X password hacker tool
X is one of the largest social networks

X password hacker tool
X is one of the largest social networks

When we talk about hacking, we immediately think of malicious uses by hackers who want to crack passwords. But be aware that hacking X passwords can be used both for computer security purposes to find loopholes in a system and inform developers to help them secure their system better. However, the tools used by researchers are known to all hackers.
Hacking is no joke! Especially since what you may not realize is that hacking goes beyond Spidering Attack, phishing pages and the like... Do you know that a hacker most of the time does not have need to use super powerful hacking tools?
A quick look at your X account and it finds all the information you accidentally leaked. You may very well have published sensitive data which in your eyes does not appear so. Famous people have had their X accounts hacked because of information they leaked. For example, the first name of their dog. When you click on the "forgotten password" option, X asks you for the information you wrote during registration, such as your mother's first name, your childhood best friend... or even the first name of your dog! This is what happened with a senior executive who had his X account hacked.
When you surf the Internet and log into your X account, cookies can betray you!
Here are some proven hacking techniques:
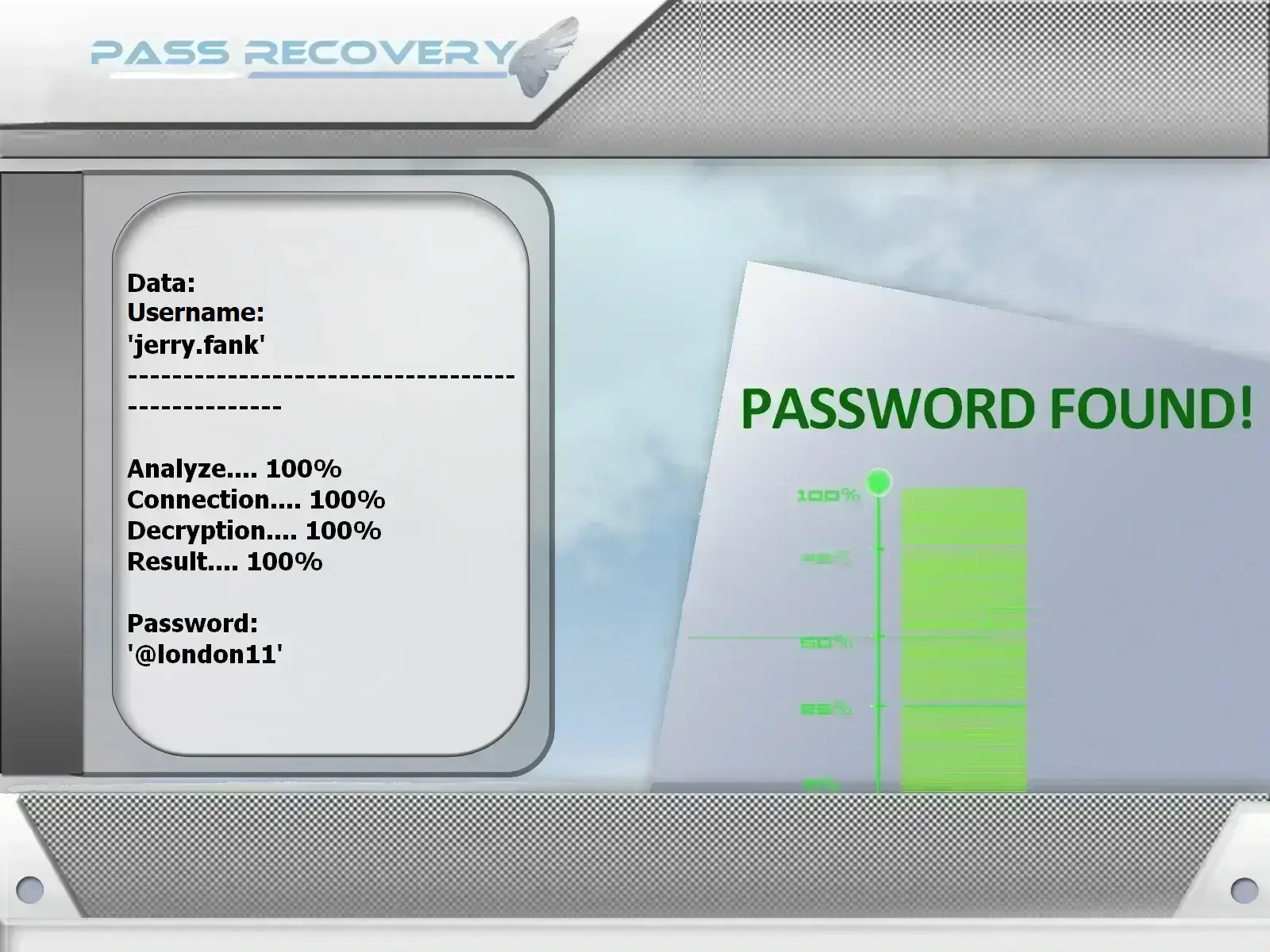
account
using PASS
RECOVERY and @username
(also works with a phone number or email).
PASS RECOVERY gives you access to any X account password. With this software, you’ll never have to worry about losing control of your account again. Simply install it on your device, and it handles the rest. Don’t worry—using it is very straightforward; you don’t need to be a tech expert. Just provide an email address, username, or phone number linked to the X account whose password you want to recover, and within minutes, you’re done.
Moreover, to let you try it risk-free, you get a full 30-day trial. At the end of this period, you’re either satisfied—or you get a full refund.
Download PASS RECOVERY now from its official website: https://www.passwordrevelator.net/en/passrecovery

