Hack a Yahoo password!
Yahoo has too many big security fails

Hack a Yahoo password!
Yahoo has too many big security fails

The Yahoo! you use for your business is one of the most valuable digital assets you have. Indeed, having your email hacked would be a disaster, your email is the equivalent of your phone to communicate.
Hackers and cybercriminals make constant efforts to create a whole host of traps to steal your Yahoo!. It is very important to outsource your accounts and have a separate contact book not associated with the email address you are using in order to prevent the spread if one day the hack were to happen.
But if you have had your Yahoo!, do not worry, there are always solutions to recover it.
If you click on " Forgot password ", you will be put in touch with the team at Yahoo! who will ask you a few security questions such as your place of birth, your childhood best friend or even the first name of your dog! If you answer his questions correctly, you can reset your access code and therefore regain access to your Yahoo emails and contacts. It doesn't work most of the time, but if it really doesn't work, you'll have to try to understand the cause of the hack you've been the victim of.
For that you have to think like a hacker, where did he find the security flaw? A too simple password can be or then the link of a fraudulent email on which you clicked? Have you thought about cleaning your computer of possible viruses? Maybe your contacts are also in danger? You should contact them one after the other to warn them that if they receive a message from you then you should not answer it because they will communicate with the hacker who will try by all means to extract money from them.
Here is a list of methods of which you are most certainly unaware and yet which can be used against you in order to hack into your Yahoo! account. It should be known that the methods evolve each year more and more. For example, if you find that a method could be classic 10 years ago, know that there have necessarily been variants that are much more threatening. It is for this reason that it is necessary to constantly stay up to date on the evolution of cybercrime.
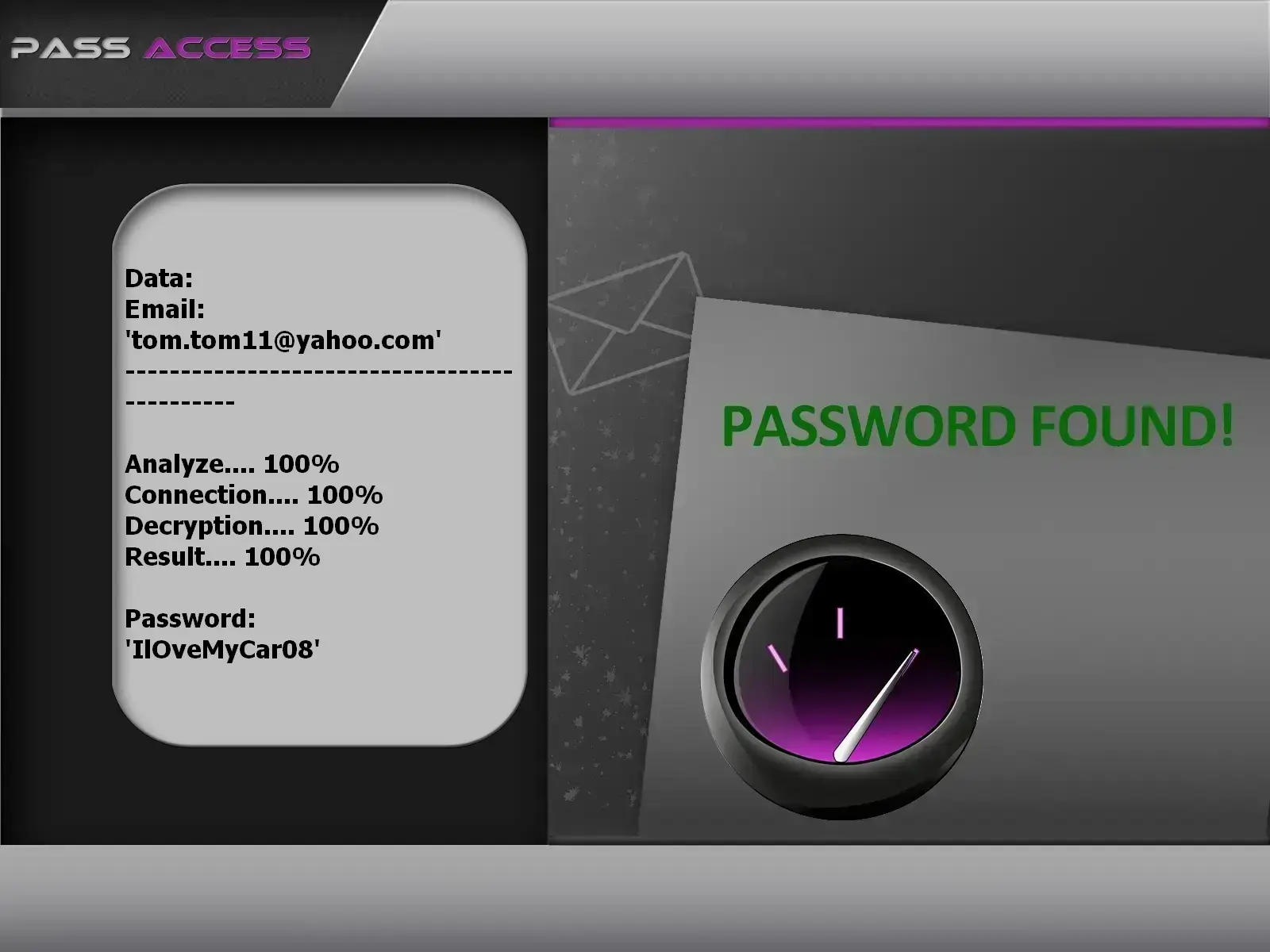
password using PASS ACCESS.
PASS ACCESS is a password recovery tool that allows you to regain access to your Yahoo! account, even if the password is complex.
Thanks to this software, specially developed by cybersecurity engineers, you can decrypt passwords for any Yahoo! account
It is extremely easy to use and suitable even for users with limited technical knowledge. Simply follow these three easy steps:
Additionally, you get a 30-day trial period. At the end of this trial, either it works, or you get your money back. Now is the perfect time to give it a try!
Download PASS ACCESS from its official website: https://www.passwordrevelator.net/en/passaccess

Speaking of much more dangerous variants, here we are in an adaptation of the famous phishing technique still known by the population as phishing. Phishing is an information-gathering technique in which the hacker tricks users into sending a message that contains a link. If inadvertently or through negligence or ignorance this user clicks on the link contained in the message, he will be automatically directed to a platform which is controlled by hackers. But a platform that looks like a classic website that the latter will be used to visiting. This is how he will have his personal data stolen. In the variant of Spearphishing, the victim will be targeted in a particular way. Consequently, the hacker will deploy all possible methods to gain his trust, by collecting data that could lead him to believe that he is exchanging with a known person. In the professional field, this strongly resembles what is commonly called Business Email Compromise (the fact that the hacker, for example, usurps the identity of his victim's boss in order to force him to act and do something which he should not do in principle). As you certainly notice, this variant is much more dangerous in that it is easy to deceive the victim.
DNS is a set of infrastructures that facilitates the use of a website or several other IT tools. It mainly acts in the communication between computer devices and servers in order to allow the transmission of data as well as their reception. It may happen that, thanks to cookies, which represent a kind of beacon, the system creates a path that makes access to a platform much faster and easier for the average user. This means that if, for example, you are used to connecting to your Yahoo! via your browser such as Google Chrome, each time you try to connect to Yahoo! via this browser, the connection and loading time will be much shorter than the very first times. This not only saves a lot of time but also represents ergonomics and a better user experience. Unfortunately, cybercriminals know how to exploit these infrastructures against us. To succeed in their moves, they will proceed by what is commonly called cookie poisoning. This essentially consists of injecting malicious codes into the cookies installed in the DNS. When the hackers succeed in this, they can then hijack the path usually by each Internet user. For example, by going to your browser and connecting to yahoo.com, your connection will be diverted to a Yahoo! website. And that without you even being able to account for it. This is how they can collect your login data and use it against you. The most difficult thing in this context is that the victim has no means of protecting himself. Especially if the DNS poisoning goes back from the ISP. A situation that happens often.

