Crack a password
The possibilities to crack a password

Crack a password
The possibilities to crack a password

What exactly are hackers looking for when they want to crack a password? Is this the notoriety? Is it genius? Money? Or just proving they are the best? Well, it could be all of them.
Actually, there are two types of crackers: the good and the bad. These are called whitehats and blackhats.
The whitehats are hacking email box to find the flaws and report them to the owner company of this service. Reporting these bugs allows them to protect and avoid surprises later. Generally, for reporting these problems, the nice hackers are rewarded with a sum of money. While blackhats only hack to resell the information later. They will try to make a maximum of money and exploit the data of the users. They will warn the company that they hacked into blackmail afterwards.
Millions of email accounts are sold on the Dark Web. There's even a seller who allegedly sells over 1 million usernames, emails and plaintext passwords of GMail accounts on the Dark Web. Moreover, according to a report by the Cybercriminal Agency International, which uses its skills, this hack has allowed 43 million user accounts to be exposed and disseminated publicly. All of this information has been listed on the Dark Web and offered for sale for just $10! These accounts also contain usernames, emails and their decrypted passwords.
Having an email account hacked can therefore go a long way! Although it is difficult to verify whether the data on the Dark Web is true or not, there is a lot of traffic and everything is selling. Hackers looking to make money largely use the Dark Web to sell hacked and stolen user accounts from old data breaches, which are then used by cyber criminals to perpetuate other crimes such as identity theft by spyware. Users are strongly recommended to reset their passwords as soon as possible, if they believe their accounts have been hacked. Also, if the same passwords and security questions have been used elsewhere, change them from. A hacker will sometimes hack an email account using a password with a password that has not been changed.
Don't believe that these scammers are hidden in dark places, most carry out their criminal activities in their living room sitting on their couch. Some embezzle millions of euros quietly in this rather surreal situation. They don't have the latest equipment either, a simple computer will do! Everything is decentralized, thanks to the cloud and VPN servers, they can simulate their presence in a place on Earth where they are not. This makes them invisible on the Internet!
Hacking an email address account becomes child's play if hackers use simple tricks like phishing, fake emails… these scams still work perfectly nowadays because people using computers trust their hardware first and do not imagine for a moment that they can be hacked.
Here are for you some techniques used by hackers to crack passwords and we will talk about the most known to the least known:
This is the password recovery application that works not only on computers but also on smartphones and tablets. Simply enter the account address you want to recover, and the software will display its password.
You can download the application from its official website: https://www.passwordrevelator.net/en/passrevelator

When we talk about cracking a password, it is immediately the technique that comes to mind of what they are used to using in this field. The brute force attack is classic. Cybercriminals use it constantly especially since hacking tools of this kind have known a certain sophistication in the last 5 years. In particular, this method is still effective against users who tend to mismanage their password. The brute force techniqueessentially consists of trying to crack the password by trying several combinations in a random or targeted manner so that the right combination can meet the needs of authentication. In one of its variants called the dictionary attack, the computer software will try a whole set of combinations which already constitute passwords collected and stored in a space known as the dictionary. In the variant called "password cracking", the password combinations used by cybercriminals are usually generated by an automated script based on user habits or even randomly. Of course, the way the user's password is composed will determine the duration and of course the effectiveness of this method against him.

