Crack an Outlook password
To crack a password, hackers use techniques

Crack an Outlook password
To crack a password, hackers use techniques

In fact, it can be visible to everyone. Not in the sense that you believe, since when you type it there are hiding points that appear to hide it, but in the computer sense, the data is saved in a database. Theoretically it must be safe from hackers, but which is unfortunately possible to hack.
In fact, those who crack the Outlook passwords have discovered security vulnerabilities at Microsoft and can exploit them until it is corrected by an update. Sometimes, it takes years before they are discovered and hackers have already made good use of cracking lots of Outlook email addresses with their passwords.
Once a hacker has an interesting list of usernames and passwords, he will seek to get paid. For that, it will spam those emails with a link.
If the user clicks on it, he will either be redirected to a site selling drugs or to a virus. If the user downloads the virus, it will turn his computer into a zombie. This is used to do DDOS attacks. His computer will therefore be controlled by hackers wanting to harm a website.
But that's not all, he can also make him download ransomware that will ask the user to pay the sum of $300 to free his computer and all its content (documents, photos, videos...). Everything is good for making money quickly and without leaving your house!
Don't believe that pirates work in the shadows as you can see on television, they are most often sitting comfortably on their sofa drinking a beer.
Apart from these attacks, do you know of any others?
You should know that there are a multitude of possibilities. Lately, cybercriminals have been doubling their ardor and intelligence in order to find a way to break through your defense.
Here are some attacks you should know about that can target your Outlook account:
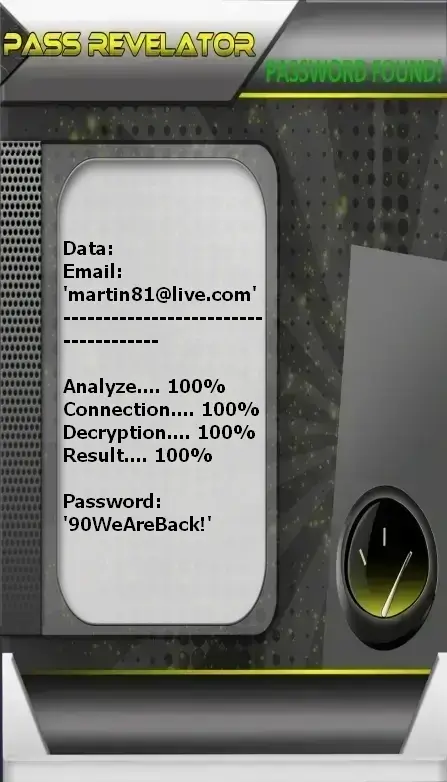
There is a well-known tool among cybersecurity experts: PASS REVELATOR. You may not have heard of it, but it’s a powerful solution designed to recover an Outlook account—even if it’s protected. PASS REVELATOR is a robust software created specifically to help victims of cybercrime. It’s not uncommon to be caught off guard by malicious actors. With this program, you no longer have to fear losing control of your Outlook account. In just a few minutes, it can help you regain access—even if a hacker beat you to it. Developed by cybersecurity specialists, it’s simple to use and perfectly suited for people with little to no technical expertise. Thanks to its cross-platform compatibility, you can run it on smartphones, tablets, and of course, computers. Best of all, you get a 30-day free trial as soon as you install it on your device. At the end of the trial period, you can fully refunded.
Download PASS REVELATOR from its official website: https://www.passwordrevelator.net/en/passrevelator

It is a variant of the famous phishing. As you probably know, phishing is a scourge of the Internet. It has been specially developed to steal users' personal data. In other words, if you lack vigilance and are not disciplined enough, there is a good chance that you yourself will help hackers to hack you. In the Spearphishing category, let's say it's a targeted phishing technique. In this context, the hacker will target a personparticular or a group of people. The message that will be sent to the target will be made up in such a way as to boost a lot of confidence. As is well known, we generally tend to click on the links present in the messages especially if they believe that this message comes from an acquaintance or perhaps from a professional manager. In such a situation, the cybercriminal takes advantage of the naivety of the individual and leads him to a bogus Outlook login platform. At this level, he will be asked to enter login information which will be retrieved by the cyber-malicious. Everything is done in such a way as to push the user himself to provide the elements that will allow him to be hacked.

We are here in the category of unknown techniques. Simjacking is a little used method, but dangerous enough to worry about. Because in one way or another, the user cannot really protect himself from it. Simjacking is a hacking technique that exploits a security flaw in the SIM cards we use. Indeed, most SIM cards in circulation have a lot of security flaws because they have not been updated since 2009. In addition to physical SIM cards, the e-SIM cardalso carries the same vulnerability problem. Thanks to the exploitation of its security vulnerabilities present in the SIM cards, the hacker can afford to steal a lot of personal information about his victims. Thanks to this information, it will be able to automatically attack your account and make you lose control of it.

The 0 Days are security vulnerabilities. These are not just any vulnerabilities, they are security flaws that have not even been discovered yet by the manufacturer or the software publishers themselves. Indeed, when setting up a computer program or making a physical tool available, there are always vulnerabilities that cannot be discovered at the time of programming. This context has highlighted what is now called the 0 Day. The fact that even the designer or the publisher is not informed of these vulnerabilities then raises the famous question of security. Indeed, it is not at all uncommon for hackers to seek to exploit these latest vulnerabilities in particular to carry outlarge computer attacks. And as there are always and anywhere, obviously the average user such as you is totally exposed. It is for this reason that it is strongly recommended to always perform the update as soon as possible. Because these updates offer the advantage of closing the 0 Day security vulnerabilities that managed to be discovered in time.
Here we are in a very common context. When cybercriminals do not want to use sophisticated methods then they will use software that allows them to make combinations of passwords as different as each other in order to break access to an account. Through automated scripts, they are able to try several thousand possible combinations in order to set the password you use to protect your account. So if you've made up your login ID in a fairly relaxed and uncomplicated way, just tell yourself it's a matter of time before they break it. As its name suggests, it is a brute force attack intended to destabilize all the security measures in place. There are variations to this technique to some extent. We speak in particular of the attack on the dictionary. It employs virtually the same methods as the brute force attack. That is, trying thousands of combinations using automated methods. Unlike the classic brute force attack, the dictionary attack will instead try to find the right password and relentlessly try a set of passwords or combinations collected and stored in a memory called a dictionary. This data used by the dictionary is either collected through several hacking methods such as phishing, scraping or quite simply through leaked databases.
As we mentioned above, the brute force attack and its variants such as password cracking or the dictionary attack are very common methods. It is for this reason that it is recommended to constitute a strong password, composed of symbols, numbers and letters. A phrase is also simple but effective for protecting passwords.
Here we have a very little known category of computer attack, DNS poisoning or DNS Cache Poisoning and Spoofing is a technique that consists of leading a user to a fake website where the hacker has total control. With such a definition, we will tend to confuse it with phishing, yet these are two totally different methods.
Everything happens from the ground up. Indeed, if, for example, a user enters his " gmail.com " search engine via his browser, because his objective is surely to consult his email box, insofar as this technique has already been put in place, this is no longer the " gmail.com " page that will be displayed, but rather a fake page. And this even if the user has entered the correct address on the browser. Unlike phishing where you have to click on a link, here it is from the browser that you the user is redirected. And even worse, it will be almost impossible to realize when you are on a fake hookup site.
As you have certainly understood, thanks to this technique, the hacker can very easily collect personal data and even connection and even financial information. The immediate consequences will be the hacking of your online accounts and even the misappropriation of your personal data.
Clearly, DNS poisoning is part of a larger hacking framework that calls itself the DNS attack or DNS Spoofing.
To succeed in their computer attack, cybercriminals make use of DNS caches. As known, DNS caches are mostly used to increase loading speed or to reduce loads on DNS servers. Essentially used to reduce bandwidth consumption or web server load relative to the tasks being performed. They are also used in order to improve the speed with which one can consult a website or use a browser. You should know that each time a DNS server is queried by a system, the latter actually receives a response. The information of this communication is then recorded in a local cache. The recorded data will serve as a reference for faster responses next time.
Knowing it was a routine on the web, it can happen that hackers compromise one of these caches. This is when we talk about DNS poisoning. And this regardless of the computer terminal used. Poisoning can start from the cache of a network router. This gives hackers the advantage of redirecting all connection requests. It is also possible for hackers to contaminate the caches that come from the very basis of our Internet use. That is to say the DNS servers which are managed by our Internet service providers. Which unfortunately makes the poisoning method much more dangerous.

In the IT threat category, social engineering is a must. It is a method that is common even if it often goes clearly unnoticed. In this practice, the hacker's objective is to play with his target. We are indeed in a context of pure and simple manipulation. The victim is a person who must be manipulated. In most of the time, social engineering and carried out on social networks. It can be done in a sublime and particular way or in a general way. The hacker will first forge links. Then take the opportunity to collect data that can be converted into login information. Be very careful when someone asks you questions that often seem innocuous. Mostly, do not communicate any code you receive by message to an unknown person or even a person you know. Indeed, it often happens that people call you and tell you that they have mistakenly sent a code by message to your number.Warning: this is not an error. Rather, it's a method used consciously to bypass your two-factor authentication. It is also used to change your account password. In other words, do not pass any code you receive by message to someone who asks you for it.

There is also talk of a computer attack that targets your SIM card. Unlike the Simjacking that we developed above, this technique does not seek to exploit a software security flaw. Instead, the cybercriminal seeks to use the vulnerabilities that reside in the way of managing the SIM cards as well as the telephone number. Somehow, the cybercriminal must have enough information about you to be able to impersonate you. Because this is the basis for performing this technique. When he has enough data to impersonate you, he calls your telephone company and puts forward the pretext of either having lost his mobile phone or pretending to have a problem with his SIM card. After verifying the identity, he then asked that your phone number be transferred to another SIM card that he will have under his control this time. Having your SIM card at his mercy, he can then initiate several types of computer attacks based on your phone number. It may even allow him tobypass two-factor authentication. Therefore, you have only one way to protect yourself from such an attack. You absolutely must avoid at all costs posting too much personal information about yourself via social networks. Try to be as restrictive as possible. Pay attention to the photos you post as well as your statuses or stories.
Beyond all this, we must always have another alternative insofar as all the measures we are deploying are not enough. Indeed, as we have mentioned several times, it is impossible to protect oneself absolutely. There is always a vulnerability, a security hole, a doorway that a cybercriminal can use against us. In other words, every time we connect to the Internet, there is a means that can be used against us. The various recommendations that we have made to you are not useless for all that. On the contrary, they will make it possible to reduce the possibilities for criminals by creating as many difficulties as possible. However, that may not be enough...
To crack Outlook passwords, hackers use various techniques including spearphishing, simjacking, vulnerability exploitation 0 Day, brute force attacks, DNS cache poisoning and spoofing, social engineering and SIM swapping.
To protect your Outlook account, it is recommended to use two-factor authentication, create strong and unique passwords for each account, regularly update your software, use antivirus programs and VPNs, avoid using public WiFi networks for sensitive tasks and be cautious of suspicious messages and requests.
If you suspect your Outlook account has been compromised, immediately change your password, review your account settings for any unauthorized changes, enable two-factor authentication if not already enabled and report any suspicious activity to Microsoft.
Yes, aside from the mentioned techniques, cybercriminals may also employ methods such as pass revelator, a form of software designed to access Outlook accounts and DNS cache poisoning, which redirects users to fake login pages.
To enhance your cybersecurity, it is important to stay informed about emerging threats, regularly update your software and devices, use reputable security tools, be cautious of sharing personal information online and educate yourself about common cyber attack tactics.