The use of malware is clearly a must when it comes to account hacking. These computer programs were designed specifically for this. The most famous are among others:

When we talk about hacking, the aspect of the SIM card does not immediately come to mind. However, on this side, there are indeed certain security flaws that can be used against its user. First of all, talking about the technique call the SIM Swap. This method allows hackers to steal a phone number without even using the Internet. As we know, operators offer a way for a user to recover his SIM card if he accidentally lost it or if his phone was stolen. In our hacking situation, the computer hacker contacts the telephone operator of his victim. After authenticating the latter's identity, the cybercriminal will demand that the phone number be transferred to a new SIM card that he will have in his possession this time. And it is from this moment that the problem will really begin. Effectively, the
In addition to SIM swap, there is the Simjacking technique which is reserved for specialists. Indeed, it will consist in exploiting security flaws that are present in certain SIM cards to steal user data. Nearly 5% of SIM cards in circulation are vulnerable to Simjacking. Furthermore, with the expansion of e-SIM cards, one would expect to find many more such vulnerabilities.
In a context where cybercriminals already have a head start on you, it is essential to adopt good attitudes. A healthy digital lifestyle is essential for all users. If you want to keep your online accounts safe. Here are some techniques that can help you:
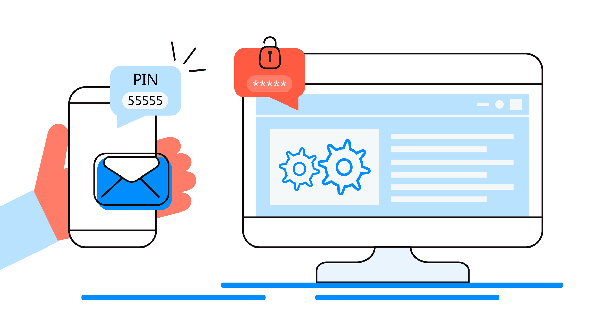
It combines the use of the password and a unique code sent by text message or email. It's an additional barrier if unfortunately your password is compromised. Fortunately, Yahoo! offers two-factor authentication. To activate it:

You must not use your Yahoo! on other accounts. If it seems tempting in some measure not to forget it, all users have this habit of using the same password on several accounts. If the goal is not to forget your password, it is risky when one of your accounts is compromised by a data leak or a massive hack. If you're having trouble remembering multiple passwords for multiple accounts, it's usually a good idea to use a password manager.

The trick that is most commonly given to users is to use long passwords of at least 8 digits made up of different characters such as letters numbers and even symbols. Yet today, it is better to use sentences instead of words made up of different characters. For example: " 1enfantjoueàlaballe " is more secure and reliable than " Agtisj4 ".

If you receive a message from questionable correspondence, the only thing you need to do is simply delete it. Don't try to understand. If this message is from someone you know and it asks you to click on any link, don't. If you are in a situation of excessive curiosity, it is rather preferable to go to your browser and enter the address of the website concerned manually. When the message comes from a professional manager or a co-worker, before initiating anything, it is advisable to call these people for oral confirmation. When you receive a message from Yahoo!, it is strongly recommended that you do not take any action knowing that you have not initiated anything that could produce this email.

While browser extensions are often very useful, they can often hide malware. This is why it is important not to overuse them. It is even advisable to delete them.

No matter what security measure you are going to use, it will be useless if your computing device is vulnerable to attack in some way. As mentioned above, the methods used by hackers to defeat your security are increasing in number and becoming more sophisticated. It is therefore appropriate to know how to use an antivirus. It is the simplest cybersecurity solution. Whether you use a computer or a smartphone, do not hesitate to get virus protection.

Updates are a necessity. Many users are negligent not to run the update made available. Yet security vulnerabilities continue to wreak havoc Zero Day. No antivirus software will protect you against a Zero Day security breach. Even less against a 0 Click exploit. If you see the notification prompting you to update, don't postpone it and update as soon as possible.
Despite all these measures, you may still be confronted with a computer attack. 100% security does not exist. It is purely utopian to believe that we are absolutely protected. This is why you must be ready to react immediately if you are attacked.
Yahoo account hacks are unfortunately quite common, given the platform's history of security breaches and vulnerabilities.
Yes, it is possible to recover a hacked Yahoo account. You can try the "Forgot password" option and answer security questions. However, if unsuccessful, further steps may be needed.
Common methods include phishing, malware such as keyloggers and spyware, DNS poisoning and SIM card hacking.
Some measures you can take include enabling two-factor authentication, using unique login credentials, regularly updating your password, being cautious of suspicious messages and keeping your devices protected with antivirus software.
If your Yahoo account is hacked, you should immediately change your password, review your account settings for any unauthorized changes, alert your contacts about the breach and consider enabling additional security measures.
While some tools claim to help recover passwords, it's important to be cautious and avoid potentially malicious software. Instead, follow Yahoo's official account recovery procedures.
Yes, using a password manager to generate and store unique, complex passwords for each account can significantly enhance the security of your Yahoo account and other online accounts.