AllAntiCovid: a phishing campaign targets app users
It has been detected a phishing companion that specifically targets Android users.
The situation was deciphered by the online media Numerama.
The hackers decided to send a text message by posing as the French government. The goal is to push the people targeted by his SMS to download the allAntiCovid tracking app. Of course this is not the real application but rather a bank Trojan.
This article will also interest you: Mobile tracing: "AllAntiCovid" does better than StopCovid with its 3 million downloads in a few weeks
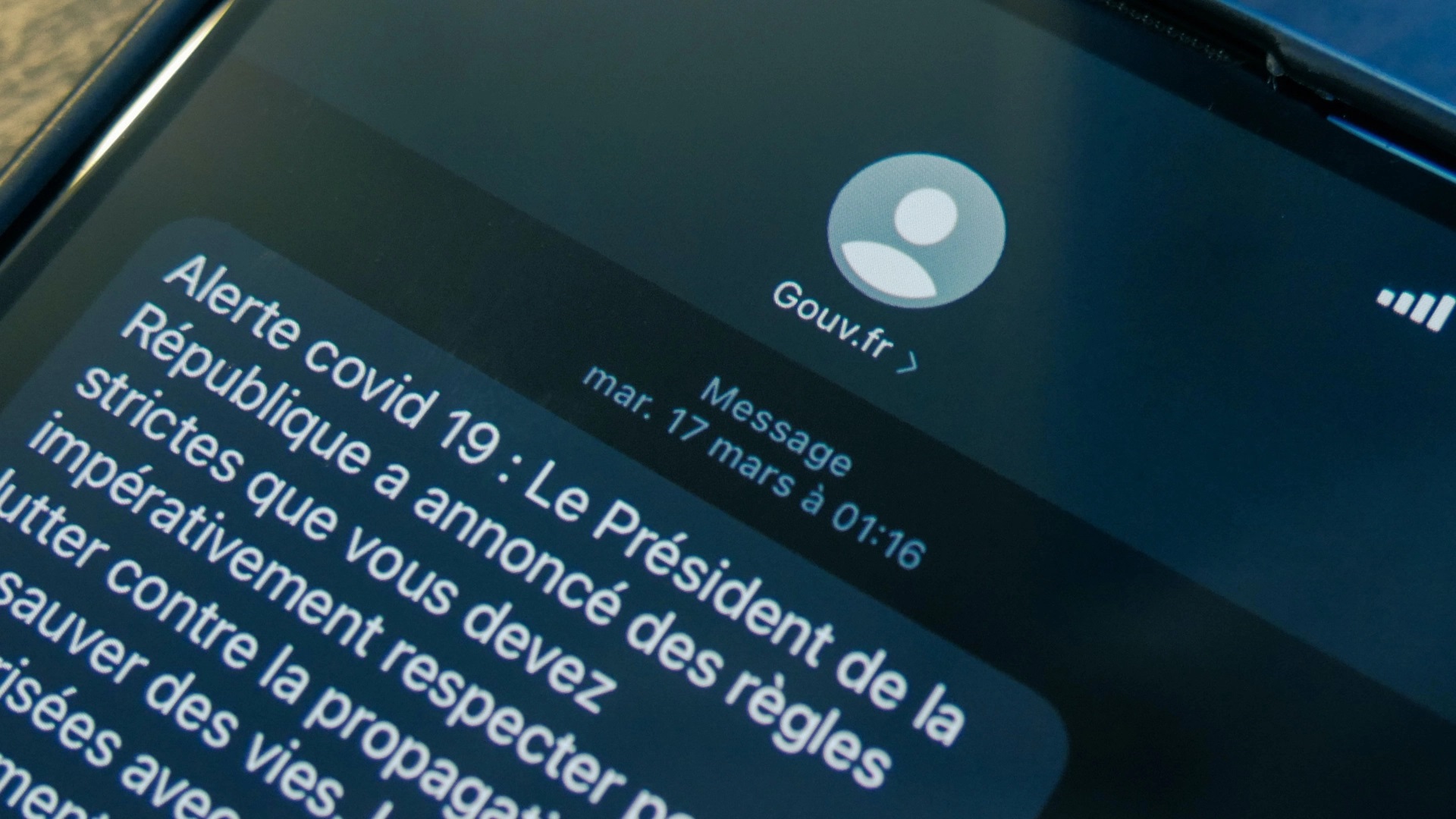
Messages began to erupt on Wednesday, December 2, 2020. All French citizens are then asked to be very careful. Despite this, AllAntiCovid's Twitter account meant that the phishing campaign ended on the same day, December 2.
Yet people continue to receive you this kind of suspicious messages asking them to download the app. The structure of the SMS is similar to that sent by the government, not long ago. But there are clear differences when you are attentive and vigilant.
At first, the URL in the message is already likely to arouse mistrust. It is accompanied by a "Bit.ly" shortcut link, while the main address used by the government in its messages is "http://bonjour.tousanticovid.fr." And worse the shortcut link contains the word "AntlCovid19" trying to look as much as possible link used by the government, as highlighted by the CyberWar platform.
In addition to this other details are challenging. The "i" used in "AntlCovid19" has been replaced so as not to attract attention but it is not the same. A common technique where it is possible to use several word compositions in order to resemble another when it is totally different for the one who does not observe well. In addition, the message used in the phishing campaign comes from "GOUV.FR." Instead, the official authorities use "Gouv.fr." These details are very useful for observing a phishing message unlike an official message.

As a result, it was observed that the URL in the phishing message directly leads to a platform clearly directed by cyber criminals. It is a website that takes on the appearance of an official website with the visual identity that goes with it. There, the user is pressured to download an APK file called "tousanticovid.apk". In this condition there are only Android phone users who can download the app and install it. While the official app can be used on both iOS and Android. Enough to attract attention.
In reality, the malware application before installing it, the user is asked to disable the Google Play Protect, so as to facilitate his intrusion into the device of the victim, in order to steal enough data. Mainly banking data because of the nature of the malware. The malware nation was specified by Maxime Ingrao, a researcher specializing in computer security, and Android at the firm Evina.
"From your ID to your password to dual authentication SMS, the virus captures all the data you need to get it right. Collecting those from your Facebook or WhatsApp accounts is also not a problem. "Security expert."
Now access an unlimited number of passwords!