Hack WiFi keys
A WiFi key is never secured

Hack WiFi keys
A WiFi key is never secured

Hacking a WiFi key is not a simple process, but it can be easy for a motivated person to want to take over the coveted Internet network.
Even if you use a simple WEP or WPA key with a long password, you will see in this article that it can be very easy to hack a WiFi account.
When a hacker attacks a WiFi network, he looks at how the key has been encrypted. WEP keys are easier to crack than WP2 keys. Since the source of the WiFi signal is broadcast by the box, the device itself would be an excellent target to be hacked. However, the routers of the boxes are regularly updated with certain parameters to prevent the routers from being attacked via brute force. However, the flaws still exist and hackers take advantage of them.
The most basic form of protection is WEP encryption. In recent years it has become a dangerous option because of its vulnerability since it can be quickly hacked. Although this is the case, many boxes still use this type of protection.
As for the WPA which is an alternative security, it will be necessary to find the sentence which corresponds to the WiFi key. You will then have to use a WiFi key simulator which can thus pretend to connect and interrogate the box to retrieve the WiFi code.
Otherwise, there are other solutions such as the attack by the dictionary or by the password generator. Today's computers are powerful enough to find the WiFi password in just a few minutes.
Of course, before they tried to start hacking, hackers made sure to measure the protection so they could adjust their tools. Hacking WiFi passwords is not just for hackers, it can also be used by the owner of the network to test the security of the network.
To hack a WiFi key without being a hacker with great computer knowledge, there is software that can hack for you.
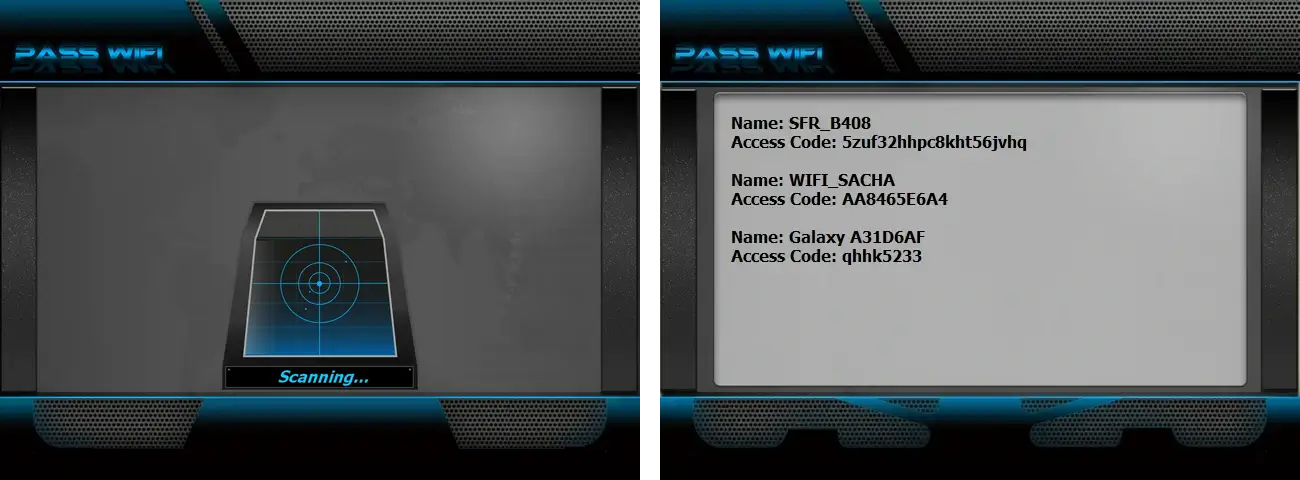
PASS WIFI is the unique solution allowing to scan and display the passwords of the routers to be connected.
PASS WiFi is a good alternative to all existing methods to determine if the security of your account is reliable. It is convenient and easy to use. Know that it was designed by cyber security professionals. Thanks to these powerful algorithms, it is able to detect any surrounding WiFi network and provide you with the password in plain text. You have the advantage of being able to use it either on a computer, a smartphone or a tablet. It is compatible with all operating systems. That's what makes your job easier. In addition to that you have a free month of trial. At the end of this period, you are either satisfied or refunded.
You can download PASS WIFI now: https://www.passwordrevelator.net/en/passwifi
If you are an IT professional, here is a list of methods that can help you hack a WiFi network. These techniques are commonly used by hackers:

There are malicious programs, which when installed on a computer device, allow their users to be able to collect data that comes from the infected device. Data extractors can work in different ways. There are data extractors that can work remotely using WiFi or Bluetooth. The goal is obviously to exploit security flaws present in the communication network or in the devices used for data transmission. It is a relatively complicated technique, it essentially requires a good knowledge of the hardware and software of the devices concerned.
There is also the data extraction method which can be done through USB cables. As we certainly know, USB cables are not only used to charge the phone. They also allow you to transfer files and receive them. Therefore, cybercriminals can simply exploit vulnerabilities that are present in a cable in order to extract data from the connected device. Since we are used to charging our smartphones by connecting them to charging stations in public places or to terminals such as computers, it is not uncommon for this to turn into an opportunity that can be exploited by hackers to steal your credentials.

