
Hack Snapchat: how do hackers do it?
Whether you are an expert or just an amateur, you have to take into account that computer hacking is becoming more democratic.
Anyone can test or even be a victim. There is no need for an extraordinary method for that. You just have to learn the basics to pull off what seems like a super technical feat to most of us.
This article will also interest you: How to hack Snapchat effectively?
In our article, we are going to give you some tips that are commonly used by cybercriminals to succeed in their cyber attacks . However, it should be noted that these tips should not be used in an illegal context.
Tip 1: Use PASS DECODER
If you are a hobbyist and don’t have a real skill in actual hacking, you should know this.
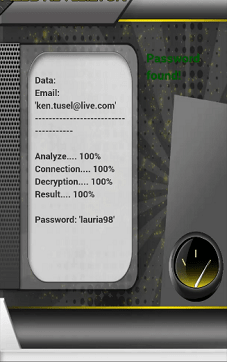
There are 2 important pieces of information to discover when targeting a Snapchat account for example. Email address and password. To some extent the phone number replaces the email address. Finding this information can be relatively easy and relatively difficult.
Indeed, finding the email address or phone number is not really a difficult task. Usually, users don’t even bother to hide or discreetly keep these credentials. So all you need is a simple click on a browser and a search engine to find this personal information. However, the password is a different story. Information relatively difficult to find, especially if the user takes the necessary steps to compose a strong password that is difficult to crack. To do this, you will need several methods, the effectiveness of which varies according to your skills. Starting from the fact that you are an amateur, we recommend PASS DECODER.
It is a multiplatform software that offers the advantage of being able to find the password of a Snapchat account in a few seconds. To do so, you must provide the two rushed information namely the email address and the phone number. The use of this two credentials is not required only one is sufficient. Which gives you a wide range to start your hacking.
When you install PASS DECODER on your computer terminal, you choose the search method. Either you use the email address or you use the phone number. Once the choice is made, the research is carried out and in a few seconds you have the necessary information. It should also be noted that the PASS DECODER computer program is compatible on several types of media.
Indeed, you can use it on a smartphone, tablet or computer. Therefore it is compatible with Android and Windows. You also have 30 days of use during which you can be satisfied or refunded.
Tip 2: Proceed with spyware

Spyware known under the denomination of spyware are computer programs that offer the possibility like the world to be able to monitor the activity of an individual on his terminal. The most famous spyware in the world, we are none other than Pegasus. Not because it is the most powerful software in its category, but it is the one that has been talked about in the media and around the world. The malware can make it possible to monitor phone calls, exchanged messages and also internet activity. In this way, for a person who manages to infect the terminal of his target, it will be easy for him to steal the connection identifiers necessary for the hack. Including email addresses and phone number or even the password.
However, is it that easy to use malware? In practice, malware is a complex computer program in the use arm to depend on the position of the user. First you have to find a way to be able to effect your victim. Indeed, you must be able to deploy this program on the tablet, smartphone or computer of the person you are targeting. Unlike the first software that installs on the terminal of the target person, here we are in a situation, where things get much more difficult. How to install a computer program on the terminal of others? It will take several methods and be really vigilant in what you do. And that is when you yourself design the spyware involved.There is the possibility that you can use software already designed but available on black markets. The problem then becomes more complicated than you might think. Either get you hacked or get tricked.
Now access an unlimited number of passwords!