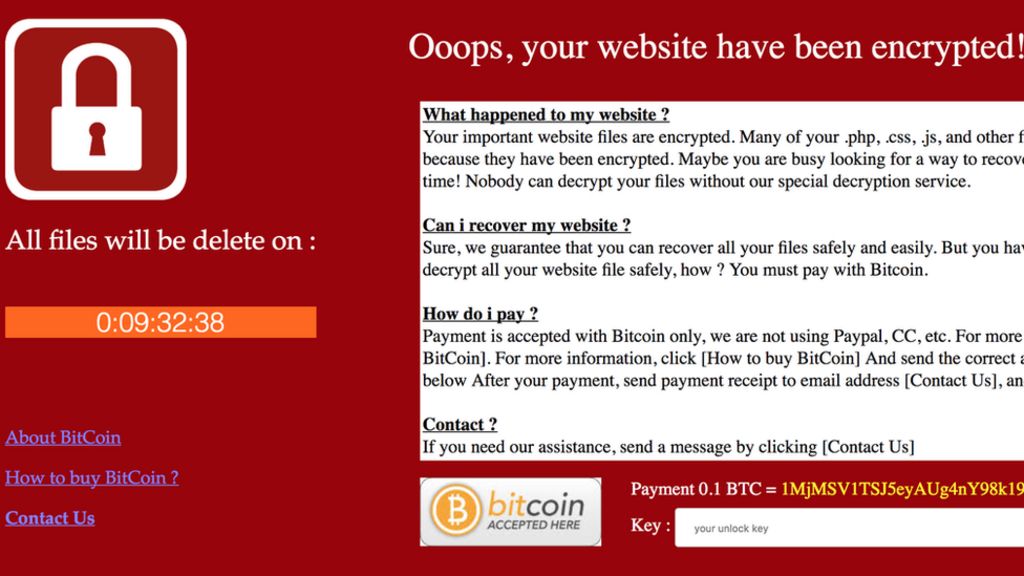
Cyber criminals spare those who have their keyboards in Russian, is this the beginning of a strategy?
May 22, 2021Today, officially, everyone knows that Russian hackers tend to spare companies that operate within their state. Even Russian companies that… Continue Reading