The password may be stolen in order to gain access to the WiFi network. It is not uncommon that when using a wireless network, we can for example save the connection in order to be able to access this WiFi automatically. Therefore, the secret code is also saved. To successfully steal the password correctly, without using malware, it will be necessary to physically access the device that has already connected.
When it comes to an Android smartphone for example, just go to the settings and access the part allowing you to generate a QR code. This feature was created with the aim of allowing the user to access WiFi without putting in extra effort. It is also possible to take a picture of the QR code to be able to use it later.
It is also possible to steal the password by creating a fake WiFi Hotspot. Indeed, by imitating the name of the already existing WiFi, the hacker will ensure that the user connects to the WiFi believing that it is his. Once connected, the hacker will then try to save the user's network password. The hacker will only have to use it to connect this time to the real WiFi network.

In a show of solidarity, it happens that users of digital services set up computer programs with the aim of being able to share the passwords of WiFi accounts recovered almost everywhere. It's a kind of community or forum where passwords are shared to allow potential interested parties to use them. For example, there are such applications on the Play Store or even under the AppStore. Which means you don't have to be an IT specialist. All you have to do is download the application and hope that one of the people who are on this space can help you obtain the password you are looking for.

These are monitoring software and there are all kinds. It is also possible to obtain it from official application stores such as the Google play store or the Apple AppStore. Stalkerware makes it possible to follow the activity of a person on a computer device, for example the smartphone. When installed on the victim's device, the hacker has to be patient and wait for the victim to connect to their WiFi network. By entering the password, for example, you can easily collect the data that interests you. The advantage with this kind of application is that it is easy to hide it, especially if the person you are targeting is close.

Let's just say that it is a technique that has its limits. However if, for example, you are unable to access the WiFi key in one way or another, it is possible to use the default password for it. Almost all routers from the same manufacturer have the same default passwords. But before using the router's default password, it is necessary to initiate its reset. But for that you must have physical access to it. It's impossible to access it remotely because the reset button is on the back of most routers.

There is still a flaw in the system. The router remains hardware with its vulnerabilities. Whether critical or minor, there is always a design flaw that can be exploited. Indeed, there are hackers who have specialized in WiFi flaws. Notably the APT41 hacker group. Typically, vulnerabilities in firmware (referring to a computer program that operates hardware such as a router by giving it instructions) are the most exploited. And there are cybercriminals who specialize in finding these kinds of security vulnerabilities.

In the field of account hacking, it is clearly a must. Social engineering is the practice of using this social interaction with a person in order to extract information necessary for their own hacking. If there is one thing that should be remembered in this practice of cyber malevolence, it is that the person who practices social engineering is necessarily someone who is close to us. It can be a contact on Facebook or Instagram with whom we have become accustomed to discussing at length. The potential people in the best position to practice social engineering in this scenario are parents or co-workers. The objective is to ask fairly simple questions, which will gradually push the individual to say things that can be used as passwords. Of course, as we know, users tend to use passwords that are immediately related to their habits so that they are not easily forgotten. And it is precisely on this facility that account hacking using social engineering is based.

We are talking about a technique that strongly resembles social engineering. However, the setting is completely different. Indeed, the technique of the spider will consist in rather establishing a profile of use of the computer tools of the victim. Unlike the previous technique which requires social interaction, this one can definitely do without it. In the majority of cases, the hacker prefers to observe the victim from afar or on social networks in order to get to know him better. It must be said that spidering is most often used against large organizations. Their network being much more profitable to hack than that of a personal WiFi. However, we cannot deny it, it is something that requires a lot of patience and a very acute sense of analysis.
One thing is certain, no organization is immune to data leaks. Everyone can be hacked because without even knowing it, your identification data may have leaked somewhere, leaving people with bad intentions to have access to it. There are spaces, forums or sites sharing data because of these data leaks. Some also trade in it. Data leaks occur for different reasons, either because of a computer hacking that was suffered by the telephone operator, by the Internet service provider or because of a computer programming error. One thing is certain, the user is rarely responsible for a data leak. However, hackers are constantly on the lookout. They wait for any opportunity to dig into data and use it against users. In the era of artificial intelligence and Big Data, data leaks are real boons for cybercriminals.

When your WiFi router is affected by a computer hack, there are obviously several unmistakable indications:
One important thing to remember when you feel like you've been hacked is to remember to reset your router. This will have the benefit of restoring the system to its original state. However, please respect these main rules:
Hacking WiFi passwords without proper authorization is illegal and considered a cybercrime in many countries. It violates privacy and security laws and individuals caught engaging in such activities may face legal consequences.
While hacking WiFi networks typically requires advanced technical knowledge and skills, there are unethical software tools and methods available that claim to facilitate password retrieval. However, their use is illegal and unethical.
There are several steps you can take to enhance the security of your WiFi network:
Signs of a hacked WiFi network may include slow internet speeds, unexpected connections to unknown websites, unusual increases in internet usage and the appearance of unfamiliar programs or devices connected to your network.
If you suspect unauthorized access to your WiFi network, it's essential to take immediate action: