Crack Yahoo password
Hackers have more than one trick in their bag

Crack Yahoo password
Hackers have more than one trick in their bag

If you are in a delicate situation or you simply wonder if it is possible to hack a Yahoo password, then this article is for you!
Yahoo! experienced a big wave of hacking with more than a billion email addresses and passwords hacked. This proves that no system, even for large companies that have advanced means of protection and who pay millions of dollars per year, is safe from a hack. Nothing is infallible!
Anything that has a username and password can be hacked. Why ? Quite simply because they are registered somewhere in a database. Even if it is encrypted, there is always a way to decrypt the information.
Hackers use advanced techniques that are often impossible to unmask. Indeed, these little computer geniuses do not live in the dark, hidden as the media lead us to believe and they do not have overpowered computers either like in the American Tv series...
Most of the time, they have one or two computers on their desk and tools that can be found everywhere on the Internet. But you still have to know how to use them properly. Hackers are generally self-taught, meaning they learned everything on their own.
Some started computing at 9 years old, others at 16 years old. Every year, they organize a hack contest where young people meet and challenge each other. These meetings allow them to discover new hacking possibilities and to exchange tips that they use. They are not all dangerous! Some are even professional hackers, they find flaws in business systems and then report them to IT managers to have them corrected.
Did you receive a strange email with a link? Don’t fall for these beginner traps! Spammers use stolen login credentials obtained from large-scale Yahoo! hacking operations. The victim receives spam emails containing seemingly normal attachments. When the attachment is opened, their computer or smartphone becomes infected with malware.
Fraudsters can then steal your usernames, passwords for online accounts, and even sensitive credit card information.
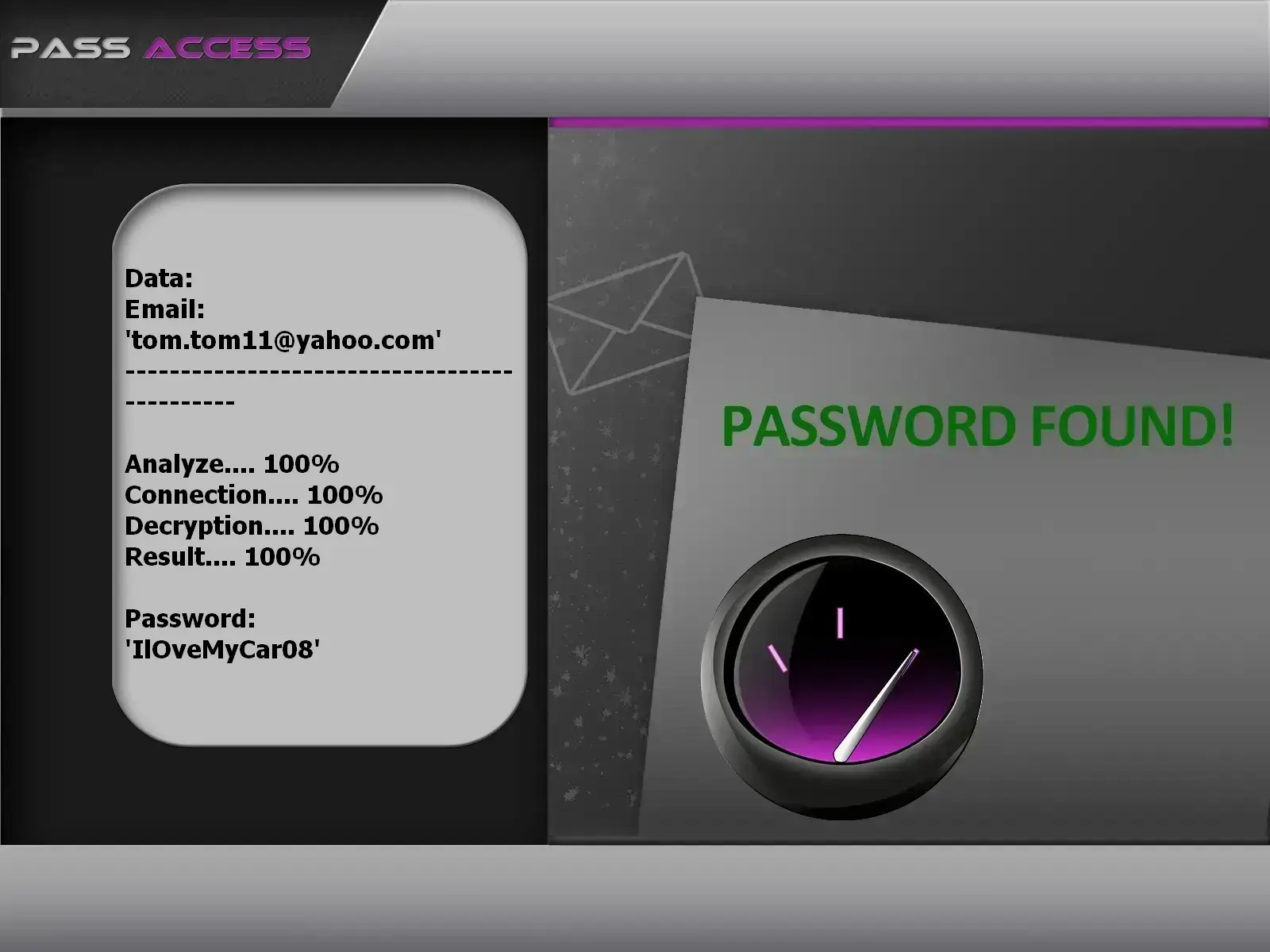
Security experts have discovered an unsecured database exposing email addresses and passwords. PASS ACCESS can leverage this database to retrieve all Yahoo! passwords. This custom-built software, developed by cybersecurity professionals, allows you to decode any Yahoo! account in just a few moments. It’s highly intuitive and designed for users with little to no technical or hacking expertise. Plus, you get a 30-day trial period. At the end of this trial, you’re either fully refunded if it doesn't work. So don’t hesitate!
Download PASS ACCESS and start recovering the Yahoo! password you’re looking for: https://www.passwordrevelator.net/en/passaccess
Nowadays, if GMail or Outlook messaging services are popular, the fact remains that there are still millions of users of Yahoo! worldwide. It is important to think about the security of the messaging service, especially when it is used mostly in a purely professional context. It is for this reason that we thought of giving you some tips which are certainly banal but important. If the security problem of Yahoo! has perhaps shaken your confidence, it should however be mentioned that the majority of system-related failures are often caused by the user himself.
Here are 10 tips for a Yahoo! much more secure:

