
Ryuk: French cybersecurity watchdog publishes ransomware report
Earlier this week, the National Information Systems Security Agency in abbreviated "Anssi" published a document on one of the most dangerous computer programs of the past 10 years: the Ryuk ransomware.
The purpose of the french-sponsored cybercrime response agency's objective is to provide more information on the workings of the groups of cyber criminals who use this malware, the malware itself and its harmful consequences on the lives of targeted organizations.
This article will also interest you: The French market in the face of cybersecurity according to the report ISG Provider Lens™ Cybersecurity – Solutions and Services
It draws its source from the manga death Note, the name of a famous character characterization characterization of the god of death, who holds a notebook in which the name of every person who is registered certainly finds death in a certain condition. In real life, Ryuk is a dangerous software used by cyber criminals to subjugate computer systems and extract money from victims. It is classified as one of the most dangerous software in its category, the most dangerous ransomware in the world.
Among the victims of this dangerous program are several large, medium and small businesses around the world, in different sectors and on all continents. Namely Steelcase, UHS, Sopra Steria…
Faced with the proliferation of such software, and the dangers it creates, the National Information Systems Security Agency has decided to better inform all IT sectors, as a prelude to this dangerous ransomware. A very detailed document for companies in particular
"The Ryuk ransomware was first observed in August 2018. It is a variant of the Hermes 2.1 ransomware, sold on the underground forum exploit.in from February 2017 by the cybercriminal group CryptoTech for about 400 dollars," the public body said. He added: "Ryuk consists of a dropper, depositing one of two versions of a 32- or 64-bit data encryption module on the victim's post. The dropper then runs the payload. After a few minutes of inactivity, Ryuk then seeks to shut down more than 40 processes and 180 services, including those related to antivirus software, databases and backups. It ensures its persistence by creating a registry key."
While this malware is rampant in almost all sectors, the health sector appears to be the most affected. Because of its too much exposure because of these events that mark the domain. Indeed, health accounts only during the month of October, about 75% of computer attacks recorded in France.
Moreover, in early November, it was found by security specialists on nearly 1,400 hospitals, pharmaceutical companies, universities and government agencies would be in contact with computer servers and platforms by being linked to a group of hackers known as one of the operator of the Ryuk ransomware. "Ryuk remains a particularly active ransomware in the second half of 2020. It differs from the majority of other ransomware by the fact that at least one of its operators attacked hospitals during a pandemic, by the absence of a dedicated data disclosure site and by the extreme speed of execution (in the order of a few hours) of the Bazar-Ryuk chain of infection, warns the National Agency for Security of Information Systems.
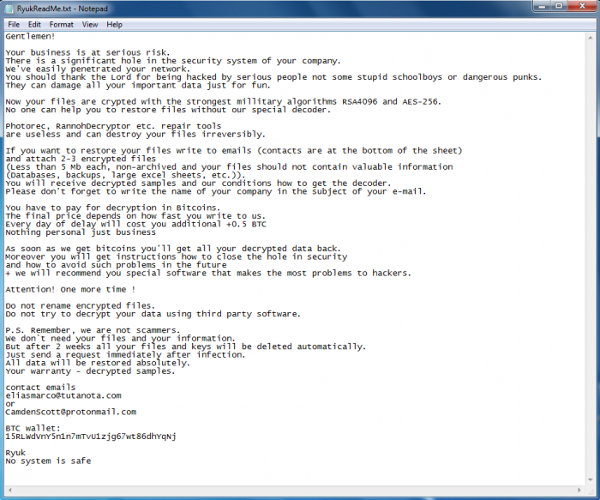
"The vector of infection usually appears to be a phishing email delivering either Emotet or TrickBot," explains the French cybersecurity watchdog. The organization specifies because TrickBot is the loader that distributes the Ryuk program the most. "Once legitimate post-exploitation tools are distributed by TrickBot (Cobalt Strike, Empire, Bloodhound, Mimikatz, Lazagne), attackers gain privileged access to a domain controller and deploy Ryuk (e.g. via PsExec) within the victim's information system." Note the Anssi.
However, there has been a change at this level. Indeed since September 2020, the chain of infection has reportedly switched to BazarLoader-Ryuk instead of trickbot. Whether this is final or just temporary.
The main groups of known hackers to date use this malware are UNC1878 mentioned above, Wizard Spider, FING, Buer and SilentNight.
It is true that Ryuk does not appear in practice as a ransomware as a service (RaaS). However, the National Information System Security Agency has noticed the involvement of several attackers during a chain of contamination that resulted in the use of the latter.
Now access an unlimited number of passwords!