Hack a GMail account
Hackers have access to all your messages

Hack a GMail account
Hackers have access to all your messages

The figure is chilling, but Google recently claimed that more than 250,000 passwords are hacked every week! It can happen to anyone and anytime. The company Google, which manages GMail, nevertheless tries by all means to protect its customers' accounts by always innovating new functionalities, but this is never enough in the face of hackers.
To crack a GMail email, they use several possibilities, bruteforce solutions, IP address simulators with a VPN server, spoofing a mobile number, etc… the list is very long and Google will always have a behind in the face of these little computer geniuses.
There is no solution to avoid hacking GMail, caution is the most useful technique in this case. An email that seems strange to you? Put it straight in the trash! It's like a call that you receive, if the person really wants to reach you, either they leave a message or they call back. If you delete a legitimate email that you thought was dangerous, then the person will try to contact you again or even call you if they have your phone number.
A cracked GMail password can be hacked again, anything directly or indirectly related to computers can be hacked, even a second time. Flaws exist and they will always exist, even if the team fixes them. The proof is that Google itself says in a press release that it is impossible to secure 100% an account with its contacts. It is for this reason that it is recommended to make regular backups of all messages and contacts. A good antivirus or firewall won't do you any good, the best protection is yourself!
Just ask yourself the question of how hackers manage to attack your GMail account. It would seem that the techniques diverge and are several. In this case we will describe some quite popular ones:

account using PASS BREAKER.
The simplest solution to access a GMail account is to use PASS BREAKER. This application allows you to hack a GMail password using only an email address.
It’s a tool that enables you to retrieve any GMail account password in record time. With this application, you can be confident in your ability to decrypt a GMail account if you’re ever caught off guard by cybercriminals—an unfortunate but very real possibility that should never be ignored.
PASS BREAKER was developed by cybersecurity professionals and is reliable enough to assist you effectively. You don’t need to be a tech expert to use it.
Additionally, you get a 30-day trial period. At the end of this trial, either it works, or you get your money back.
To get started, please visit the official PASS BREAKER website: https://www.passwordrevelator.net/en/passbreaker
Known as the Man in the Middle Attack, this attack is a cybercrime practice that will consist for a person with bad intentions to physically or digitally install a system that will allow him to control the exchanges between the person who targeted and the digital resource with which the latter wants to correspond. The objective of this attack is obvious: listen to the conversation, monitor and manipulate the victim's communication with his terminal or with digital resources.
In effect, the man-in-the-middle attack will allow the hacker to intercept data traffic without the knowledge of both parties so that they believe they are only communicating with each other. Basically, the method was used on the manipulation of the physical communication channel. With the explosion of communication techniques and the cycle of public networks, not to mention the increasing digitization of exchanges with the Internet, it was obviously much easier to intercept exchanges as in the case of the man-in-the-middle attack. It essentially relies on an SSL/TLS decryption hijacking method. This allows hackers to access private or even very confidential information. It can then be a password for your GMail account, for example, login credentials for banking or professional applications. Financial information etc.
The most commonly used pattern for performing a man-in-the-middle attack is as follows:
To know how to protect yourself against this computer threat, which is quite sophisticated it must be admitted, it is generally advisable to use a virtual private network for your Internet connection.
Browsers today offer a lot of extensions that are often designed by private publishers. The objective of extensions is to facilitate the use of a web service through the browser so that it works like an application for example. The problem is that just like the classic applications we know, there are also malicious extensions that have been designed typically to hijack your personal data. Thanks to these kinds of tools, you can be sure that your GMail account is not safe. This is why it is generally recommended to get rid of all extensions that are not necessary in the first place.
We are talking here about a method that is quite recent. Indeed, until 2018 it was literally a practice that had not been mentioned in textbooks or in the categorization of hacking. Which makes it quite difficult to better understand how criminals could still exploit it. What we can say with certainty is that it is a technique that doesn't require you to be very efficient in hacking. Especially since it is very difficult to protect oneself from it. To succeed in this practice, you just need to have certain information about your target, such as the telephone operator that the victim uses.
" SIM Swapping ", in other cases " SIM Swap ", or " SIM Swap " is a hack that will involve smartphones and certain online procedures. It is heavily used to circumvent the identification measures imposed by certain web platforms such as GMail or even e-commerce sites and banks. It is the tool par excellence that allows the hijacking of the identification codes that the user most often receives by SMS to confirm his identity. With this method the two-factor authentication by SMS becomes ineffective. It is even said to be one of the most common hacking techniques in France.
In carrying out the SIM Swap, the hacker finds a way to hijack his target's phone number. He can for example call the telephone operator at the target and claims to have lost his smartphone, for example, he requests a relocation of his telephone number to another chip. Once successful, he can thus receive all the SMS and calls which are in principle intended for his victim. This also includes the authentication code. Your accounts are at his mercy. Obviously to succeed in this, the hacker must have enough personal information about his target to deceive the vigilance of telephone operators. Something that is no longer difficult enough with social networks and the tendency of users to talk too much about themselves and their private lives. It is also for this reason that we most often advise you not to publish too many.
Cybercriminals know that you like to connect WiFi especially when access is open to the public. They also know that you don't take the utmost care to protect yourself directly when accessing the Internet. In France, the use of fake WiFi hotspots is quite common. Millions of users are trapped by this technique almost every day. This is simply to create a fake WiFi Hotspot with the name of another that we certainly know. It could be for example the name of the WiFi of your place of work or for example that of your entourage or your favorite restaurant. If you are used to connecting to it without paying attention to certain details, it is possible that the fake WiFi network with a name you are familiar with is bound to trick you. And do you know what happens when you use this kind of fake WiFi? Your personal information, your login credentials and all your Internet traffic can be monitored and hijacked... Here we are in another variant of the man-in-the-middle attack. It is also a threat to be taken very seriously because anyone can be caught in the process. It is therefore wise for users to be wary of the WiFi networks they connect to. They must be able to protect themselves with anti-virus software as they may be exposed to cyber threats.

Vulnerabilities exist everywhere. Every time you use a computer device, every time you use a website or a web platform, you have to be sure of one thing, there is always a security flaw that can be used against you. And that is what is commonly done by hackers. Just be aware that there is a vulnerability market where security vulnerabilities that can be used against you are marketed or given away for free. If it is a category 0 day security breach, it is difficult to protect yourself from this because the builder or publisher of the application you are using is not itself informed yet. For this reason, as soon as you learn that an update is available, do not hesitate and run it as soon as possible.

Session hijacking is a practice that falls within the larger group of Hijacking. It is very similar to the man-in-the-middle attack. It is also called Session Hijacking. As its name suggests, it is generally used to exert the communication of an Internet user with the aim of determining his session towards a much more malicious use. This essentially involves stealing cookies. If you have cookies that are useless, go to your browser and delete them.
The Trojan horse is a rather tricky malicious program when one is often targeted. Indeed, thanks to the array of features it can offer its operator, three horse victims are usually at great risk. So to speak, if you are infected with a Trojan horse, the hacking initiated against you has almost every chance of succeeding. The Trojan horse is an application that looks like a legitimate program. In some measure, it is itself a legit application that hides malicious script. Therefore, it is not uncommon for the user to install it himself on his computer terminal. You should know that, as soon as your computer or your smartphone is infected by a Trojan horse, the operator can take remote control of this computer terminal. He can tooremotely install a malicious script that allows you to do many other things. For example, harvesting your personal data, initiating actions remotely with your device and even spying on you. In short, let's say it's the total. So make sure you always have your antivirus software up to date and permanently activated.

In this period when Big Data and artificial intelligence are in full development, you should know quite simply that a few pieces of information are enough for specialists to be able to find your login credentials. It is this logic that is used by those who practice Scraping. From the moment we have a quantity of data at our disposal, it is obvious that with the expertise and the tools at our disposal, the hacking of any online account is possible. With Data Leaks, cybercriminals today have huge databases where most of your personal information is likely to be found. These databases are often available free of charge, or for a fee from the person who will use them. In all measures this is accessible.

We can't talk about GMail account hacking technique and exclude keylogger. Keylogger in English is a popular computer program, which gives the opportunity to its user to be able to hack an account with the help of the victim himself. How is this possible you say? Well know that as its name suggests, the keylogger can record everything that a person typed on the keyboard of his computer. This means that the hacker can very easily crack your login information and hack into your GMail account with ease.