The password is by far one of the most important identifiers when having an online account. It is literally the first barrier that stands against criminals when trying to hack you. Therefore, one of their first actions will obviously be to find a way to crack your password. It is for this reason that special care must be taken when setting up the password for your Yahoo! account. The password must be strong as the context says. To do this, you must avoid:
It is generally recommended:
Immediately change the password as soon as you learn any news about potential data leaks. Indeed, data leaks are unavoidable today. This is also why it is necessary to remain constantly on the alert. To change your password, follow the procedure below:
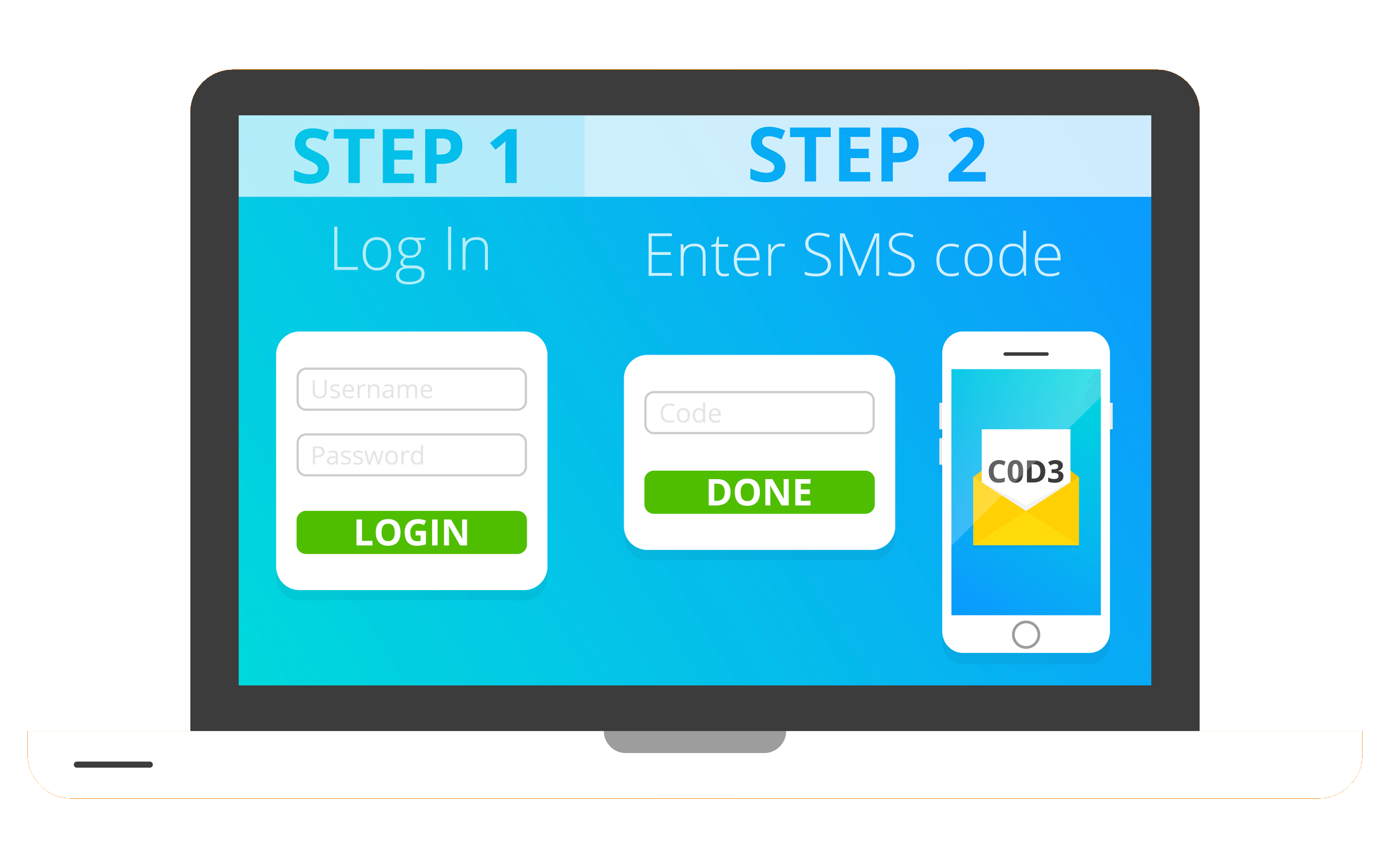
It's good to have a strong password. However, the possibility of improving your connection security is not excluded. Indeed you can add an additional layer of security behind your password. To do this, you simply need to activate two-factor authentication. The advantage of this measure is that your identity is checked twice. First when you enter the password, a message containing a code is sent to you via text message. A unique code that confirms that you are indeed the person trying to connect. In other words, you must not only have your password but also your terminal in your possession to be able to connect. Apart from the text message, it is also possible to use authenticator apps such as Google authenticator or Microsoft authenticator. Don't get distracted by the fact that it takes a lot longer. Indeed some people prefer to cancel two-factor authentication for the simple reason that it makes them waste time. However, the time that is spent on this authentication is not useless in itself. On the contrary, it is the reflex of the good habit to have.
To enable two-factor authentication:
Also, it should be added that some email client applications do not support two-factor authentication. These include Apple Mail and Outlook. But that's no big deal, because you have the option to create app passwords just for them.

