3 tips to protect yourself from phishing
Phishing or phishing is a technique that allows cyber criminals to collect information about Internet users, abusing their naivety or lack of vigilance.
It is also one of the most widely used practices in the field of cyber-malveillance. Almost all computer attacks have been based on phishing campaigns. This means that this fact should not be overlooked.
This article will also interest you: The phishing site: a continuous proliferation
Speaking of phishing, in French phishing, it is a technique that consists of simply attracting Internet users to a platform. A person who is usually takes the form of a legitimate web service that one may be used to using. Once on the platform that is in control of cyber criminals, Internet user is often invited in most cases, to fill out fields of information, in which he will be asked for personal data. Data that will be retrieved and used later in other circumstances.
In most cases, the hacker does not have a great need for technical skills to succeed. The same goes for the average user. Indeed, with good practices and a good sense of observation, you can easily get rid of the stranglehold of a phishing campaign.
1- Always on your guard
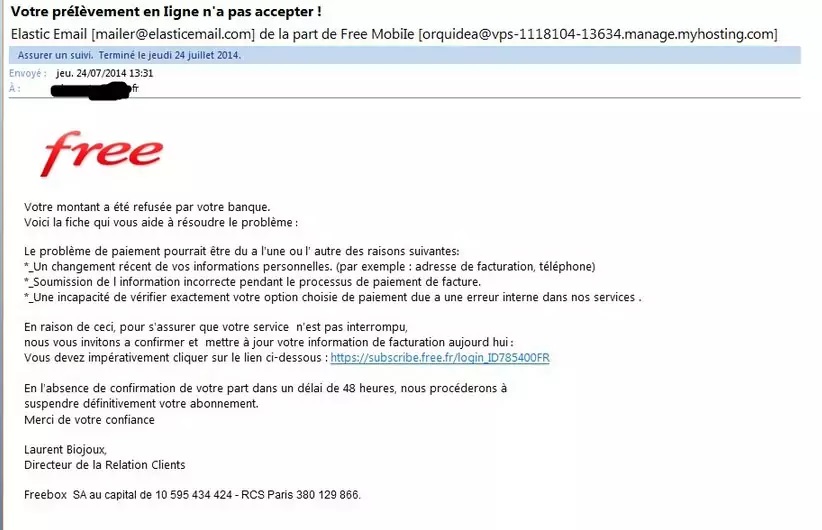
Indeed, every time you are connected to the Internet, you must be on your guard. With every message you receive, every email, the chances of it being a phishing attempt be more than 50%. This means that at all times, you will have to pay attention to all your correspondences especially when they come from unknown recipients. This seems to be over-distrustful, but an excess of mistrust that has its role. First be sure to always check the addresses that send you emails or messages online. Check the spellings as well as the links that are used in this kind of message. You can also make a few calls to make sure that the recipients who send you the message is beautiful and well the one who was supposed to do it.
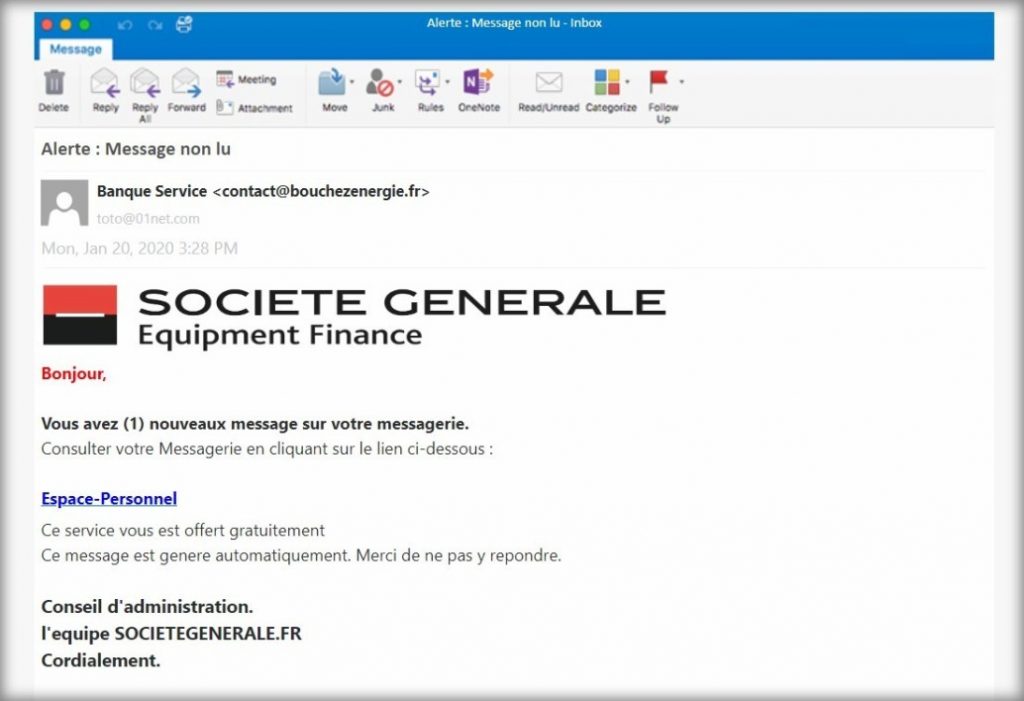
In practice, cyber-caregivers know that users of digital services are generally negligent people. It is on this negligence that they fully support their tactics. When you are faced with a sense of urgency, it is exactly at this time that you need to be most careful. Indeed, the idea is to prevent you from being as thorough as possible. Therefore, don't get caught up in the game. You have the right to doubt. You have the right to take your time to analyze things. Only reply or click on a link when you are sure and certain
2- Search the Internet
When you receive a message and the content is unreliable where you think is doubtful, take some time on yourself, and go searching the internet. You will see that some methods have been used before. All you need to do is type only a few keywords on Google's search bar.
"Test different queries: the first sentences of the message; The address of the sender of the email or a general description of the content of the message. You should come across consumer forums full of testimonials, expert associations like Signal Spam or warnings issued by Cybermalveillance or law enforcement. Or maybe you'll end up on Cyberwarfare, where we're dissecting the main French phishing campaigns. If there's any sign of your suspicions, go your way. As a last resort, share your suspicions of phishing with a more competent relative than you on the subject. explains one expert.
Another important point, when you receive a strange message, you should not hesitate to contact your IT security manager directly. When it comes to large companies, hackers use much more complex tactics than when it comes to a simple person.
3- Access directly to a website or app only through a link
This last point is essential. Indeed, it is through links that hackers manage to divert the attention of Internet users and direct them to platforms they control. This is why you are totally discouraged from using a link, especially a link that you receive by message or email. Access the website directly to your browser via the official application of the relevant platform.
Now access an unlimited number of passwords:
