Hacking an Outlook password
Email are not secure as they should

Hacking an Outlook password
Email are not secure as they should

Many hackers hack for the pleasure of spying. A bit like they were Big Brother. They do this by installing some scripts, backdoors or third-party applications that they have usurped to appear more believable. Users will not be wary and trust what they install.
It's important to check the email you want to open. A hacker could modify the data on your hard drive with this little Outlook hacking script. It could siphon all data, including your emails and contacts. This hack would send spam to promote advertising for a political party or drug sales. The dangerous thing is that it could also be used to hack other Outlook adresses and spread spam.
Nearly 1 email out of 130 would contain a dangerous file. Hackers have lists of email addresses to send their fraudulent messages. The average is a piracy on 20,000 emails. There are more than 5 billion devices on Earth, imagine the spread of these hacks.
We have ranked some hacking techniques for you. Some you know for sure and some you may not know. We wanted to share these methods with you in order to understand how Outlook account can be hijacked:
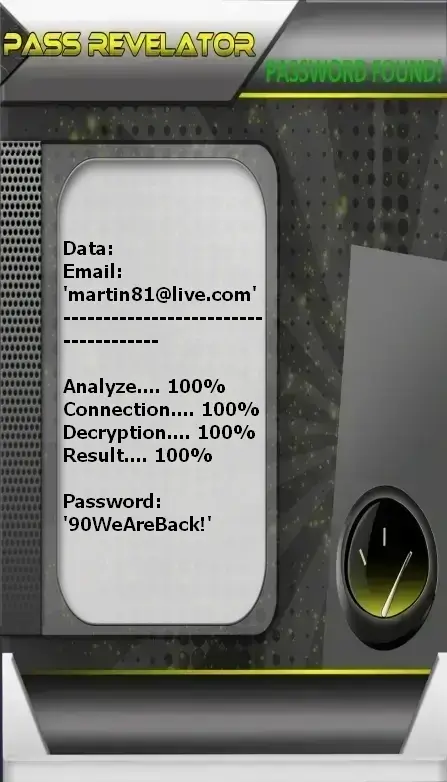
This simple and fast application lets you hack the access code to an Outlook account in no time. Even if the password is encrypted or the account is protected by two-factor authentication, PASS REVELATOR is the most complete solution. In this case, we offer you a software tool that can certainly help. Plus, you get a 30-day trial to be fully refunded.
If you need to recover an Outlook account, PASS REVELATOR is the solution for you.
You can download it from the official website: https://www.passwordrevelator.net/en/passrevelator

This technique essentially targets the use of SIM cards. The objective of the hacker behind Simjacking is to exploit security vulnerabilities in order to use them to collect data on his target. It is a technique which is not very popular, however the danger concerning its use against any person. Indeed, we all use a SIM card in one way or another. Whether physical SIM or e-SIM, the reality is that this little computer tool has become almost essential. Moreover, the problem related to the SIM card dates back to 2009 when it was highlighted on several occasions that the majority of these terminals in circulation have not been updated. Which means that there are still several vulnerabilities that can be used against the user without their knowledge. One of the concerns with SIM jacking is that the victim has no way to defend themselves, since he cannot know if his SIM card is faulty.

We still continue in the category of SIM card hacks. It is important to focus on SIM cards because in an environment where security measures are increasingly developed, the best way that hackers can develop would of course be to take advantage of SIM card vulnerabilities. The SIM Swap is a method which consists in usurping the identity of a particular person and making sure to hijack their SIM card and use it without their knowledge. In this context, the hacker does everything possible to get in touch with the telephone operator of his target. He will pretend to have had a problem with a real SIM card and then request a transfer of the telephone number to another SIM card that he may have in his procession. When he has proven his identity using information that he will surely have stolen, your SIM card is now at his mercy. The danger of SIM swap lies in the fact that the majority of our online accounts are often linked to our telephone number. This gives him the possibility of being able to hijack the accounts.
USB cables as we know are not designed only to charge our phones. The usefulness of this piece of wire also lies in the transfer of data from the smartphone to other terminals. In certain situations, we often have to ask where to borrow the USB cables to charge our phones. Which can probably cause serious problems because these cables can be modified and used to hack into our phones. Beyond using someone else's cable, it's not uncommon to use USB ports installed all over public spaces to help charge a smartphone. Well, these ports may also be contaminated by hackers in order to use the data transfer functionality of your USB cable.