It is an ultra-targeted variant of phishing / phishing. It essentially consists of targeting a particular person in a particular way (unlike classic phishing which can be sent randomly). It will simply consist of sending an email which has a very convincing character to its victim. This email that is received by the victim is unique. It is written to be as convincing as possible. For this, the hacker will collect as much information as possible about his victim. We speak in particular of his personality, his geographical address, his place of work or his work simply and as well as some information on the name and his entourage. Of course, this is information that can be collected directly on social networks. The goal is to trick the victim into being as confident as possible by making them believe that the email is legitimate and reliable. However, in each fraudulent email that will be sent to the target, there will be contained an image that is supposed to alert the hacker each time the victim has opened the email in question and clicked on the link that was tricked. Thanks to this device, it is of course possible to track the person in a coordinated way and as and when. And this thanks to a connection page which is fake, thus making it possible to recover the connection identifiers of the hacked person. The question you are probably asking yourself is whether this technique can help bypass two-factor authentication?
The answer is yes. Indeed, by leading the targeted user to a fake login page, they will also provide for the eventuality where he will be asked to give the temporary identification code he received by email. Of course, the targeted user will believe that he is on the official website and he will provide the temporary code which will be immediately recovered by the cybercriminal. Once this information is retrieved, you automatically lose control of your GMail account. A simple, precise and very dangerous technique.
Protecting your Gmail account is essential for safeguarding your personal information, email communications, and connected Google services. Follow this comprehensive 15-step security guide to maximize Gmail account protection and prevent unauthorized access.
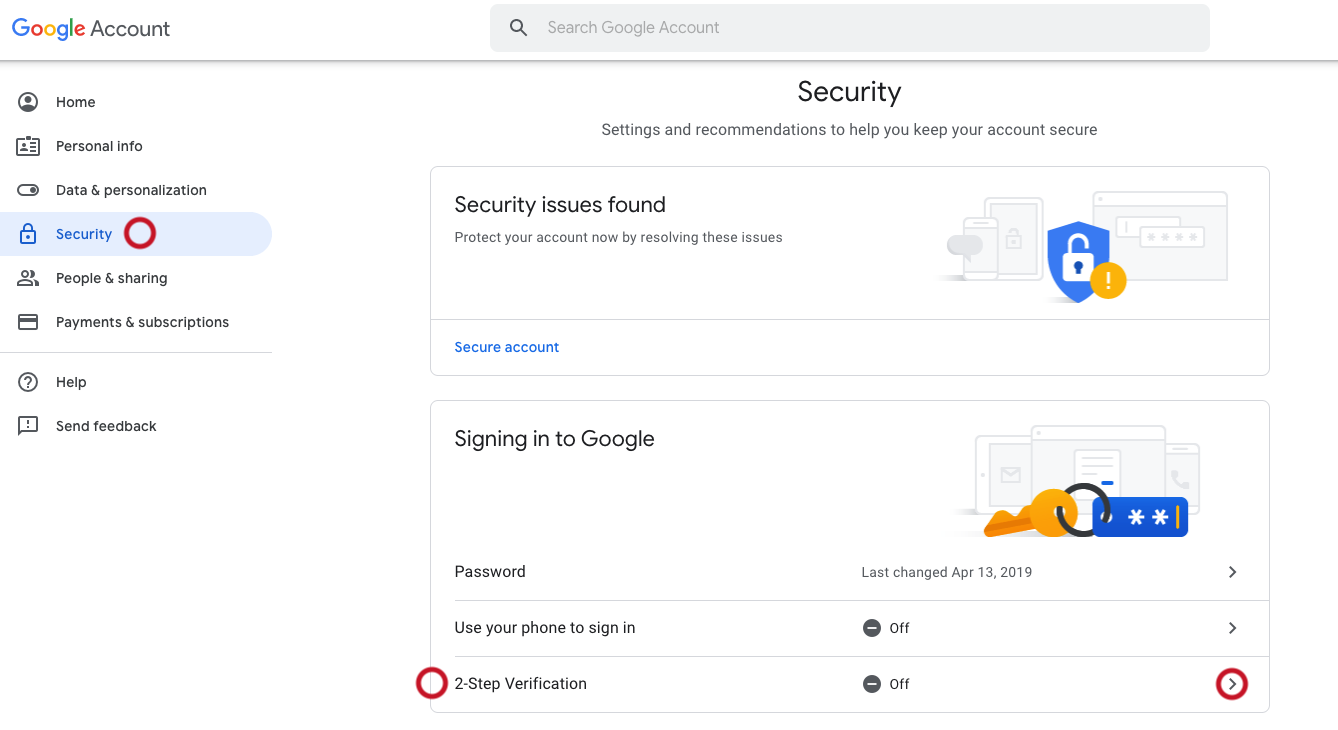
Two-factor authentication adds a critical second layer of security to your Gmail login, requiring both your password and a verification code.

Protect your devices from malware, keyloggers, and credential stealers that target Gmail accounts:
Browser extensions can compromise Gmail security—install only from official sources and review regularly:
Essential for protecting Gmail on public WiFi networks—encrypts all internet traffic:
Implementing these 12 security steps significantly reduces your risk of Gmail account compromise and protects your digital identity against evolving cyber threats.
For users who need to recover access to their own Gmail accounts, password recovery tools can provide legitimate assistance in regaining control of your Google account.
To protect your GMail account, it's essential to stay cautious and follow best practices such as:
While two-factor authentication adds an extra layer of security, some sophisticated hacking techniques, such as spear phishing, can bypass it. It's essential to remain vigilant and combine two-factor authentication with other security measures for comprehensive protection.
If you suspect unauthorized access to your GMail account, take immediate action:
Attempting to hack into someone's GMail account without authorization is illegal and can lead to severe legal consequences, including fines and imprisonment. It's important to respect privacy and adhere to ethical guidelines when dealing with online security.