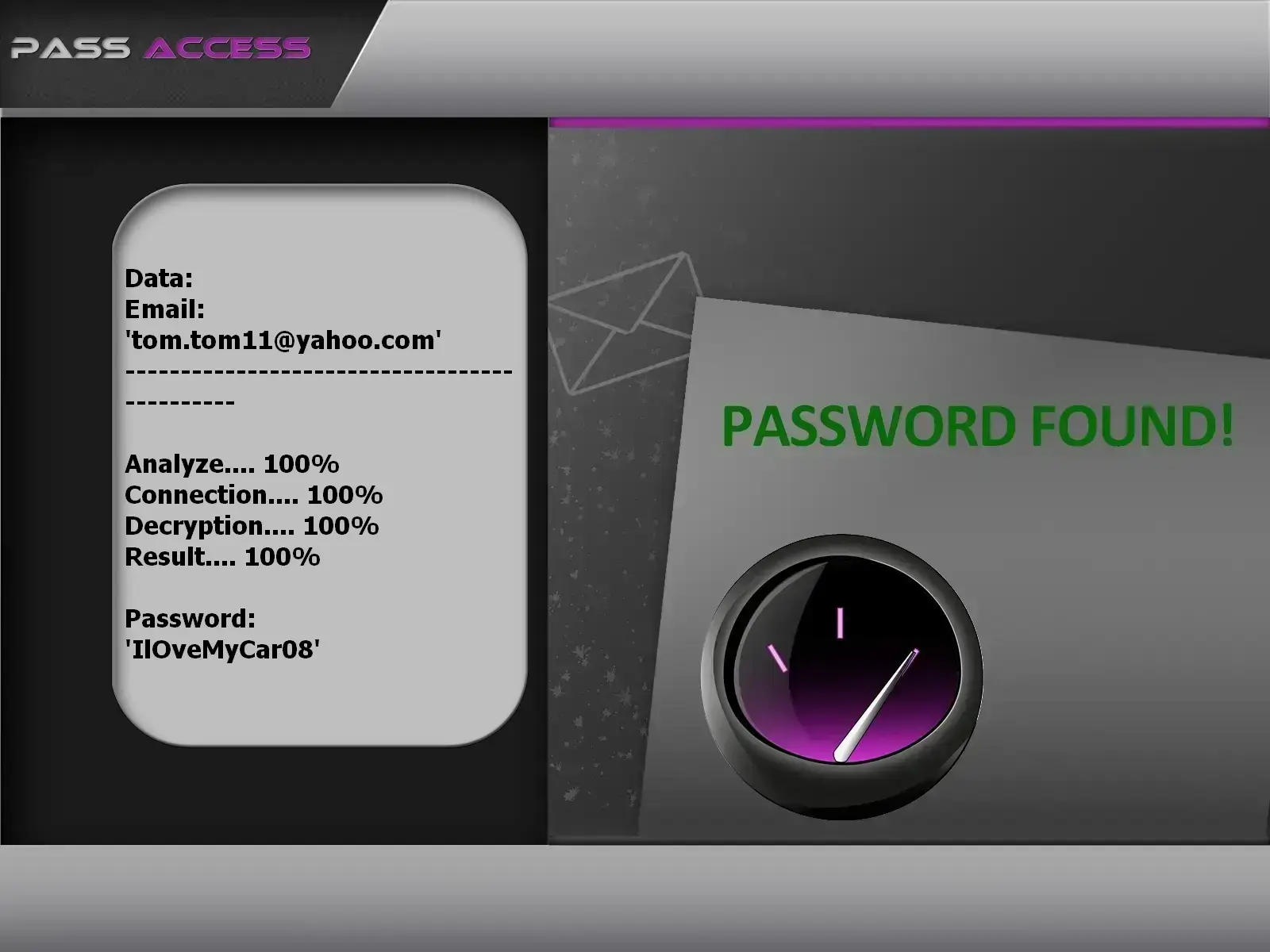
using PASS ACCESS.
This software allows you to recover a Yahoo! simply from an email. Simply enter the login in the box provided for this purpose so that PASS ACCESS recovers the password associated with the account. It finds the password and deciphers access in just a few minutes.
You can download PASS ACCESS from its official website: https://www.passwordrevelator.net/en/passaccess
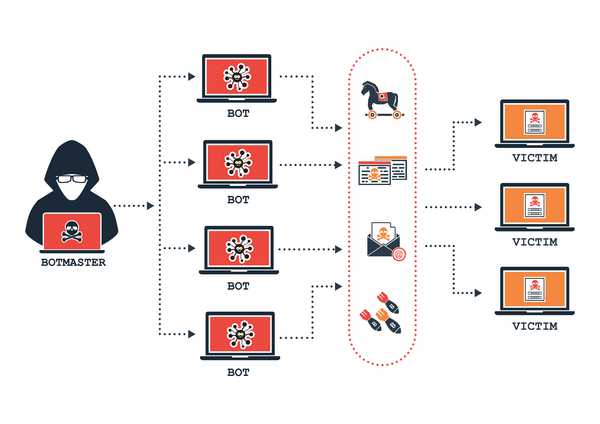
A botnet is a network of computers that provides synchronized computing power in order to perform actions with enormous power. They are also called " Zombies ". This network of computers allows hackers to launch multiple attacks at once. Their powers being increased by the fusion of several computers, most of the time it involves thousands of computers. Botnets work by infecting a computer system and succeed in their actions most of the time. Hackers therefore use malicious software to connect computers or smartphones together. This weakens the defenses of the user who sees the performance of his computing device reduced drastically.