Phishing, is by far one of the most popular password hacking methods there is because every user has heard of it at least once. Which means you are not ignorant of this subject. We speak in particular of phishing when the hacker uses a link to lead the targeted user to a web platform. The web platform in question is supposed to usurp the identities and colors of another. The objective of course is to make the Internet user believe that he is on a legitimate website and then ask him to provide his login credentials himself. If the latter is caught by the scam, he will himself allow the hacker to recover his passwords without the latter having to make additional efforts. Most often, phishing is carried out in a generalized way. That is, with corrupted messages that are composed with the aim of reaching the maximum number of people which allows the hackers to be able to have the maximum number of victims possible. However, there is a much more dangerous variant that is not widely known. These are in particular theSpearphishing. A targeted phishing technique that only targets a specific person or group of people that cybercriminals have already studied and strategized against them. Unlike phishing in general, spearphishing is difficult to counter if the targeted person is not someone who is suspicious and vigilant.
When we connect to the Internet, no matter what method we use for this connection, we do not think objectively about the possibilities of being trapped. However, there are other discreet and very effective techniques in the field of cybersecurity that cybercriminals use against us to collect our data. The man-in-the-middle attack, as the name suggests, is a method where the cybercriminal infiltrates our connection and monitors our web traffic. To achieve such a thing, the hacker will make sure to intercept your connection. For this, it has several methods. The most famous and dangerous is the provision of a fake WiFi network. Indeed, all WiFi networks, especially those that are accessible to everyone without any protection, are potential tools used by cybercriminals. And it doesn't really seem difficult. We are used to consuming the internet through WiFi. Therefore, it is just enough for the hacker to open a Hotspot and let users come and get tricked. The technique becomes much more dangerous when the cybercriminal decides, for example, to usurp the name of a WiFi router used by many people.
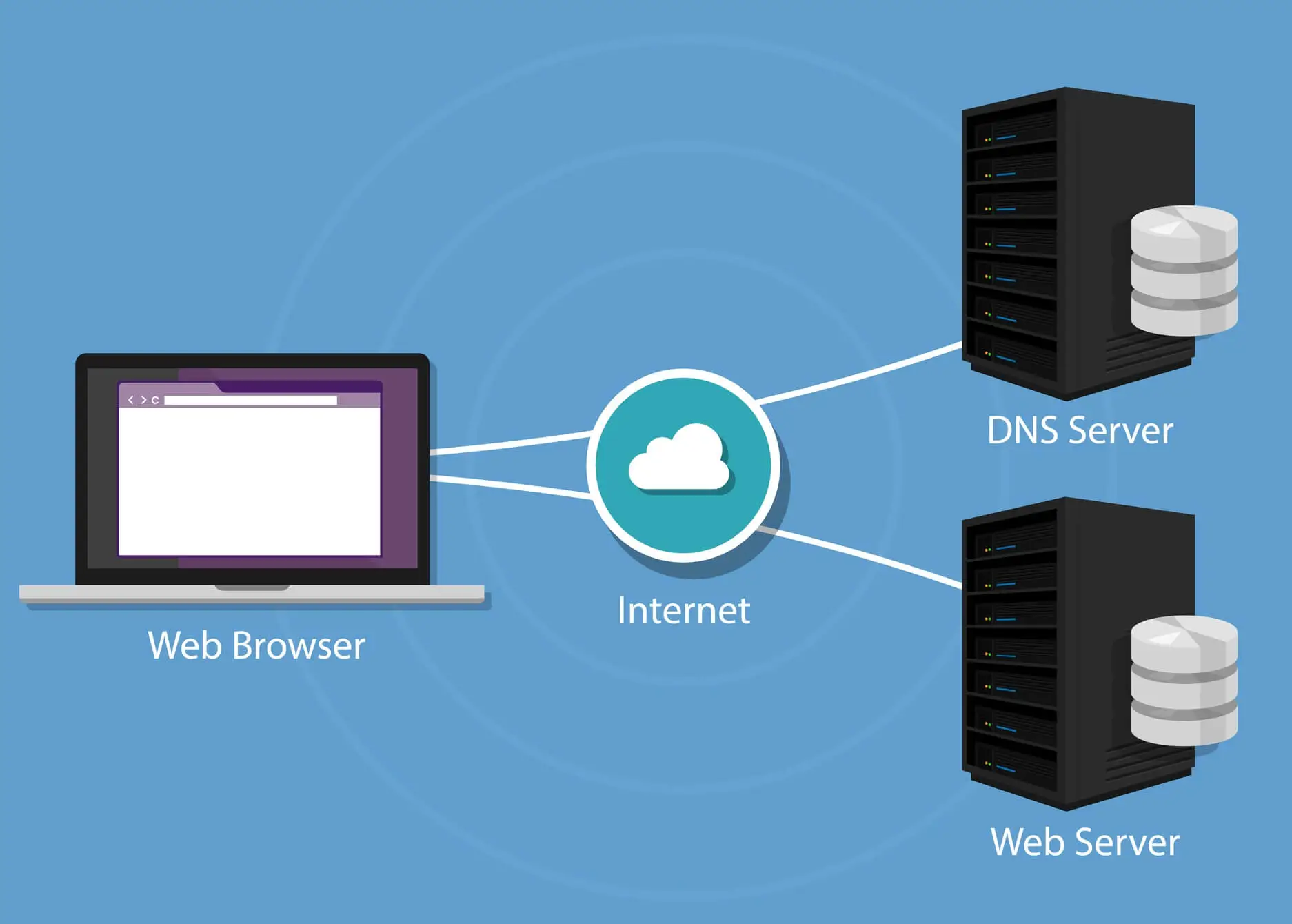
Many Internet service users do not know what DNS is. Yet, this computer tool can be the cause of your hacking and much more than that. " The Domain Name System or DNS is a distributed computing service used to translate Internet domain names into IP addresses or other records " (see definition on Wikipedia). Its role is to allow the user to easily access a computer address. Cybercriminals have found a way to take advantage of this feature. DNS often logs tasks to speed up access to websites or other platforms by Internet users. Through DNS cache poisoning strategy, it is possible for cybercriminals to create a path to other websites. And this, without the user even realizing it. When the technique is well implemented and the user uses any browser to go to a website he wants, his traffic will be diverted to another bogus website. A website that has been designed to collect the user's personal data. The most dangerous thing about this technique is that unlike phishing where the user must first click on a link, here there is no need to click on anything. The diversion of traffic is done from the base and it must be admitted that the Internet user has practically no means of protecting himself against it.

In order to protect themselves in certain sectors, all methods of connection to the wireless network are excluded. To do this, IT players are developing completely sealed connection methods to protect themselves from Internet threats. Therefore, it uses so-called Ethernet cables with RJ45 sockets. They are used to establish communication between the different devices of the organization or establishment concerned. The objective is obviously to prevent any external computer hacking. The problem is that specialists have developed a method that still allows them to hack into computers and collect data. Like what no system is unstoppable. So we wonder how they do it. The practice consists of simply exploiting the waves emitted by computers in order to collect sensitive data.
They will first seek to receive electromagnetic rays which are emitted by the Ethernet cables. Reception is done by a computer connected to a cable fed by an antenna. The constraint of this technique is that the hacker must be able to physically access the network and inject it with a malicious program to help capture the network. For the injection, it is possible to go through the use of a contaminated USB key and this method obviously works.

This particularly concerns those who tend to use any USB key on their terminal. Today everyone uses USB keys whether to store data or to transmit it. Consequently, these small tools then become vectors for computer attacks. USB drives can be contaminated with malware. The careless user just needs to connect it to their terminal. How exactly can this happen? The hacker can go through a relative who has started for example to download games on his USB key. It can also go through an imprudent collaborator. But what is much more common is leaving USB keys lying around as if they had been misplaced. Unfortunately, there are always people who will collect these keys and connect them to their computer.

Ransomware, also known as ransomware or ransomware,is a computer program that has the functionality of being able to take the computer system hostage. After the hostage taking, the hacker behind this operation demands the payment of a ransom. In exchange for the amount paid, the targeted person can then receive a decryption key that will allow them to free themselves from this virus. The problem with this technique is that we often forget that the hacker, in addition to taking the computer system hostage, also exfiltrates important data. This gives him the possibility of knowing your login information and sensitive data. Another negligence is to believe that only companies are targeted by this scourge. Anyone can fall victim to ransomware on a computer or even a smartphone.

In the category of malware used most often by hackers to steal passwords, the Trojan is clearly in the lead. The Trojan can infect a computer or a smartphone by passing an official application. It can itself be an official app which can be downloaded either from the Google play store or any official app. It can install malicious scripts on devices it has infected. Going further, exfiltrate information and allow monitoring of traffic and even the use of an individual's terminal remotely. Because he can even take control of this computing device. The Trojan horse is difficult to detect, which is why hackers like to use it so much.
We are talking here about a computer program which is a popular derivative of classic spyware. If for a long time it has always been believed that spyware was particularly used in a much more advanced context of hacking, the fact remains that there is a popular version that can be used by anyone: Stalkerware. These are computer programs that will have the ability to monitor the use of a computer terminal by a third party. This will then include the possibility of knowing the password of several accounts used by the target.
These techniques are as delicate to observe as to protect against them. However, you can easily avoid having your account cracked by adopting good behavior and good digital hygiene.
Hackers may crack passwords for various reasons, including gaining notoriety, showcasing their skills, financial gain, or malicious intent to exploit user data.
There are two main types of hackers involved: whitehats and blackhats. Whitehats identify vulnerabilities to help improve security, often receiving rewards, while blackhats exploit vulnerabilities for financial gain or malicious purposes.
Hacked email accounts are often sold on the Dark Web, exposing user data to potential exploitation. Cybercriminals may use this information for various crimes, including identity theft and espionage.
Hackers use various techniques such as brute force attacks, phishing, man-in-the-middle attacks, DNS poisoning, corrupted USB keys, ransomware, trojans and stalkerware to crack passwords.
Individuals can protect themselves by using strong, unique passwords, having updated antivirus software, regularly updating their devices, securing their devices from unauthorized access and staying vigilant against potential threats.