Hacking a WiFi code
Internet wherever you want...

Hacking a WiFi code
Internet wherever you want...

When we talk about hacking WiFi keys, we immediately think of the hacker hidden in the shadows with his computer and his software running to decrypt passwords like on television. But be careful, WiFi password hacking is a professional business, we will show you how hackers do it.
Don't believe that only hackers can hack WiFi connections, anyone can do it, it's just a matter of logic and willpower. Companies often call on outside consultants for whom they pay a lot of money to test the security of their networks.
Professional networks are generally well protected with encryption types WEP, WPA and now WP3. Too bad for them, this WiFi security is not infallible. They also have the option of allowing only those who are invited to connect. They can create a list of devices by entering the MAC addresses that have permission to connect.
Most of the time, WiFi security breaches are due to poor network management by the user who is often new to this area. The flaws can also be the technology used. As a general rule, when a password needs to be created, it is best to create a phrase with special characters. The longer the key, the harder it will be to hack it. There are also very serious flaws with Internet service providers who all put default passwords on their routers.
The user new to the subject will not have fun changing it, which leaves the door open to any hacker to connect to a WiFi network. A badly thoughtful hacker can also simulate a hotspot to encourage people to connect to it. It will then see everything, recover everything like email address passwords, credit card numbers, absolutely everything...
You may have already wondered how a hacker can hack your WiFi connection key. There are a lot of users who want to find a method to connect to your WiFi network without asking your permission.
It’s therefore wise to ask: what method is used to bypass the security of a WiFi network? What technique can be used to access a WiFi hotspot when you don’t have the password?
PASS WIFI is precisely the solution.

Use PASS WIFI to decode a wireless Internet access key and enjoy freedom! You’ll be able to connect to the internet because PASS WIFI analyzes data stored in network databases. From that moment on, it scans and retrieves router passwords in plain text!
PASS WIFI fulfills your request to find the password for any router or WiFi hotspot.
Simply install PASS WIFI on your device. Open the application and start the scan. Select the password of the network you want and connect.
Within minutes, the application will provide you with the password from its database, granting you unrestricted access to the WiFi network.
PASS WIFI is already used by thousands of people worldwide. Plus, you get a 30-day free trial. At the end of your trial period, you’re either satisfied or refunded.
Don’t hesitate—try PASS WIFI now by downloading it from its official website: https://www.passwordrevelator.net/en/passwifi
There are other techniques used by hackers to access a WiFi network without having to ask the network owner for their connection key. We have listed for you the simplest to the most complicated techniques.
Here are the methods of hacking WiFi keys:
The brute force attack is a technique widely used in the cyber malicious sectors. Hackers will try to find your WiFi key by trying several types of combinations based on numbers, letters, symbols… so that with each attempt they are able to eliminate possibilities to go for the right combinations. It is a technique that seems tedious, however, to make the task easier, they use computer programs designed to generate these combinations and calculate these access possibilities. These are computer programs that are developed based on powerful algorithms with a set of data that is commonly circulating on the Internet including certain usage habits.
It often happens that when trying password combinations, hackers use real credentials collected from the Internet and stored in databases. This variant is called the dictionary attack because it takes inspiration from existing passwords in order to create new ones. The objective with the dictionary attack is to be able to study the modes of formulation and the techniques of constitution of users' passwords in order to guess their login credentials.

We are talking about an information theft technique that has existed since the Second World War. Indeed, this method doesn't require an Internet connection or the use of a modern computer terminal. You just need to be able to intercept vibrations and sounds, as well as to have a sound decryption tool. Acoustic cryptanalysis consists of collecting sound and vibration data and then converting it into information. Noises that may be emitted from computer keyboards by the CPU or from a server fan motor. This method can spy on any tool that emits sound. Yet we know that the materials we use on a daily basis such as our computers make noise. With an antenna adapted to capture these sounds, the hacker can then make conversions and find the information that is generated or that passes through this computing device.

This method doesn't require the use of the Internet to be used for hacking. Indeed, all data hacking or theft of sensitive information does not necessarily require being connected to the Internet, this is often the mistake that many users make. For example, this technique only requires capturing the light emitted from your screen. Indeed, any computer device emits light beams depending on its use. The frequency of these beams varies according to the use made. It has been shown that with a special lens it is possible to capture these light beams and use them to collect information. Also, if the hacker is within a tolerable distance and can access the light emitted by your computer, they may well determine what you are doing, all without using the Internet.