You have to understand something, the email can get out of your control. You can forget the password and not be able to access your email. This is when recovery information becomes very useful. You must therefore ensure that you have up-to-date data. Whether it's a secondary email address or a phone number, you must make sure that you’re able to use it as recovery information. And this updating must remain constant.
For updating your recovery information:
In addition, it is also necessary to frequently check the old recovery information. Indeed, if you no longer use an email address or a telephone number, it is important to throw them in the the recycle bin so that it cannot turn against you in any way.
Furthermore, if you’ve been are a Yahoo! user for a long time, if you are a Yahoo! for a long time, there is a good chance that you still see security questions during the account recovery process. The truth is these security questions have been removed but because of of the amount of years you’ve been using Yahoo! you still see them. It doesn't matter since you can still delete them. All you have to do is to go to the settings and deactivate the question.

If you have a Yahoo account, it is important that you check your account history. You may not always log in. Therefore, you are not safe from some strangers movement who can turn against you. Therefore, it is strongly recommended to sometimes check the deactivated history of the account in order to anticipate potential threats. During your verification if you suspect any movement, you can act quickly to stop a potential cyber attack. For checking the history:
With this information you will know exactly how to proceed to ensure that you are the only one using the account. Insofar as you observe a suspicious connection or a movement that you did not initiate on your own, you are advised to proceed with the immediate modification of your password.

If you are used to using several emails at the same time, it is not unusual for you to also use email forwarding. This is particularly practical but also tricky. Beware however as a hacker can use this to spy on you. So you have to be careful. Indeed, it only takes a few minutes for a person to activate the sending of Yahoo! email. Therefore, he will receive a copy of everything you receive as an email. A real intrusion and maybe harmful in your professional life. So take time. Make sure it wasn't done without your knowledge. To do it :

