PASS RECOVERY is the legitimate and certified ISO 9001:2015 & ISO/IEC 27001:2022 AI-powered application that allows you to hack the password of an X social media account, even if they are complex and log in.
Without PASS RECOVERY, you’ll never be able to access it! Imagine being able to decrypt an X account and connect now without restrictions.
Take advantage of this simple trick—you’ll be amazed by the results! You only need the @username, phone number, or email address for PASS RECOVERY to extract the requested X password in just a few minutes, even if the account is private or old, giving you full access.
PASS RECOVERY simplifies the process of breaking passwords by integrating an advanced artificial intelligence algorithm. It uses a powerful system for real-time data interception and analysis, combined with a sophisticated script-based process for deep cryptographic decryption. Once the password is identified, the next step involves processing protected database storage to obtain accurate and efficient results, the access code is placed in the broadcast variable. This allows the X password to be displayed in plain text on your screen, enabling you to log in anonymously in just a few minutes.
PASS RECOVERY’s sophisticated method does not generate any X alert notifications throughout the process.
![]() WARNING: Do not use this application on accounts other than your own. Review the terms of use.
WARNING: Do not use this application on accounts other than your own. Review the terms of use.





TRY IT NOW!You don’t need any experience to get started... PASS RECOVERY was developed to bypass security and easily regain access to X accounts—that’s exactly why we created it! To get started, simply follow these 3 steps:
Have doubts or questions? Contact us without hesitation or try it now with a 30-day money-back guarantee! We’re confident in our application’s effectiveness, which is why we guarantee access or we’ll issue a full refund. Start NOW and instantly access passwords Frequently Asked QuestionsWho can use PASS RECOVERY?Anyone who has lost access to their X account can use PASS RECOVERY to recover their password. How many passwords can PASS RECOVERY hack?PASS RECOVERY can find an unlimited number of X passwords. How long does it take to get results?Results are typically obtained within just a few minutes after providing the required information to PASS RECOVERY. It can recover passwords from all X accounts—private, personal, or professional. Is the security of recovered passwords guaranteed?Yes, with PASS RECOVERY, the security of recovered passwords is ensured. No data is stored to protect user integrity. Is using PASS RECOVERY confidential?Yes, PASS RECOVERY does not require account creation or any personal details to operate. All data is cleared when the app closes. Can I use PASS RECOVERY in my country?Yes, PASS RECOVERY is designed to work worldwide, ensuring users in all countries can access its services. Is there a trial period for PASS RECOVERY?Yes, we offer a 30-day trial with a money-back guarantee if it doesn’t work. Feel free to contact us for an immediate refund. Does it require a monthly subscription?No, PASS RECOVERY is available as a one-time purchase with no monthly subscription required. How long does it take to receive it after payment?Download is immediate after payment. There is no waiting time required to start using the application. Is PASS RECOVERY secure?PASS RECOVERY is secure in its use since no external information is communicated. Is it legal to use PASS RECOVERY?Using PASS RECOVERY to access accounts other than your own is completely illegal and may result in criminal prosecution. We encourage you to use the application in compliance with the laws of your country. |
Enjoy unlimited, commitment-free access! Do not use this application on accounts other than your own, as this is entirely illegal and may lead to criminal prosecution. The best experience is achieved on your own account while complying with your country’s laws.
Instantly access any X account. This application was developed to help people who have lost their X account password recover it. In other words, it extracts the account password and displays it on your screen. Money-back guarantee!
X has more than 206 millions of users and 500 million tweets per day. It’s an opportunity for hackers to crack X passwords. With X, you can easily reach the thousands of followers even millions! But are you aware that your X account’s value is more than your credit card information?
There are several reasons why hackers target X passwords:
You have to be careful and to hurry up because your contacts could be in danger if someone hacked your X profile. You must recover your lost password now using PASS RECOVERY!
There is always a feeling of insecurity when we connect to a X account. A feeling that when we try to connect and when we enter the password, someone can spy at that moment and discover our password. It is very important to protect yourself against hackers.
You can try to hide your password like you currently do with a credit card but it could be a little different with a phone or a computer. Protecting your private life is a priority that should not be neglected. The consequences afterwards can be disastrous. But you have to keep in mind that no password is uncrackable.
After much hard work, we have finally found out a way hackers can get it. Several of you are probably wondering how it is possible to accomplish this formidable operation with this program.
It is at least worth a try. No need to pay and no survey. If not we have to go to other alternative options available to those we got. If you use the internet, then you have heard of X. It is the largest social network platform in the world. You have also probably heard that it is the most unsecured platform in the world. You are probably wondering, how does a company that facilitates so many users consistently, allow itself to be forced so often. You would be surprised at just how easy it is to enter in a personal X account profile.
With online software programs such as X Password Hack, it is simple. You can log into the site, follow the simple instructions and within 2 minutes you can be inside anyone's account. Get ready to have access to the best online X hacking software available. When you have the feeling that you are cheated by someone, a network service is the only way to know the truth. First thing to do is to make sure that you get the best tool for the X messenger. Try it also on phone or tablet.
Now, these methods we have listed below are only for specialist and computer expert. To initiate attacks, the hacker begins by decrypting the password of an account and then proceeds to change the @username, the password and the contents of it. Thus, the victim is no longer able to regain possession of his or her digital identity. The pirate will then use the account as he sees fit. Hacking can also be ethical, some do it to thwart the protections of a computer system not for criminal purposes, but to improve it and make it safer, therefore less permeable to fraudulent attempts by hackers.