This attack consists of drawing passwords stored in local databases often managed by browsers or applications. When you access a social network, or your Yahoo! account, the passwords are stored and protected with an encryption measure preventing anyone from accessing them. We then say that the passwords are hashed. The hashing system can be circumvented with this technique. Indeed, hackers have algorithms that allow them to decode the hash and discover the content of the password in plain text. There is one condition: the hacker must access the database containing the hashed data. But it's not really a difficult thing to do. Today, they achieve this by exploiting data vulnerabilities or by simply obtaining them from the Dark Web.

There is malware that gives access to hackers to be able to record the screen of the infected computer device. Which means that everything you do on your computer or smartphone can be monitored remotely. This obviously includes the use of passwords when logging in. Thanks to their tools, they know exactly how to collect your personal data. To install it on a device, they usually use the phishing technique or find a way to access it physically. You should just be aware that it is malicious program that allows surveillance. This kind of method looks like the same operating mode as spyware or keyloggers. They generally are very discreet computer programs and they know exactly how to exploit users' bad practices against them.
Like the previous application, it also allows to extract information from the victim's activity. He mainly focuses on what is typed on a keyboard. Which means that if a smartphone or a computer is corrupted by a keylogger, then the hacker behind this malicious program will be able to know what the victim is going to type on the terminal keyboard. And of course, we all know that we frequently enter our passwords. Your Yahoo! account becomes vulnerable if you are caught in this kind of cyber malicious activity.

It often happens that we save the login ID each time we log into our online accounts. This is a very practical function that allows us to save a lot more time.
This is a simple option to activate on the web browser used. This can be, for example, Google Chrome. By accessing the settings, you will find a tab dedicated to the form and the password. You will see a set of saved credentials. You can search for the password you are interested in from the appropriate email address. However, it is possible for hackers to push the exploitation of this feature which is initially made to facilitate the user.
Indeed, browser cookies can also be used by hackers. Cookies store all of our personal data when we browse the Internet. When a user writes his username and password, the cookies record everything without being aware of it. Once the hacker has gained access to the cookies, they can simulate your presence and log in as if it were you on a browser.
This is a very simple method that does not require deploying a lot of resources. However, this requires the hacker to physically gain access to the victim's computing device. If he succeeds in gaining access to it, he can retrieve the identifier that interests him in less than a minute.

