
9 password hacking techniques
In today's article, we'll talk about how hackers do and their different techniques for hacking your passwords.
These are usually techniques mainly used by computer hackers who have bad intentions. Hackers have now created highly developed algorithms, which manages to speed up the process to find your passwords.
Putting in place a difficult and long password is highly recommended by cybersecurity, but this same cybersecurity does not show us how to identify hacking in your device. No matter what strategy you created passwords with, hackers always have this ability to decipher your passwords.
This article may also be of interest to you: Cracker or hack a password
Today we will give you some password hacking techniques used to hack into our accounts.
1 – Use PASS REVELATOR
PASS REVELATOR is a suite of hacking software designed specifically by budding hackers who have managed to hack a set of protocols thus allowing access to any password.
Whether it's Facebook, GMail, Instagram, Yahoo!, Twitter, Outlook or even a WiFi network, these software will be able to deliver passwords to you in just a few minutes!
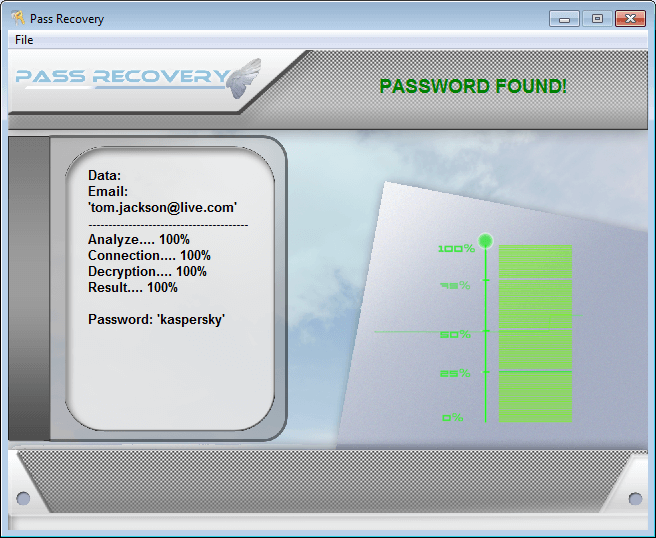
You can download the software on this page: https://www.passwordrevelator.net
2 – Dictionary Attack
Dictionary attack is a method that much used by most hackers to find the secret phrase in tempting their luck several times. This is a classic file containing a set of unusual words that several people use as a password. This is one of the easiest methods of hacking the word someone's pass. But producing a difficult password can beat this attack very easily.
3 – Brute Force Attack
The main objective of the strategy of the Brute's strength is to break the password. He's going to try all the possible combinations to get to the point of finding the real word Pass. However, nowadays, users are becoming smarter, so the length of passwords makes things a little difficult making Brute Force's attack quite complex to decipher them. It looks like elsewhere if you notice the dictionary attack.
4 – Phishing
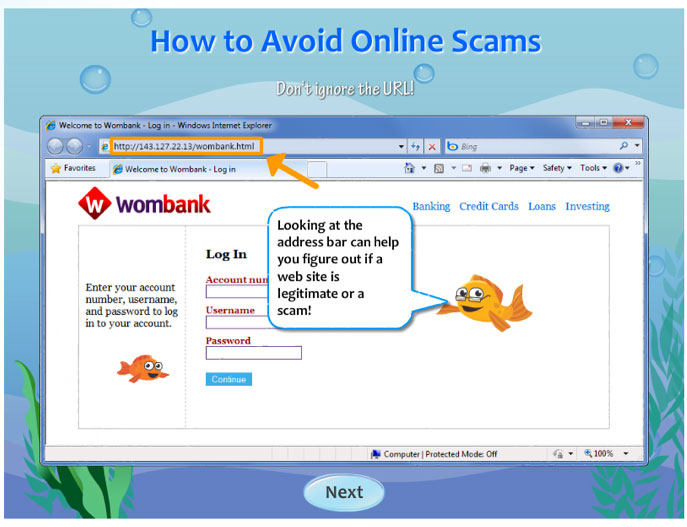
Phishing or phishing is the most a fairly simpler method used by computer offenders. It does not done absolutely nothing extraordinary, it merely asks the user their passwords. However, the word request technique individual and different passes. hackers will create to this the effect of fake pages, fake email addresses, and fake software, etc. one once you have committed the carelessness of entering your contact information and personal information such as your details, everything is transferred to the hacker server.
5 – Malicious Software
These programmes are largely developed hackers for the sole purpose of causing the destruction of their target. Viruses and worms are installed in the user's system to they get to fully use the infected machine or a corrupted network as a whole. They are transmitted by email or are simulated any program.
6 – Attack via Ports scan
It is a method sometimes used to find flaws on a specific server. It is mainly used by IT security officials to detect vulnerabilities in the their system. The attack via port scan is used to transmit a information to a port and wait for a response and data received from the port which are an invitation to hackers to attack the server.
7 – Social Engineering
Social engineering is a hacking technique that will rely heavily on human interaction and often requires inciting people to not respect normal security rules. In this way, hackers can try different ways to get into security procedures.
8 – Find passwords by guessing
Here, hackers can try to guess your words pass, they may even try to guess your security response. in In short, hackers can try to guess everything to break your security and hack into your account. However, thanks to two steps and code alert connection this type of techniques are usually a failure in our days.
9 – The Hybrid Attack Method
Here, the hybrid attack is another good hacking method that is widely used by hackers. It's a fusion of the dictionary and brute force. In such an attack, add them add numbers and symbols to the name of the files to be able to decrypt the password. The majority of people change their passwords only to add only a number to their current password.
Now access an unlimited number of passwords:
