Hack GMail password
Some tips from hackers!

Hack GMail password
Some tips from hackers!

GMail is the most widely used email service in the world, it is important that you know why hackers can take your account integrity by storm.
It is very difficult for all GMail users to remember their password. They have so many on different sites that it's almost impossible to remember them all! This is why hackers find it much easier to hack GMail account passwords and gain access to our privacy.
We are all vulnerable. By the way, passwords like " 12345 " are still as popular as ever. Our current life requires us to have a minimum of protection, our digital life must keep a minimum of privacy.
Every day, hackers are developing new hacking techniques to bypass GMail security. There are articles explaining that a hacker can easily hack a GMail password, it can apply to your account too. They use a whole variety of little software like brute force. They make several probabilities, several tries until the password is cracked. Other methods like creating fake WiFi networks are meant to only capture internet traffic. Thus the password is saved for sure.
What you need to know is that when hackers hack into security systems, even the most complicated ones like GMail, they most often do so from a simple computer. Contrary to popular belief, they don't use a super modern last generation computer. Their main tool is the Internet which is used only as a source of information, which is then used against your GMail account. It's a double-edged sword, the Internet is a magnificent tool that helps billions of people around the world but also provides an extraordinary reserve for hackers. They have their own channels for distributing pirated software that they exchange among themselves.
Google believes in providing good protection for its GMail users. It is entirely false. GMail is an email, it's not a digital safe!
Google's email client is used by millions of people around the world. With the expansion of Android and the ease of creating a GMail account, it has become almost a generality to have an email address hosted by the Mountain View giant. This means in particular that there is a huge amount of data to be hosted on this platform. Just like us, hackers know this and intend to take advantage of it.
Additionally, hacking is initiated by relatives wanting to know what their contact is doing when they log on to email. It can be parents watching over their children, or a spouse watching over their mate.
What makes hacking your GMail account even more dangerous is social media. Indeed, our social network accounts are affiliated with our email addresses. Which means that if a hacker manages to hijack your GMail account, your online accounts that are affiliated with that GMail account will be vulnerable to them.
Depending on the objectives and means, everyone uses techniques that suit the situation. Here are some methods you should know that can be used to hack your GMail account:

account using PASS BREAKER.
PASS BREAKER is a powerful tool that easily decrypts a GMail password. Simply enter an email address, and it will display the corresponding password. How? Through an advanced algorithm that directly accesses internal password databases.
You can now download PASS BREAKER and start decoding your GMail account password.
Visit the official website to access PASS BREAKER: https://www.passwordrevelator.net/en/passbreaker
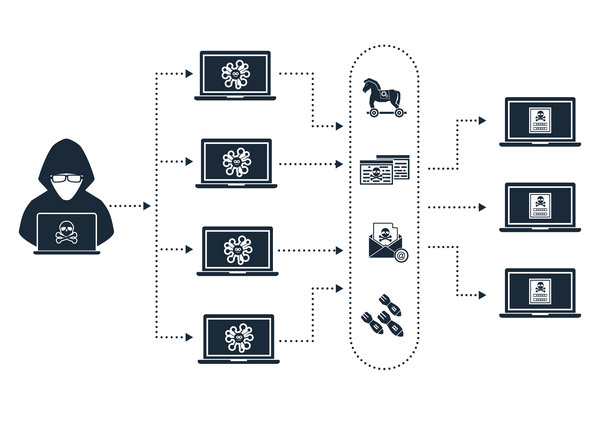
Basically botnets are used for cryptocurrency mining or large-scale piracy based on ransomware, for example. However, one should not rule out the possibility of their use to steal your GMail credentials. GMail being a strategic web communication space, all means are good to be able to access it. Botnets are a set of computers and computer devices connected (smartphones, connected objects) to each other. This type of network is set up by actors with the aim of generating great computing power by merging each device individually. And this, of course, to the very detriment of the owners of the computer device concerned. When the malware that allows this interconnection is installed on a terminal, it can act as a Trojan horse and suck the data from that computing device. It is for this reason that botnets can be used against you in the context of hacking your GMail account.

The screen recorder, as it is said in English, is a malicious program that has the ability to spy on the screen of your terminal and send it to its operator. As the name suggests, it records everything that is done on the screen of the device. So imagine that when you log into your GMail account everything you do will be logged. The hacker will then be able to know what information you use to make this connection successful.

We talked above about this computer program that records the screen and ensures that everything on the smartphone or computer is visually transmitted to the malicious operator. The Keylogger works the same way, however this software is more specialized in recording keystrokes. The Keylogger is a malicious program that allows a hacker to know what you write from the keyboard of your terminal. Therefore, if you are infected with a Keylogger, your password will be at the mercy of hackers. However, you will need to install it on your device first. In this context, hackers often use:
The dictionary attack is a technique that will find the password by trying several possible combinations stored in a database called dictionary. The hacker will use malicious software which will automatically sort through the database kept by him. This analysis of all the information stored in the dictionaries is automatically applied so that the correct password is found and executed automatically at login.
All of these combinations that are used to initiate the dictionary attack are often at the origin:

This attack is widely used on social networks with the aim of diverting users' attention. It works much like phishing. However, in its context, it is not necessary to click on a link. You can be a victim of clickjacking just by clicking on an image or simply on a like button. It is indeed very difficult to be able to detect this method of hacking. The user simply has to trust his intuition when he finds himself in such a situation.

Brute force attacks are part of computer hacking and consist of the hacker forcing the connection to an account or access by trying to make a multitude of proposals for connection identifiers so that the system ends up validating the correct proposal.
The principle of this attack is simple, thanks to automated software, the hacker will test different combinations one by one. The combinations are generated following well-defined logic algorithms. For example, the system used can carry out analyzes in alphabetical order. This can also be in ascending or descending order with respect to the number content of the password. It can also be, by totally exploiting random letters to prevent the protection measures deployed on certain connection systems, such as a barrier, from being able to interrupt the attack. Hackers may then be tempted to use random combinations. To maximize the chances of this cyber attack, hackers often combine the brute force attack with the dictionary attack or the rainbow table attack which are variants of it.

It is a technique that comes under pure cryptanalysis. It simply consists of converting sounds and vibrations emitted by a particular device, whether computer, analog or mechanical (cryptoprocessor, rotors, computer keyboard, etc.). But the implementation of this technique of course requires that the hacker is a good equipment. Indeed, he must have receivers, sound analyzers and some cryptographic software.
You should know that acoustic cryptography has emerged since the Second World War. This is a hack that was ahead of its time.

It is not strictly speaking hacking since it can be used outside the world of the internet. Social engineering is first and foremost manipulation. It is a method that allows someone you trust to gather useful information to ultimately use it against you. Not everyone on social media is honest. However, in some public or private groups, interactions lead to forging links. If there is one thing to remember from these exchanges on these groups and even on social networks, it is that there will always be people who want to take advantage of your inattention to try to hack you. Often when they need information, they will pressure you to provide it. Therefore, it would be interesting to avoid publishing too much data that has a direct or even indirect relationship with your private or professional life. Avoid reacting to posts that ask for your age or date of birth. The same is true for exchanging messages in private with people you do not know physically.

When you forget your password, you can recover it by launching a reset procedure. This is quite simple and convenient, however, it can also be used against you. Indeed, if the hacker launches password recovery and he has some personal information about you, he will be able to choose a new password that will allow him to have control of your GMail account. In this context, you will first need to have access to your phone since when resetting the password, an SMS is sent with a reset code allowing the hacker to complete the procedure. But having your phone number isn't really a problem anymore. All you have to do is use the technique of SIM card hijacking, called SIM Swap. A method of phoning the telephone company pretending to be the owner of the telephone and asking to transfer the telephone number to another SIM card. When the hacker completes this procedure, resetting a GMail password will be a piece of cake for him.

There are a large number of techniques to hack yourself. But what about methods to protect yourself? First of all you have to know one thing: the security of your GMail account is personal to you. Discipline is a requirement in the face of cybercrime, there is no flawless protection, absolute security is impossible. As we know " as long as it's computerized, we can hack it ". Therefore, here are some methods that you really need to consider in your protection policy:
GMail hacking is unfortunately quite common due to various methods employed by hackers, such as brute force attacks, social engineering and keyloggers.
While GMail implements security measures, no system is entirely foolproof. Users should also take additional steps to safeguard their accounts.
Common hacking techniques include brute force attacks, phishing, keyloggers and social engineering.
Users can protect their GMail accounts by using strong, unique passwords, enabling two-factor authentication, regularly updating software and being cautious of suspicious emails or links.
Yes, using a VPN can enhance your online security by encrypting your internet connection and masking your IP address, making it more difficult for hackers to intercept your data.
If you suspect unauthorized activity on your GMail account, immediately change your password, review your account settings for any changes and report any suspicious activity to Google.