It may happen that a user forgets for example his password. For this, there is a dedicated function that allows him to recover it easily. He must click on the tab that mentions " forgotten password ". Then he will be redirected to a recovery page. Thanks to this, he will then be asked to enter personal information that allows him to be identified. Once the identification is confirmed, the user can then change the password he has forgotten.
Provided that the hacker knows the necessary credentials, he can simply initiate password recovery and impersonate you by accurately confirming your identity. Of course, for the hacker to be able to exploit this method, he must first access your mailbox. Which is not really complicated insofar as he can use phishing or social engineering.
They use a technique called " clickjacking " which involves placing a hidden virus behind an image. The way it works is really very simple. The pirate will create a website with a button indicating " win a gift " for example. Unfortunately, this is a trap. Indeed, the hacker loaded an iframe on your Yahoo! email account aligned in exactly the same place as the " change password " button.
The victim does not suspect anything and clicks on this particular button which, then, will change and save the new password for the Yahoo! account.
There are some hacking methods that don't require to go through the internet. Which means that when you're offline you mustn't think you're safe, the hacking of your Yahoo! account is always possible. Indeed there are techniques that can vary depending on the context but which manage to hack without being connected to the Internet. Here are a few:
Data theft with LED light : Do you know that the LED beam from your screens can be used to steal your passwords? Indeed some researchers have discovered that when you use a computer device, by using special light processing software, it is possible to convert the light rays from the screen into binary codes. The hacker equipped with a webcam directed towards your screen, intercepts these rays and converts them into readable code in order to know your Yahoo! password.
RJ45 ethernet cable hacking: Ethernet networks are designed to be isolated. The objective of the development of such a network lies essentially in the fact that they want to avoid any intrusion coming from external malevolent actors. However, no intrusion is impossible, in fact, there are techniques that allow hackers to be able to connect to the data despite this. This is the technique called “LANtenna Attak”. It essentially consists of capturing the vibrations emitted by the RJ45 cables which can be converted into intelligible information. However, it will first be necessary for the hacker to have previously installed special software on the devices connected to the Ethernet network in order to push the infrastructure to emit ultrasound. These ultrasounds are then captured with an antenna and will be the receivers which will allow the processing of the information.
Hacking via Bluetooth : Bluetooth is a wireless network that also allows communication between several computer devices. Like the Internet, cybercriminals have developed a method that allows them to use security flaws present in the very functioning of Bluetooth to hack into targeted people. The objective is of course that your personal data such as your Yahoo! login ID be compromised. They will arrange for you to accept pairing between their devices and yours.
Hacking via the USB cable : there are several techniques that allow the use of the USB cable. These wires, which generally allow you to charge your phone, are also ways to trick you and collect sensitive information. When you are in a public place, there are often USB charging stations. This can allow people who are in a waiting room to be able to recharge their smartphone. The trick is that hackers install file extractors on these charging stations. Obviously you have virtually no protection against this kind of problem. iPhones are particularly vulnerable to this hacking technique because of the generalities present in the lightning cable.
Hacking through the GSM network: before the democratization of the Internet network, the GSM network was literally the means of communication. We can safely say that today it is the most widely used network in the world. It is mainly used to transmit telephone calls. Computer hacking professionals have discovered a technique that allows a computer to be hacked through this network, which basically only serves to transmit cellular calls. The technique will rely on the development of software that is able to use electromagnetic waves and force the computer bus of the targeted computer's memory to react like a telephone antenna. All of this setup is to trick the computer into transmitting like a cellular phone. To work properly, it will rely on the fact that computer memory works through a multi-channel architecture. This amplifies the signal. That's not all, you need to use a rootkit for mobile devices. It must be embedded in the radio chip of the mobile phone to be used for transmissions. A complex procedure but which definitively can achieve good results when everything goes as it should.

Let's just note that hacking of Yahoo! account responds to a need for data accumulation. First, if they manage to gain access to yours, it will be easy to steal your identity. In addition, do not forget that your email account is always associated with your social network accounts. A hacker who can hijack your email account will have the ability to hijack all of your social media accounts affiliated with that email account. This demonstrates how dangerous it is to neglect the security of your email.
The hacker of a Yahoo! account can also impersonate the target. This can have a professional impact if the account is used that way. The hacked account could also be used to carry out other cyberattacks such as emptying your bank account or scamming your relatives.
Finally, there is also computer hacking carried out by relatives in order to be able to monitor the person with the aim of discovering secret information. A parent can decide for example to control the activity of his child, it can also be a jealous spouse.
Of course the reasons differ. But it is important to point out that hacking the Yahoo! account of a person without their consent is an offence. This is punishable by law. It is for this reason that regardless of the reason you give, if you ever want to initiate an attack, make sure to stay within the law.
The idea is to know what good practices to adopt in order to minimize the risk of hacking. We talk about reducing the risk of hacking because it is impossible to be 100% secure. However, you can ensure that the hacker who decides to attack you cannot do so easily. Here are some guidelines for you:
Cracking Yahoo passwords or any other online account without proper authorization is illegal and considered a violation of privacy and cybersecurity laws in most countries.
While nothing can guarantee absolute protection, there are several measures you can take to enhance the security of your Yahoo account, such as using strong passwords, enabling two-factor authentication and being cautious of phishing attempts.
If you notice any suspicious activity on your Yahoo account, such as unrecognized logins or unusual changes to your settings, it's essential to act quickly. Immediately change your password, review your account settings and consider contacting Yahoo support for further assistance.
It's generally recommended to change your Yahoo password regularly, ideally every few months. Regularly updating your password can help minimize the risk of unauthorized access, especially in the event of a data breach.
Using public WiFi can expose your Yahoo account to security risks, as these networks may not be secure. It's advisable to avoid logging into your Yahoo account or accessing sensitive information when connected to public WiFi networks, as they could be vulnerable to hacking or surveillance.
If you believe you've fallen victim to a phishing attack targeting your Yahoo account, immediately change your password and review your account settings for any unauthorized changes. Additionally, report the phishing attempt to Yahoo to help protect other users from similar scams.
If your Yahoo account has been hacked, you should attempt to regain access by following Yahoo's account recovery process. This typically involves verifying your identity through recovery options such as email or phone number verification.
While there are various tools and services available to enhance online security, it's essential to be cautious when using third-party services. Always ensure that any tools or services you use are reputable and legitimate and be wary of scams or malicious software.