In the category of very little known but commonly used hacking methods, we certainly have the download method. How do hackers do in this context? They just start hacking websites that aren't secure enough. Then they will insert malicious scripts into the http or PHP code of these websites. This allows them to install malware directly on the computer terminal of visitors to this website using a stealth download technique. This download can be initiated either without the knowledge of the latter or with his agreement but camouflaged behind another solution. Once the download is complete and the malware is installed, the theft of your personal data and other strategies will be triggered, which endangers the security of all your accounts.
We are talking about yet another computing technique that does not directly target the user. Before carrying out any attack against the end user, the hacker will first target those who tend to exploit user databases. During its realization, the latter will therefore execute a piece of SQL-type code, a standardized computer language that will allow it to manipulate these databases used by Internet sites. If he ever succeeds in his master stroke at this level, he can thus easily access data. Which can backfire on users who don't have a clue what's going on. Because by directly accessing the data of the websites, the hacker has the possibility of collecting this data to modify or delete it.

We cannot talk about an Outlook account computer attack without mentioning the Trojan horse. The Trojan horse is the malware par excellence for hacking practices. If its use is reserved for a certain category of very professional and experienced hackers, the fact remains that it remains a very obvious and persistent threat. The Trojan can be installed on our smartphone or computer without our knowledge. It can even be installed on the computer terminal by the user itself. Indeed, the particularity of this malicious program is to be discreet and to go as unnoticed as possible. In that case, how does he go about it? Quite simply by hiding behind another computer program. Indeed, it is possible for the Trojan to be a legitimate app available in official app stores. It can be basically a calculator, photo editing software or even any other software that we are used to using. Once the application is installed on your smartphone, the malicious code executes and can allow hackers to perform several tasks. First of all, it is necessary to mention the fact that thanks to the Trojan it is possible, among other things, to spy on a person and collect this personal data. Personal data refers to any type of information including Outlook credentials. photo editing software or even any other software that we are used to using. Once the application is installed on your smartphone, the malicious code executes and can allow hackers to perform several tasks. First of all, it is necessary to mention the fact that thanks to the Trojan it is possible, among other things, to spy on a person and collect this personal data. Personal data refers to any type of information including Outlook credentials. photo editing software or even any other software that we are used to using. Once the application is installed on your smartphone, the malicious code executes and can allow hackers to perform several tasks. First of all, it is necessary to mention the fact that thanks to the Trojan it is possible, among other things, to spy on a person and collect this personal data. Personal data refers to any type of information including Outlook credentials. spy on a person and collect this personal data. Personal data refers to any type of information including Outlook credentials. spy on a person and collect this personal data. Personal data refers to any type of information including Outlook credentials.

Spyware is a must in the hacking industry. There are all kinds. Recently since the Pegasus case, this type of malicious program is particularly in the hot seat and attracts a lot of attention from people of all kinds. It is a way of explaining to you that, if you have the opportunity to use spyware, it is obvious that your computer attacks will succeed at 90%. Today you can even get lighter versions that are often used in a legal framework. These surveillance apps as they are commonly called are considered as malicious spying apps. It is also known pejoratively as Stalkerware. Spyware lets you know exactly what a person is doing on their computer terminal. It is possible to track the person and collect all the data of his internet traffic. In other words, we can know exactly how he managed to connect to his Outlook account.

Databases are the set of information compiled on a server. This information may be:
Either way, a database is very valuable to a cybercriminal. With this information and good tools, our hackers may be able to hack into accounts. Big Data is not something exceptional these days. With a database it is possible to initiate several types of hacking. The best known are the dictionary attack and password cracking, which will use automated methods to find the right passwords based on an already existing database. Thanks to databases, cybercriminals can also initiate massive phishing attacks. Most often, these databases are the result of massive data leaks. It may happen that hackers build databases on the exploitation of the scraping method. Finally, thanks to targeted and very discreet computer hacking, it is possible to have databases marketed on the Dark Web.