Few users are aware that Bluetooth can be used to hack them. Indeed, even if the WiFi network is now losing speed since it is used less and less, the majority of our computer devices are equipped with a Bluetooth connection. If today it makes it easier to interconnect our tools such as wireless headphones and refrigerators, previously the Bluetooth network was used much more for data transmission. This is exactly what we all forget because this feature still exists even though it is no longer used. Indeed, there are still vulnerabilities present in the Bluetooth networks of computing devices. Thanks to these vulnerabilities, people can hack you when your Bluetooth is on. Hackers use computer software that can, for example, extract information from your computer device and use it as they wish. It is also possible to use Bluetooth to share connections to bypass security requirements and find the WiFi key.

The USB cable does not need an internet connection to be used. The USB cable is used to charge your computer device such as smartphones, but it is also used for the transmission of information from device A to device B.
Therefore, if you use your USB cable on a corrupt connector, hackers can exfiltrate your data. This eventuality is not as rare as you think. Indeed, we may want to charge our device when we are in a public place such as an airport or a supermarket. These places often offer spaces that allow charging through USB connectors. It is likely that hackers can take advantage of these connectors to install devices with integrated data extractors.

When device X connects to a WiFi network, it is possible to share the identifier via this device which has already connected. Which means that you must first have in your hands a device that has already connected at least once to this WiFi.
Go to settings, WiFi setting and you will see a QR Code. Click on this QR code and scan it. It gives you direct access to the WiFi connection. You can even take a photo of it and distribute it freely.
There are different ways to share a login ID. For example, there are applications where people who have already been able to access WiFi networks in public places decide to share them themselves by identifying them, which creates a kind of social network allowing its members to know where to connect to a Wi-Fi router.
There is also the possibility of discovering the password in plain text. Indeed, if you go to the settings and on WiFi security, you will see the password section. Click on discover the password in order to display it.

If you can access the router physically, you have the option of initiating the reset by pressing the dedicated button just on the back. Once the router has been reset, use the default password written on it. If nothing is mentioned, use the default password, in fact, almost all router models have the same password. If you know the pattern, it is possible to find the default password on a website. You can then take advantage of the WiFi connection.
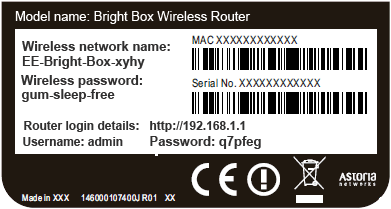
The default password generates a login ID that is assigned to a device or software upon installation or commissioning. It works the same for almost all computing devices. More often than not, devices of the same model use the same default passwords and many users never bother to change them. Using the model number on the router, simply go to the manufacturer's website to find information about the default password. This technique is widely used by hackers, experience it, you will certainly be surprised to see how negligent many users are at this level.

Thanks to a Keylogger, it is possible to collect everything that the victim will enter, namely the connection identifiers of his WiFi network. If you can physically access their device, use a USB flash drive or memory card and discreetly transfer the app to their device. Once this action is done, simply wait for the victim to start connecting to the network and you will have the login credentials. If it uses the virtual keyboard, chances are you won't be able to get the credentials you want because the keylogger only works for physical keyboards. To overcome this failure, then use a screen recorder, this is a program that gives you access to the activity of the computer device via the screen.
Hacking techniques are numerous and highly sought after. It is therefore important to consider the method to improve the security of its WiFi network. If we have previously given you techniques that can be used to hack your router, then it is legitimate that we give you techniques that will help you to better secure it.
Be aware above all that there is no absolute security method. No matter what you are going to deploy as a protection system, it is essential that you keep in mind that there is always a security vulnerability that can be used against you. It doesn't mean you're going to get hacked, it just means it's important to be disciplined for the long haul.
First, it is important to eliminate risky behavior.
To improve the security of your WiFi network, here are some tips that we suggest you follow scrupulously.
Hacking into WiFi networks without permission is illegal and constitutes a violation of privacy and cybersecurity laws in most countries. It can lead to severe legal consequences.
While hacking WiFi networks is technically feasible, engaging in unauthorized hacking activities is unethical and illegal.
To protect your WiFi network, you should use strong encryption methods such as WPA2, regularly update your router's firmware, use complex passwords, enable network encryption and limit access to authorized devices.
WiFi hacking can lead to unauthorized access to sensitive information, identity theft, financial loss, legal ramifications and damage to personal and professional reputation.
Yes, you can hire professional cybersecurity experts or ethical hackers to conduct security assessments and penetration testing to identify vulnerabilities in your WiFi network legally.
If you suspect unauthorized access to your WiFi network, immediately change your network password, update your router's firmware, enable stronger encryption and monitor network activity for any suspicious behavior. Consider contacting law enforcement or cybersecurity professionals for assistance.