Hack Facebook Passwords Tutorial
Facebook is the number one most hacked network

Hack Facebook Passwords Tutorial
Facebook is the number one most hacked network

It's a lot easier than you might imagine. Hackers have hundreds of ways to steal a Facebook password and their techniques are getting more and more sophisticated each time.
These days, most users think they are safe on the Internet. It's hard to imagine that you can have your life, your friends, your identity stolen on the web. We all tell ourselves that this only happens to others and that it will never happen to us. However, the day it happens, we wonder how we got there.
You should know that the Facebook account is one of the most important data sources. Indeed, if we take the fact that Facebook is the most visited social network in the world, users tend to share a lot more personal data about them because of the interactions they want to maintain.
Sometimes, Facebook account hacking is initiated in order to monitor a loved one, child, spouse, etc.
One thing is certain, the demand for Facebook hacking is exploding. Which means that anyone with an account on this social network is exposed in one way or another. That's why you need to know what threats you will face.
Here is a list of hacking techniques:
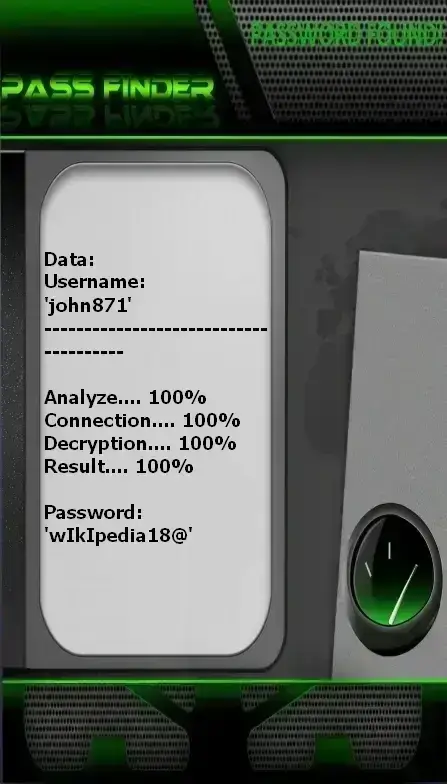
using PASS FINDER and @username
(also works with a phone number or email address).
This technique is much simpler—anyone can use it. It’s designed to be easy to use, even if you’re not a computer expert. Just follow the basic instructions and start using this application right away.
It’s a complete tool that makes your life easier and allows you to decode a Facebook account if you’re ever caught off guard.
Follow these three simple steps to find the password:
Additionally, you get a 30-day trial. At the end of this period, you can be fully refunded.
The pirate will buy advertising space on Internet sites and stick his advertising there where a dangerous link is hidden. Specifically, when a user clicks on the ad, they will be redirected to a page infected with malware.
Without the user noticing anything, hackers will continue to install malware on the victim's computer or smartphone. Especially since this is an endless chain since once the virus is installed, it will be able to reproduce itself ad infinitum.
The hacker will only have to wait to receive on his email the identifier of the Facebook account with his password. Be certain that a hacker can hack your FB password without you realizing it.

This technique is particularly difficult to put into practice. However, all the conditions are met for it to work. You thought it was impossible to siphon passwords without even using the Internet? The basis of this method is going to require the installation of a malicious program on a particular computer terminal. The victim's device, for example. Which will require in some way physical access to this computing device. There is the possibility of being able to use it both on Windows, Ubuntu or other Linux-like distributions. The computer program concerned is very discreet and light, it is only 4 KB!
Thanks to it, it is possible to receive and give information at a maximum distance of 6 meters. If the use of this technique is combined with a powerful reception antenna, it is possible to be able to receive them at a distance of 30 meters. Obviously, such a technique cannot make it possible to transfer data of a very large volume. However, this is sufficient to recover a password.

This consists of using the GSM network to extract data. You just have to know that it also works thanks to a malicious program that must be installed on the victim's computer. Thanks to this application, it is possible to launch some configurations. They will push your computer to function as a mobile by emitting GSM waves. With the right tools, hackers will know exactly how to exfiltrate the information they care about.

