10% of SIM cards would be vulnerable to Simjacker
During the month of September, it was revealed that there is a security flaw in several SIM cards.
This security breach allowed some people via specific SMS to collect personal information about users of vulnerable SIM cards. This new form of piracy was called the "Simjacker."
This article will also interest you: Watch almost anyone via his SIM card, it's the Simjacker
The vulnerability was discovered by society Adaptive Labs in early September. In its report published this month, the company explains that this security breach had been exploited since 2013 by other researchers especially this from SR Labs.
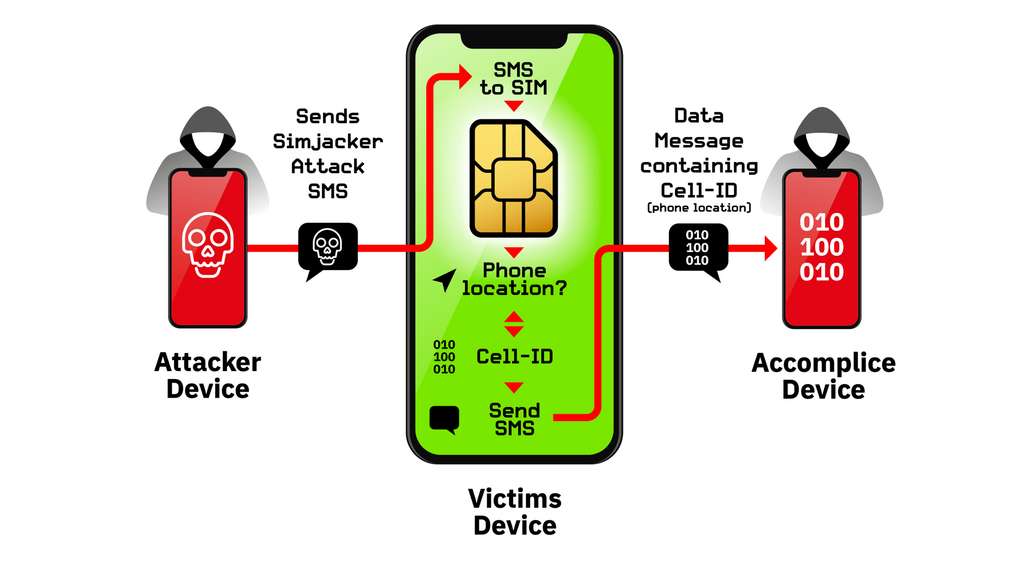
As a reminder, let's explain how the SIMjacker works:
Hackers to exploit the flaw send a command SMS to the vulnerable SIM card. one texting the text message. The SIM card in turn responds to hackers to provide it information he needs to determine either geolocation, the type of device used, etc. All this happens without the card user's knowledge Sim card. This is what drives computer security researchers to be concerned about this security flaw that has been going back five years. Especially since it can be easily used "to surveillance purposes. »
So far we have no exact idea of the number of victims, or even exact figures for SIM cards Vulnerable.Just approximation of 10% SIM cards in circulation.
According to SR Labs, the German company specializing in cybersecurity of mobile devices, this flaw is not to be overlooked as since 2013, it has been trying to report it and identify its consequences. and to do this, they had to test about 800 different SIM card models to justify the reality of SIMjacker attacks. In this regard they explain that the vulnerability allowing the Simjacker attack works thanks to an SMS as mentioned above.
It is an SMS that contains "Sim Toolkit" instructions that is directed to a single application called S@T, which is only installed on certain SIM card models in particular. Apparently this wouldn't be the only flaw that compotes some categories of SIM cards. SR labs talk about a second vulnerability that can be exploited on another Wireless Internet Browser application, a flaw discovered by the Ginno Security Lab, which published it on its website.
A little bit at this stage, we can conclude that there are now two possibilities for hackers to engage the Simjacker. The SR Labs in a survey gives some figures:
– 9.4 percent of SIM cards that have been tested has an app S@T
– 10.7 percent of other SIM cards tested have Wireless Internet software Browser.
It is true that this panel is not representative, and what is certain, not all SIM cards are not necessarily involved in this security breach. This can be explained by the the fact that SIM card and application configurations will vary according to telephone operators. For each House mobile phone, there will be a particularity brought to the the SIM card that she will use.
In the end, the Simjacker is indeed a reality. Maybe everyone is exposed in any way. The major problem with this vulnerability, which the user cannot protect by himself. it is obliged to rely on mobile operators who must provide an adequate solution to put an end to this security breach.
Now access an unlimited number of passwords:
