Crack MSN password
Learn how to protect yourself from hackers

Crack MSN password
Learn how to protect yourself from hackers

When we consult our mailboxes, we are far from suspecting that a hacker can consult them at the same time as us. Behind our screen, users feel safe and do not perceive the danger that there is on the Internet. However, a networked computer is extremely vulnerable. It's the door open to anyone.
It seems almost unrealistic and yet every day hundreds of thousands of MSN accounts are cracked. Hackers can read all your emails and access all your contacts. They can then send them spam, viruses and even pretend to be you! The interest? Financial of course! By pretending to be you, they can make your friends and family believe that you are in serious danger and that you need emergency financial assistance. This scam still works, even today.
People who crack emails passwords don't just do it for the money, even if it's their main motivation, they also do it to challenge each other. Hacking contests are held every year. They launch competitions among themselves, they exchange techniques, software that they themselves have made, etc... they are truly gifted. Their average age is 20 and some even still live with their parents and others sleep in prison...
They understood from an early age that with a computer and a little imagination nothing is impossible. It should be understood that an MSN username and password are stored in a database and that with patience, it is always possible to find them even if the data is encrypted. Researchers advise using long passwords like a sentence, while complicated passwords are no longer useful.
Here are some computer attacks to which you expose yourself:

With PASS REVELATOR, recovering a password has never been easier! Simply launch the application and enter the address of the account you want to hack. The software will connect to internal databases containing the credentials and display the password directly on your screen. The tool we offer is developed by cybersecurity professionals and gives you the ability to decrypt an MSN account in just a few minutes.
PASS REVELATOR is a cross-platform application that can be used on a smartphone, tablet, or computer.
You can download it from the official website: https://www.passwordrevelator.net/en/passrevelator

They are considered to be the most persistent threats in the field of cybersecurity. Trojans are the highly sophisticated tools that pose as the most widely used malware programs. Which means there is a high chance that you or anyone else will fall victim to a Trojan horse or be the victim of an attempted Trojan horse infection.
The Trojan is a computer software, which hides behind a legitimate application. Which means that there is a good chance that you will be the one downloading and installing it on your computing device yourself. And this is where the danger of this program mainly lies. It is very discreet and makes us the main vectors of its propagation. Its functionalities are also very developed. Indeed, the Trojan horse when it is installed on a computer terminal offers certain possibilities to its user. First of all, it can make it possible to execute malicious codes remotely on the targeted terminal. These codes that could install either spyware, ransomware or any other hacking program. They also make it possible in the process to collect information which is contained in the contaminated terminal. Thanks in particular to this feature, the hacker can easily spy on his victims and steal login credentials.
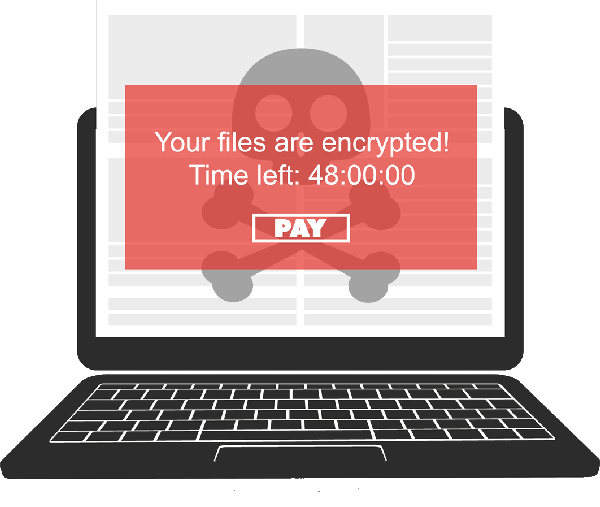
Ransomware is a very popular malware today. Their popularity mainly lies in the fact that they have been at the heart of several scandals exposed in popular media. We can highlight the Colonial Pipeline affair which deprived the United States of almost a week of fuel. There are many other examples to cite, but ransomware remains the most dangerous threat of the past 5 years. However, there are still misconceptions around this computer program. Ransomware or ransomware is not intended exclusively to hold a computer program hostage. It can also be used to collect a lot of information. Information that can be used for other purposes by hackers. For example, it is not uncommon for hackers to use the information collected on the computer system to blackmail their victims into refusing to pay the demanded ransom. In other measures, they use this information to initiate other hacks or sell it to other hackers. Another popular misconception about ransomware is that ordinary users tend to believe they can't be targeted. For many people, these malicious programs are intended for large companies. Which is totally wrong when you know that even a simple user can be targeted and be a victim.

In this category we are in a variant of phishing. This method has the particularity of targeting a person as precisely as possible. For this, a set of provisions will be taken by hackers to be able to succeed in this hack. It should be mentioned, however, that Spearphishing requires that the targeted person be a person on whom the cybercriminal has sufficient data. Indeed it starts with sending messages. This message can be sent by SMS, by email or by instant messaging via social networks. It is a message that is designed and tailored to the individual who receives it with information and data that may lead them to trust that message. This message will therefore invite this person to connect to their account via a link offered to them in the message in question. if he gets tricked into clicking on this link, he will be automatically redirected to a fake login page. This fake login page will prompt him to enter his login credentials. Of course, this is a platform that is run by cybercriminals. The latter will simply collect its information and reuse it as they wish. This is how by a simple message received you can lose control of your MSN account. We must still recognize that it is a formidable technique in the sense that it is organized and precise to target a particular person. To the extent that the individual is not suspicious enough, the consequences are immediate. This fake login page will prompt him to enter his login credentials. Of course, this is a platform that is run by cybercriminals. The latter will simply collect its information and reuse it as they wish. This is how by a simple message received you can lose control of your MSN account. We must still recognize that it is a formidable technique in the sense that it is organized and precise to target a particular person. To the extent that the individual is not suspicious enough, the consequences are immediate. This fake login page will prompt him to enter his login credentials. Of course, this is a platform that is run by cybercriminals. The latter will simply collect its information and reuse it as they wish. This is how by a simple message received you can lose control of your MSN account. We must still recognize that it is a formidable technique in the sense that it is organized and precise to target a particular person. To the extent that the individual is not suspicious enough, the consequences are immediate. This is how by a simple message received you can lose control of your MSN account. We must still recognize that it is a formidable technique in the sense that it is organized and precise to target a particular person. To the extent that the individual is not suspicious enough, the consequences are immediate. This is how by a simple message received you can lose control of your MSN account. We must still recognize that it is a formidable technique in the sense that it is organized and precise to target a particular person. To the extent that the individual is not suspicious enough, the consequences are immediate.