If there is one place where social engineering is very common, it is obviously on Facebook. Since the social network is frequented by a lot of people, doing social engineering becomes quite easy. Social engineering will consist of deceiving a person with whom one has established contact. The purpose of this contact is to get the person we have targeted to give us information that can be used to hack into their Facebook account. Obviously, the way to proceed will consist in generally using simple exchanges to first establish a bond of friendship and gradually release personal information. When social engineering is done between two people during an exchange, it can go unnoticed and usually takes less time. There are also methods that allow the cybercriminal to initiate social engineering, but on a large scale this time. This usually goes unnoticed, but you've certainly noticed posts on groups asking questions like:
These are not trivial questions because somehow they can help the hacking of thousands of Facebook accounts in one go. So if you see these kinds of posts, it's best to ignore them.

This method is known in French as " diversion de clic ". It was from 2008 that the concept of clickjacking became popular. This hacking technique is usually used to operate on web applications. Clickjacking consists of deceiving a user when he clicks on a tab or an image, which aims to make him perform an action that he did not foresee or want.
The technique works as follows:
We all know the importance of session cookies. These little beacons that allow us to find our way when browsing on several platforms at the same time. Cookies are truly useful and practical. However, if a hacker manages to gain access to it, they can use it to gain access to your session and hack you. Indeed, session cookies leave a trace and allow access to your account without you needing to retype your identifier. And it is precisely this situation that the hacker will exploit. That's why when you log in to your Facebook account, after logging out, take the trouble to erase cookies for more security.

A fake WiFi can be the basis of your hack. Indeed, if the cybercriminal follows your habits, he can trick you and trick you into connecting to a WiFi network trapped by hackers.
The first step is to create a WiFi network. To do this, you just need to deploy a router that allows Internet connection such as a WiFi router. Moreover, even with a smartphone it is possible to create WiFi access. Once this network is immediately available to the target, hackers can then monitor the traffic of the person who connects to their WiFi network. This gives them the advantage of diverting the connection to a phishing web page, allowing them to deceive the user's vigilance and ask them for their connection credentials.

We speak of interception of traffic when it is possible for a hacker to be able to learn the content of the communication between two computer terminals. In other words, when the computer terminal A communicates with the computer terminal B, the hackers recover the thread of the communication by trying to know exactly what information is circulating during this communication. They can achieve this in various ways. For example, by creating a fake WiFi hotspot as indicated above or by using cookies for the purpose of hijacking the session and intercepting the content of the communication. But, the most dazzling interception consists in capturing the communication between the different packets. At this level, it is almost impossible for a user to do anything to protect themselves from it. Communication between DNS servers is done by packet transmission. This transmission is based on a unique signature that does not change. When a hacker has succeeded in becoming aware of this signature, he can create new packets using this same signature in order to divert communication between different servers. The user will be exposed to spying without being able to do anything.

It is a great classic in the cybercrime sector. Every year, new tools are developed to make cracking passwords easier. It is a method that consists of using software or an automated script that will be responsible for generating thousands or even millions of combinations of words or symbols with the aim of being able to find the correct password. The success of this technique depends on the quality of the software used for this purpose, the power of the computer as well as the nature of the password to be cracked. One thing is certain, Facebook users are vulnerable to this method. Why ? Quite simply because the power of the processors makes it possible to crack passwords quickly. Beyond password cracking, we can also take the opportunity to mention the attack on the dictionary which is also one of the greatest classics. This is essentially based on a set of passwords or connection identifiers collected by various means (data leak, scraping or hacking). This data is compiled into a database that will be used to find the identifiers useful for hacking accounts.

At this point, it is useful to know how to ensure better security for your Facebook account. There is a practical way to protect yourself from cyber attacks.
Finally one last thing to know absolutely, 100% security does not exist. In other words, the effort to protect is something constant. You must always be on the alert and be ready to react in case of doubt.
First, consider the security of your computing environment. Everything you use to access the Internet should be secure.
Hacking someone's Facebook account without their consent is illegal and considered a violation of privacy and cybersecurity laws in most countries.
While it's technically possible, using hacking techniques to monitor someone's Facebook account without their consent is unethical and potentially illegal. It's better to establish open communication and trust with your child.
While no method is foolproof, you can significantly enhance the security of your Facebook account by enabling two-factor authentication, using strong and unique passwords, keeping your software updated and being cautious of suspicious links and activities.
Yes, there are legal and ethical alternatives such as discussing concerns directly with the person, seeking professional help if necessary, or involving law enforcement if there are serious issues.
You can report hacking attempts or suspicious activities on Facebook by using the platform's reporting tools, which are usually found in the settings or help sections of your account.