The most widespread hacking technique is phishing: the user receives an email from X in which he is asked to provide his credentials to prevent his account from being suspended. Another technique, the scam, is to create a relationship with the target through the exchanges via instant messaging, then abuse his trust by causing him to reveal his X password and login.
The FBI has issued an official warning against extortion by hackers who blackmail X users. The perpetrators demand ransom from the victims and in case of refusal they threaten to publish their illegally obtained personal data.
As soon as possible criminals ask to make a transfer to an anonymous account in bitcoins. The Bureau quotes messages sent by hackers. In most cases, the messages are almost identical. The criminals threatened to send "dirty information" to friends and relatives of the users if they refused to pay.

The founder of X, Jack Dorsey, was hacked! His X account was exposed and the hackers had fun with it. They used a formidable hacking technique: SIM Swapping. This hacking uses a fairly complex operating method to allow hackers to transfer the victim's cell phone number to their own phone. In summary, hackers will pretend to be the victim they want to hack to get around 2FA and take control of the X account.
If unfortunately you are the victim of the hacking of a X account, you must log in to your e-mail as soon as possible and change your password, to prevent the hacker from logging in again. If he has preceded you and your password has already been changed, then contact your email provider, to report the piracy of your account. This is a complicated operation (how can the operator know that you are really the owner of the account?).

One of the most common techniques for hacking X accounts is doing social engineering, which is essentially a process of collecting information about someone whose account is going to be hacked. The information may be his date of birth, his cell number, his nickname, his name, his place of birth, etc.
Obtaining such information from those involved may allow us to hack into their account. X is not an exception to provide a security issue as a PASS RECOVERY option. So, if someone comes to know the answer, he will be able to hack the account using the forgotten password option or try your weak passwords.
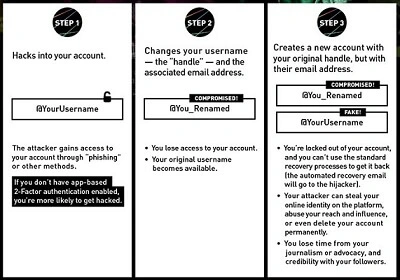
"DoubleSwitch", this type of attack is mainly organized to destabilize the political activity of a country. DoubleSwitch involves hacking a user's X account to impersonate the user. Extremely dangerous, the attack allows malicious people to influence the population by conveying false or incomplete information.
This practice has become commonplace over the past few years and is used mainly to destabilize countries. To organize and transmit information alternatives to the one that the power disseminates, the political opponents very regularly appeal to the social networks. According to information provided by security expert, this online political movement is the victim of the malicious acts of several hackers. It is mainly the identities of journalists and activists or those travelling in the country that are usurped by hackers.