Surely everyone knows what phishing. It is a technique of impersonating an organization in order to deceive a user. The practice is to send a message that contains a link. This link leads to a bogus platform which is operated by cyber criminals. When the victim gets caught in the deception, imagine what happens? He gets his personal data stolen which could be used against him later. With spearphishing, things evolve differently. Indeed, the hacker will not send an email in a disorderly and poorly targeted manner. It will specifically target one individual. When he targets this individual, he makes sure to produce all the information necessary to obtain the trust of the latter. In this context, the message that the targeted person receives is so complete and well constituted that there is little chance that the latter does not fall into the trap. Once trust is established, it then asks its target to perform certain tasks. So many of these tasks are going to be to help the victim get hacked themselves. In the professional field, such a technique is known under the name of Compromised Business Email.

It doesn't matter what IT tool we use. It doesn't matter what software we used or are going to use. One thing is certain, it will be a computer tool that is affected by a 0 day flaw. There is in any computer tool, a security flaw which is not even discovered or which is not known by the manufacturer or the publisher. These security vulnerabilities can be exploited in order to undermine the integrity and security of the user. Today there is a mad rush to discover 0-day security flaws. These vulnerabilities, when properly exploited, can be used in a very sophisticated espionage context. This is why it has always been recommended to follow digital news in order to be informed of the latest news. We talk about it quite regularly on our blog, you will learn a lot about operating security vulnerabilities. Last year, it was mentioned by several specialists that the software named Pegasus, the famous spyware revealed to the general public by Forbidden Stories, exploited zero-day security flaws to spread and function properly. These vulnerabilities even allowed its operators to perform zero-click exploits. Zero-click exploits are the exploitation of zero-day security flaws with the aim of infecting a computer terminal without the target facing any manipulation or noticing. It is also for this reason that you should never neglect updates.
Beyond these hacking methods, it is important to think about protecting yourself. For this, some basic methods will help you improve your computer security. It is therefore time to ask ourselves if we have a healthy lifestyle when it comes to the use of computer software or devices. As a prelude, if you want to improve the security of your Outlook account, it is essential to activate two-factor authentication. This is one of the basics of security today. Almost all digital platforms offer this eventuality. This meets the needs of securing your account insofar as the password may be compromised. Speaking of the password, how to manage your login ID is also one of the bases of your protection. It is recommended,
This means that you should avoid using:
Today, it seems to be much safer to use sentences than compound words. For example, instead of choosing: " wrkdkzk381525 ", you can for example choose: " Jaimebienlesmangasdesannees2000 ". The second being much more difficult to decipher by conventional methods.
Also, do not click on the links you receive in your emails. In particular if you do not know the recipient or if you have not taken any action that could justify sending such a message. If you are still curious and want to know what is behind this link, it is best to go directly to your browser and enter the address of the website concerned.
To be sure that an email is legitimate, you have to look at its origin. If you click on " Reply " you will see the correspondent appear and thus his email. If his email is different from the signature of the message or if the domain name does not correspond to anything then you are sure that it is a compromised message. The only remaining solution is to place it in quarantines or even in spam and then delete it. You will be safe the next time this hacker tries to crack an Outlook email address. This prevention must be repeated as many times as an unwanted email arrives.
Moreover, whenever possible, please use anti-phishing software or firewalls that allow you to detect this type of message or email.
It is also important to think about protecting your connection. Therefore, here are some steps you should take before logging into your account:
There is also the possibility that despite all efforts, you are still the victim of a computer attack. Indeed, specifying it is important, you will not be able to protect yourself constantly.
Hacking into someone's Outlook account without their permission is illegal and violates privacy laws.
Yes, you can enhance the security of your Outlook account by enabling two-factor authentication, using strong and unique passwords, avoiding clicking on suspicious links or emails and regularly updating your software.
If you suspect unauthorized access to your Outlook account, immediately change your password, enable two-factor authentication and review your account activity for any suspicious behavior. You should also report the incident to Microsoft.
Yes, if you've forgotten your Outlook password, you can use official recovery methods provided by Microsoft, such as resetting your password through alternate email addresses or phone numbers associated with your account.
To protect yourself against phishing attacks aimed at stealing your Outlook credentials, always verify the sender's email address, avoid clicking on suspicious links and never provide sensitive information in response to unsolicited emails.
Using public WiFi networks to access sensitive accounts like Outlook is risky as these networks can be vulnerable to hackers. It's recommended to use a virtual private network (VPN) for added security when accessing your account over public WiFi.