Spyware, also known as espioware or spyware, is a computer program that has been designed specifically to monitor a person's activity. A long time ago, spyware raised the frames of myth. They were believed to be computer programs that could only be used for extensive hacking or by people with political or extremely criminal affiliations. We have all seen in spy movies the use of spyware. Yet we are in a context today where spyware has become more democratic in terms of its use. Particularly with the explosion of its known variants on the place of Stalkerwares. Spyware has even been in the news lately. Especially with the PegasusGate affair. We are now in a context where we must expect at any time to be the target of a hacker using this kind of malicious program. Spyware is now very sophisticated and offers a lot of features. Another reality must also be taken into account. It is possible to get spyware on the black market and use it against someone. This means that your MSN account can be targeted with software sold on any website.

Last year, the social network Twitter was the victim of a rather complex computer attack. This computer attack resulted in the takeover of several accounts of celebrities including Bill Gates, Elon Musk, Barack Obama. The investigations were able to show something quite interesting: the hacker did not really use sophisticated enough methods to succeed in his hacking. He just manipulated the right people. Indeed, he played with some employees of the platform to extract from them the information necessary for his hacking. In the jargon, this method is called social engineering. It is commonly used in several hacking processes without being hacking per se. Social engineering consists of forging links with an individual and then abusing their trust. Thanks to the relationship that the hacker will weave with his victim, he can gradually collect information on the latter. The information can then be used in a process of finding login credentials. The Twitter hacking example is a perfect illustration of this. Therefore, it is important that you are very careful in your communications when you are connected on social networks. Because innocuous questions may be asked in order to extract the data necessary for your own hacking.
In the digital sector, platforms, social networks and websites store a lot of digital data that comes from the interactions and activities of visitors on this platform. For reasons of negligence or for programming errors, it is not uncommon for these quantities of data to be exfiltrated and made available on the web or on the Dark Web. When this happens we commonly speak of data leaks. Unfortunately, data leaks are things that happen too often and the user has practically no way to protect themselves from them. Big platforms such as Google Facebook or even Yahoo! and Outlook have indeed been the victims of huge leaks recently. There are high risks that you will be affected. The danger with leaks is that the data in transit or exposed can be used in hacking contexts. Cybercriminals are constantly on the lookout for this kind of opportunity where they have almost no effort to provide. Indeed, thanks to your information, they can put in place a lot of means to hijack your online accounts. This is why you are most often encouraged to stay informed about the status of data leaks that are known or published. It is also recommended to have the habit of changing your passwords.

In the category of the most common techniques, we will discuss the dictionary attack or by the dictionary. You should know that it is a hacking technique that is a variant of what is commonly called a brute force attack. It is also known as password cracking in a general sense. Specifically, the dictionary attack allows hackers to try to guess the password of the MSN account they have targeted, by trying several passwords that they have harvested and stored in a register called a dictionary. Most often, the passwords used in the dictionary attack come from leaked data or from databases harvested from the Dark Web. It should be taken into account that the process is automated, which saves hackers time. If the dictionary attack does not work, then criminals opt for what is commonly known as password cracking. Another variant that will not just run on a dictionary of stored passwords, it will instead use an automated script that will try thousands or even millions of combinations of letters, numbers and symbols in an attempt to be able to guess the password. This is a relatively effective method when the password used to protect your account is not well constituted or is not a " strong password ".". So the next time you need to set up your password again, remember to use fairly complex combinations to prevent a simple script from overcoming your barrier. A simple sentence is enough to create a good password.
From year to year, hacking methods continue to grow in sophistication. Hackers are on the rise. In a context of increasing digitization, the use of the Internet and online platforms has exploded. The threat then becomes significant and persistent. You will have to think about protecting yourself.
How? 'Or' What ? You will say� quite simply by adopting good practices and a healthy digital lifestyle.
To do this, you need to put into practice some of the following tips:
If by chance you are caught off guard, we have a solution that can help you. Indeed, protecting oneself absolutely and flawlessly is impossible today. There is always a vulnerability that can be exploited against you. That doesn't mean you can't protect yourself, though. It is important, in addition to deploying security solutions, to use a tool that can help you recover your account as long as they managed to get ahead of you.
MSN password cracking refers to the unauthorized access to MSN accounts by using various techniques such as password guessing, hacking software, or exploiting vulnerabilities in the system.
Hackers are individuals who attempt to gain unauthorized access to computer systems or networks, often with malicious intent. They may do so for financial gain, to challenge themselves, or for other reasons.
Common cyber threats targeting MSN accounts include Trojan horses, ransomware, spearphishing, spyware, social engineering, data leaks and dictionary attacks.
To protect your MSN account, you can follow these tips:
If your MSN account is compromised, you should take immediate action to secure it. This may include changing your password, enabling additional security measures and contacting MSN support for further assistance.