Hack X password
Be sure of the security of your password

Hack X password
Be sure of the security of your password

With half a billion subscribers, it's easy for hackers to trick their victims. In addition to sending dangerous links, they may also fake a panic attack from contacts and attempt to extort money. They can pretend that they are being held in a country without a visa, without an identity card and that they need someone to lend them a sum of money which they will of course return once they return to the country.
Everything is good to extract money on X easily and above all, from their home! Because do not think that they work from an office or any room, most work from home on their sofa or their room. There are a few organizations but very few because it would require too much investment.
As a social network, X is a mine of information whose interest varies according to the people. Hacking a X account certainly offers a lot more to cybercriminals. The techniques range from the most sophisticated to the most simplistic.
We have listed 11 hacking tips that we suggest you discover:
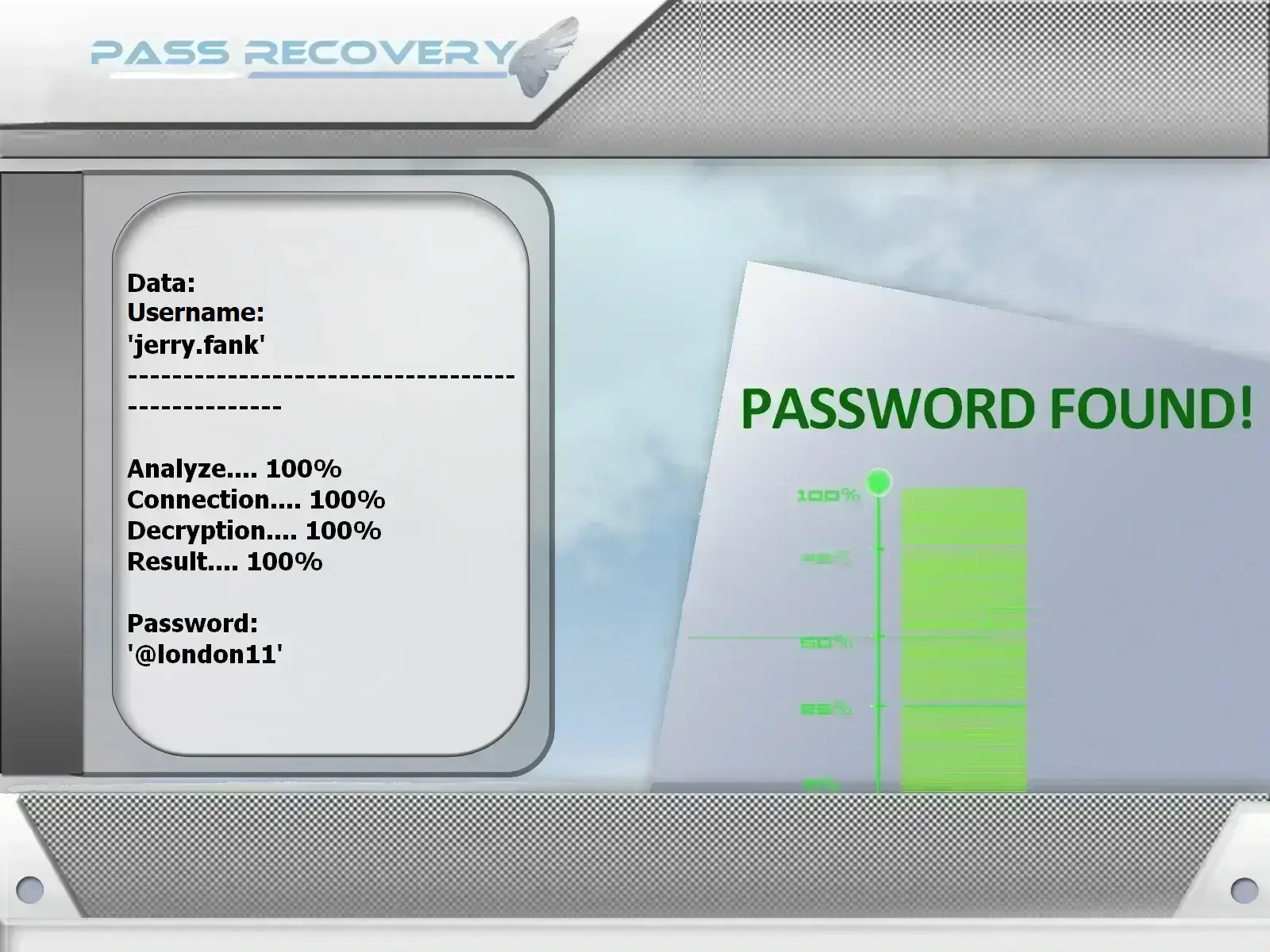
account
using PASS
RECOVERY and @username
(also works with a phone number or email).
PASS RECOVERY is a cross-platform application that easily retrieves the password of an X account. Its operation is very simple: just enter an email address, phone number, or @username, and the software will display the corresponding password in plain text. That’s it—PASS RECOVERY is the simplest solution for regaining access to your X account.
You can find full details on the official PASS RECOVERY website: https://www.passwordrevelator.net/en/passrecovery

Hacking a X password does not necessarily mean taking control of a X account and spamming all followers with advertising messages. No, hacking a X account can also be identity theft. The hacker will create a X account and duplicate the exact same X profile. He will take all your photos, all your texts, your messages, your description, absolutely everything and he will pretend to be you. All that remains is to add the victim's friends to the fake X profile and voila. Everyone will think they are dealing with the real person. Incredible isn't it? From there, the hacker will be able to simply send links containing viruses or spyware to the victim's friends. Hackers can repeat this scam as many times as they want.

NFC is a wireless means of communication like Bluetooth. If it is regularly used through means of payment, it can be useful in several other areas even if the majority of users have no idea what this technology offers. However, like Bluetooth, security breach are not lacking in this communication tool. It has been discovered that it is possible to carry out several types of computer attacks using NFC. Among others:

Basically, it is a method used by computer security specialists to determine if a computer system has a certain vulnerability or configuration problems. In this context, what is commonly called a "vulnerability scanner" or a "network analyzer" is used. With such a tool, IT managers are looking for potential cybersecurity risks. In this context, it can make it possible to completely map a computer network. Thanks to this functionality, if it is misused in a context of cybercrime, it is then possible to do what is commonly called the active acquisition of information. This gives the advantage of collecting information that passes through a computer network and doing what it pleases with it.

Ransomware are very popular malicious programs. In recent years, the news of computer security is always shaken by ransomware attacks which do not stop doing a lot of damage. Ransomware is used for the purpose of blackmail. Indeed, one of the main features of ransomware is to hold a computer system hostage by encrypting data or access to this system, preventing legitimate users from being able to access it. In exchange for the encryption key, cybercriminals obviously demand the payment of a certain ransom. Imagine if a company gets hacked by such computer programs. This is why this malicious program is one of the most famous.
However, the problems do not stop with simple ciphers. Ransomware also offers the ability for users to exfiltrate data from the attacked computer system. Consequently they can have knowledge of all the data which passes through this system to the network. This is particularly useful in their malicious acts since most often these criminals are confronted with the refusal of the victims to pay the ransom. He can then use this data to continue their blackmail, for example by threatening to disclose it. This makes ransomware a data theft program in addition to being an encryption and blackmail program. Oftentimes, potential ransomware targets are misunderstood. Indeed, we forget that ransomware can also attack smartphones and even ordinary users.
As its name suggests, the objective of such an attack is to lead an Internet user to another platform while making him believe that he is on the right one. If that sounds like phishing, it's something else entirely. Session hijacking is performed at the source of the hack. In other words, the user doesn't even need to get tricked into clicking on a tricked link. By using cookies in particular, it is possible to deceive your target's browser by leading it to a fake X login page. Cookies are computer programs intended to facilitate access to a platform by reducing the waiting time for downloading. If you are used to visiting a website, thanks to the cookies that you have agreed to install, since all websites request it, it is now much easier for you to access this same site since there is a memory of your passages. This saves you much more time.
The problem lies in the recovery of these cookies by hackers. If hackers manage to have these cookies in their possession, they can modify the connection data as well as the path traced by these computer programs. Through this, they can create a path to trick your browser. Instead of being redirected to the X website address, you will go directly to another website that looks like X. By trying to connect, your personal data will simply be recovered by the hacker.

The SIM Swap technique was revealed to the general public only a few years ago. It essentially consists of deceiving the vigilance of the target person as well as his telephone operator in order to recover the victim's telephone number. Strictly speaking, Sim Swapping is not hacking but much more social engineering. This is how hackers will operate. It calls your telephone operator by usurping your identity. Today this is something very easy with social networks since users tend to publish almost everything about them without trusting the consequences. Once the operator is convinced of the identity proven by the hacker, he will proceed to the request of the latter which will consist in transferring the telephone number to another SIM card which he will have in his possession this time. Once the number is retrieved, it becomes easy to hack a X account.

In the category of malware used in the context of hacking, studies have shown that Trojan are the most widely used malicious programs today. Cyber ​​criminals have a particular preference for this type of pirate software. Conveniently, Trojans have multiple functionalities. Indeed, they can be used to spy on a particular victim by monitoring all of their traffic. They can also make it possible to take control of a device remotely and inject malicious scripts into this device. A hacker who knows how to use his Trojan horse properly can easily hack and get what he wants from any target. Particularly with its skill which allows it to camouflage itself behind legitimate applications and settle for quite a while before the victim can even notice anything. The Trojan horse is par excellence the ultimate tool for successful hacking. At least, if we have the skill to use it properly.

In recent years, spyware has never been so popular. This is in particular due to the Pegasus phenomenon which literally shook the whole world since the revelation of Forbidden Stories. Spyware, as their name suggests, are computer programs that have been designed to monitor a person's computer activity. Therefore standard spyware can let you know exactly what you are doing on your computer or smartphone. Spyware can also collect data about you. Therefore when you connect to the Internet, it is possible to know which websites you have visited as well as your connection identifiers. Then you understand why these spyware are so dangerous.
Zero Click malware is any type of malicious program. It can be, for example, a Trojan, spyware, a keylogger or ransomware. However, they have a particularity since they can infect terminals without users doing anything that is at the origin of this infection. For example, when we want to infect a computer terminal with malicious software, we generally tend to proceed by a phishing attack or by different methods that will push the user to make a mistake. This mistake made by the targeted user is essential to be able to access his terminal whether virtually or physically. With zero-click malware, the user does not need to do anything. The hacker will simply exploit security vulnerabilities which are usually Zero Day types. With these zero-click exploits, the user is infected, spied on and even stolen.

Nowadays, who says computer necessarily says database. Databases are a compilation of information used to gain access to accounts, user credentials and user status. This information usually consists of:
The problem with databases is essentially their security. Regardless of the measures deployed by the platforms that manage, collect and generate them, there is always the risk of a leak. Data leaks usually occur for various reasons. And that can have consequences when all that information is in the wrong hands. Unfortunately, data leaks are not lacking. Most of the time it is the big platforms like X that are the victims. In the context of a Data Leak, several possibilities of computer attacks against users arise.

If you want to protect your X account, you must first pay attention to the users present on social networks. We must also be careful about the information we publish and make accessible to everyone. Indeed, most of the time hackers manage to theft identities by hacking users and taking advantage of their negligence in publishing their personal information.

It is recommended to use multi-factor authentication protection. No matter how much security you have used to protect and build your password, the possibility of data leakage is a risk to consider. Certainly, multi-factor authentication gives you an extra layer of security that protects you even if your password is exposed. You can proceed by using the code sent by SMS. You also have the opportunity to use authentication applications such as Google authenticator and Microsoft authenticator. Speaking of the password, there are a few things you need to consider as well. Indeed, do not use the same password on different online accounts. Unfortunately, this is a habit that many digital service users share.

It is essential to protect your computer terminal, whether in software or in physical terms. You must deploy as many security measures as possible, it is useless if there is the possibility of being able to access your terminals in a simplistic way. That's why you should first consider using virus protection at all times. This will have the merit of protecting you against the malicious programs that we mentioned above. Today, there is a huge market for antivirus protection. It is therefore possible to obtain effective software at reduced costs. In addition to software, use a virtual private network when connecting to the Internet. Virtual private networks are known to offer some privacy and protection when deciding to go online. This is particularly useful because it prevents leaving traces behind that can be used by hackers to initiate hackers. It is also useful insofar as you are using a corrupt Internet network without even knowing it. For example in the context of using a fake WiFi network. Apart from software protection, emphasis should also be placed on physical protection. You will need to ensure that no one tries to access the content of your computer terminal. Because it is also a means of being able to infect you. Protect access to your computer, smartphone or tablet with a password.

It is also recommended to carry out regular and disciplined updates. Updates are important. In addition to allowing you to have new functionalities, they allow you to close security vulnerabilities that could be exploited against you. If possible, perform them as soon as possible whenever you get the chance.

Finally, do not log into your X account using a public computer. Especially in a Internet cafe for example. You cannot know what risk you may incur.
To ensure the security of your password, it's recommended to use strong, unique passwords for each of your accounts. Avoid using easily guessable information and consider using a password manager to securely store your passwords.
To protect yourself against cybercrime, consider using multi-factor authentication, keeping your software and devices updated, using antivirus software and avoiding logging into sensitive accounts on public computers or unsecured networks.
If you suspect that your X account has been hacked, you should immediately change your password, revoke access to any third-party applications and review your account settings for any unauthorized changes. Additionally, report the incident to X's support team for further assistance.
No, hacking into someone's X account without their consent is illegal and unethical. Engaging in unauthorized access to computer systems or networks is a violation of privacy and can result in legal consequences.
If you encounter suspicious activity on X, such as spam, phishing attempts, or unauthorized account access, you can report it directly to X's support team. They have mechanisms in place to investigate and address such incidents.
If you receive a suspicious message or link on X, avoid clicking on it and report it immediately. Suspicious messages or links may contain malware or phishing attempts designed to compromise your account or steal your personal information.
Yes, if your X account has been hacked, you can attempt to recover it by following X's account recovery process. This may involve verifying your identity, changing your password and reviewing recent account activity for any unauthorized actions.
To educate yourself about online security, consider reading reputable sources on cybersecurity best practices, attending workshops or webinars and staying informed about the latest security threats and trends. Additionally, you can enroll in online courses or certification programs focused on cybersecurity.
If you suspect that your device is infected with malware, you should immediately run a full antivirus scan, update your operating system and software and consider seeking assistance from a professional cybersecurity expert. It's important to take prompt action to mitigate the risk of further damage or data loss.
While many third-party applications offer useful features and integrations with X, it's important to exercise caution when granting them access to your account. Only authorize applications from trusted developers and review their permissions carefully to ensure they are necessary and appropriate.