The hacking of X accounts is very easy, in fact, hackers have specialized in collecting accounts to launch DDoS attacks of a new kind. Your account has been restricted following a normal activity! This is the type of message that X can show you in administering your micro blogging space. Pattern? Too many retweets, too much "I like" in a few minutes. Your fans have become too "in love"? There is a good chance that a hacker has used the DDoS X method. The idea for the malicious malware, to get hold of the hundreds, thousands of old X accounts? How? Simple or almost. Phishing or passwords worthy of a student. The benefit of accounts, they are old but still present on X. The hacker did not need to create malicious allies that will require further authentication through X, such as a phone number.
An old account has already been authenticated, by its legitimate author. Any benefit for the pirate. The latter has only to set up a bat that launches its attack from the infiltrated X accounts. The attacked account can no longer communicate. Particularly disruptive in times of crisis or in the context of institutional communication. You know, several attacks were recorded. Botsets make and deploy spams to manipulate, but it remains difficult for X to keep track of it. The accounts of pretty young women are not the only ones to make retweets.
But this concerns the "new" enemies. For the old ones, it is much more complicated. In his blog, X says that "robots can be a positive and essential tool, from customer support to public safety, plus we strictly prohibit the use of bots and other manipulation networks to impair the essential functionality of our service". X confirms having doubled its teams and resources and creating new tools and processes. It is possible to process all the X password hacked. To protect yourself, use a unique password that is complicated enough not to be found by a tool or by social engineering.
As you may know, X is a massive platform for several attacks and some have been recorded on X recently. They are mainly targets of activists, but also political opponents and journalists. Hacking, cyberattack, phishing, hacking networks: between computers and smartphones, digital is everywhere and computer security has become a major issue in the midst of an unlimited cyberwar.
That's why, in any case, it is better to be safe than sorry: if your password has only 6 or 8 characters or it is too easy to guess/crack, start by modifying it, taking care to choose one that will give a hard time to the many hackers (and their robots) who roam the web!
Private data, sensitive sites of companies or governments, credit cards, passwords: if data theft feeds films and newspapers, there are some who are doing this legally and are much less known from the general public.

If you have a X account, like many other social media accounts, it is certainly important to take steps to increase its security. This is important as we see more and more computer attacks targeting users of different social networks. It is for this reason that we have planned to give you some tips on how you can keep your X account as secure as possible.

This is the first piece of advice we can give you about protecting your account. The password is very important, it is the first barrier that opposes a hacker or anyone with bad intentions who wants to access your account without your knowledge.
To do this, you must first know how to set up a good password. This is because the password should be formulated in such a way that classic password cracking methods cannot work so easily. It is for this reason that it is more than recommended to constitute a password of 8 to 10 characters. Then, it should be composed of upper and lower case letters, numbers and if possible special characters.
You should avoid formulating passwords based on well-known credentials. We must put an end to "1111111111111", expressions such as "password" or "password", cybercriminals already know the trick. In addition, it is also excluded to use dates of birth or the names of relatives. In addition, the main recommendation is not to use the same password for your X account on other web platforms.
Finally, if you doubt or think that your password has been compromised, immediately reset it. There is indeed a dedicated parameter for this purpose:
In the wake of password protection of the account, it is strongly recommended that you use multi-factor authentication. It doesn't matter how complex your password is.
Account Login
Log in to your X account.
Go to the security settings or the account settings.
Look for the “Two-Factor Authentication” or “2FA” option.
Choose a primary factor, typically:
Authentication app (Google Authenticator, Authy, Microsoft Authenticator)
SMS (less recommended)
You are not immune from a data breach or handling error on your part. In addition, hackers continue to develop new methods of hacking more or less effective. Multi-factor authentication then becomes an additional layer of security. It also helps protect you from phishing. Especially in a context where X is one of those platforms most visited by large-scale phishing operators. Double factor authentication will double confirm your identity to be completely secure. The advantage is that the social network X offers it in its parameters. Therefore, do not hesitate and activate it.

Like most social networks, X offers connection alerts that notify the user when a new connection has been detected from a new device. Therefore, it is clear that if you are careful, you will be able to anticipate cases of account theft. These alerts can also warn you in the event of an update of your email address. Which is an extra layer of protection.

Phishing, is a very common practice on the Internet. Almost all users have been the victim of a phishing attempt or similar. Therefore, it is the most persistent threat to which you will be most exposed. You need to be comfortable with this situation. Be wary when you receive private messages or even downloadable attachments. To this end, X warns you:
"We will never ask you to download something or sign-in to a non-X website. Never open an attachment or install any software from an email that claims to be from us; it's not.
If we suspect your account has been phished or hacked, we may reset your password to prevent the hacker from misusing your account. In this case, we'll email you a X.com password reset link.".
You must be extremely vigilant and always on your guard.
Whether it is your browser or the X application, before using it you must be sure that you have deployed the most recent update available. Your overall security depends on it.
You may be a victim of computer hacking and you want to get your account back. The PASS RECOVERY application that can let you recover your X account in a matter of minutes. Thanks to your email address or the phone number associated with your account, it allows you to find the password in a few minutes.
Yair Wahal, Marketing Director, Zingali Acustics