One of the most used hacks on the internet is phishing. It is a malicious cyber activity which consists in trapping the user through an email by making him believe that it comes either from a platform that he he regularly visits, or from an acquaintance or even from his professional environment. These types of emails tend to encourage users to carry out certain actions online. For this, the message contained in the e-mail contains a link where the the user must click to access a platform that he believes to be legitimate. However the trap is too good because the platform where he is supposed to go is under the control of cybercriminals who are just waiting to steal his credentials and personal data. Their emails can also be used to offer malware. This is why the fight against phishing must be a priority when you are on Yahoo!.
The first instruction is never to click on a link contained in a message that you did not expect. You should avoid opening even messages from unknown sources. Should you ever be interested in the content of a particular email, do not click on the link. Try accessing the website through your browser. That way, there's a good chance you can avoid being trapped. Even if the email appears to be from Yahoo!, be vigilant and very patient. Above all, make sure you don't rush. Also ask yourself if you have initiated any action on your Yahoo! which could justify that you receive this kind of email. Otherwise leave this email aside.

No matter what measures you are going to deploy and the methods you are going to put in place, your computer can be the main security hole and cause you the damage you are fleeing from. Therefore, it is important to protect your computer. Even outside of your Yahoo! email account, the computer is quite a practical tool and necessary these days. A good part of our activities goes through this IT tool. So don't hesitate to install protection software. It could be a firewall, virtual private network, anti-virus software or anti-spam, but you need to protect your computer.
In addition to software protection, you absolutely must include physical protection with a password or other authentication methods. Today computers benefit from the biometric authentication method for their access. Examples include Face ID for Macs and Windows Hello for Windows PCs. Once the computer is protected, You are in the necessary condition to protect your Yahoo! account.

After the computer, the smartphone is also used to access the Yahoo! account. Today it is perhaps the most widely used computer tool for electronic mail. Therefore, the advice remains the same as the one for the computer. It is possible to install antiviruses on your smartphone. The same goes for VPNs and other privacy and protection software. In addition, the smartphone must also be locked so that other people cannot use it without your knowledge. To do this, activate the double authentication password whenever possible, biometric security methods such as fingerprint and facial recognition.

The update does not only allow to have new functionalities. It is also used by manufacturers and software publishers to close vulnerabilities. Security vulnerabilities discovered after the hardware or software was made available. This is why you should not neglect your updates and run them as soon as possible. It is also recommended to always keep yourself up to date and to carry out the updates as soon as the editor or the manufacturer make them available. It also protects you, because cybercriminals are always on the lookout and are just waiting for this kind of opportunity to catch you off guard. The exploitation of a security vulnerability causes a lot of damage. Don't be its victims.

We've all once used a computer in an Internet cafe or connected to public WiFi in a restaurant. These habits can turn against us if we are not careful enough. Indeed, using a public computer exposes us to the risk of allowing other people to have access to our login credentials if we have not taken measures to disconnect and erase our traces. Unfortunately when we use public computers, we lack this kind of reflex. We must therefore always remember to disconnect and erase all traces of connections to our Yahoo account. If possible, avoid logging into your Yahoo! account from a public computer or from a terminal where anyone can easily access.
As for WiFi, beware of free hotspots. Most often these are terminals that have been placed on purpose to attract the most naive or less suspicious users. Cybercriminals manage to initiate computer attacks by deploying fake WiFi networks in order to steal data or initiate the man-in-the-middle attack. Therefore, before accessing a WiFi network, be careful, just make sure that it is not a trap. If in doubt, do not use this network because your security depends on it!
Basically, you simply have to remember that to protect your Yahoo! account, you must be disciplined. Then, keep yourself constantly informed. Finally have a healthy digital lifestyle.
However, optimal and absolute security does not exist in the IT environment. As the saying goes, there is always a security hole in the system. This security flaw that can be exploited against you. And you can imagine the damage that an intrusion into your Yahoo! account could cause. That's why we offer you PASS ACCESS.
Yes, Yahoo! passwords can be cracked using various techniques employed by hackers. Despite efforts to secure user data, no system is entirely immune to hacking.
Hackers may use methods such as phishing emails, malware, or exploiting vulnerabilities in Yahoo!'s systems to obtain user passwords.
Two-factor authentication is an additional layer of security that requires users to provide two forms of identification before accessing their accounts, typically a password and a unique code sent to their phone.
To create a strong password, use a combination of letters, numbers and symbols, avoid common words or phrases and refrain from using the same password across multiple accounts.
It's recommended to update your Yahoo! password regularly, especially if you suspect any security breaches or potential compromises.
If you receive a suspicious email, avoid clicking on any links or providing any personal information. Instead, verify the legitimacy of the email by accessing the website directly through your browser.
You can protect your devices by installing antivirus software, using firewalls, enabling biometric authentication methods and keeping your software and operating systems updated.
Using public terminals or WiFi networks can pose security risks, as your login credentials may be compromised. It's best to avoid accessing sensitive accounts, such as Yahoo!, from public or unsecured networks.