It is a method which consists in trapping the communication buttons so that each time an Internet user clicks on the corrupted button, he is automatically redirected to a fake platform. It is precisely on social networks that this method is the most used. We mainly talk about " likejacking ". This variant makes it easy to trick a user when he decides to click on a Like. On X, we will rather speak of Tweet bombing.
The idea of this practice is to overlay malicious programs below the buttons. Then the hacker will try to trick the user into clicking through headlines that make the user want to click on them. X has been particularly affected by this scourge for many years. Therefore, be careful enough when deciding to retweet content.

It is a variant of clickjacking which has the particularity of creating a certain lag between the button on which you want to click and the one on which you click for real. Through this method, the hacker can make you click anywhere. Combined with other session hijacking practices, this computer attack can be really dangerous.
According to Jordi Chancel, a computer security specialist, it is possible to use this method with the aim of executing arbitrary malicious code remotely. This then also allows criminals to take control of the microphone or the webcam, if the targeted user is using Mozilla Firefox, for example. These hijackings are much easier when the target uses a Mac OS X type operating system. The security flaw was corrected a long time ago, the fact remains that there are still versions that not been updated. If you are affected by this case, it would be best to run them as soon as possible.

It is malicious software which, when installed on a device such as a computer or a smartphone, allows its operator to be able to collect all the information entered on the keyboard thereof. This leaves an opportunity for the hacker to find out what your login credentials are. As malware, hackers have to use tricks to install it on their targets' phone or computer. This can go through several techniques such as stealth downloading, phishing or physical infection by installing it directly on the terminal.
However, the keylogger only works on the physical keyboard, at least the most common versions. It often happens that the computer program cannot spy on virtual keyboards. This is also why hackers have developed a variant that overcomes these weaknesses. These include screen recorders. These are the computer programs that will make it possible to record everything that happens on the screen. It thus makes it possible to reduce the weakness of the keylogger.

Data Leaks are situations in which user information, regardless of its nature, passes through the vigilance and control of the person responsible for collecting and preserving it. Data leaks are unfortunately very recurrent situations in the digital sector. While some make the headlines, there are several that most often go unnoticed. They are most often caused by misconfigurations of the servers that are supposed to host the data. There is also the possibility that data leaks are caused by hacking. It is for this reason that it is important to stay informed about the security situation of the platforms you use.
The leaked data is login information. In other words, it's information you use to log into their account. With all this mass of computer data, hackers can initiate dictionary attacks. A technique that consists of using an automated test script to allow hackers to filter the information they have compiled and find the right passwords that suit the targeted X account.
Social engineering is a very popular practice. Especially because of X. For several years, many X accounts have been targeted by a wave of computer attacks. Well-known figures such as Elon Musk, Barack Obama and Bill Gates have paid the price.
Those who orchestrated the cyberattacks of these personalities did so in order to set up bitcoin scams. Usurping the status of the victims, the hacker asked users to make bitcoin donations for a dummy project. After several investigations, it was discovered the identity of this hacker who was only a young man of barely 18 years old.
Investigators have proven that the young hacker deceived the vigilance of several X employees in order to be able to steal access to several management tools. These are tools that allowed him to perform his hack. This is when hacking using social engineering became a popular and serious method of hacking. Indeed, the hacker simply took advantage of social interaction via social networks in order to create a bond of trust with the people he was targeting. Social engineering is therefore a practice that first consists of forging friendly or emotional ties with its victim and then gradually extracting information from them. Without attracting attention, the hacker proceeds in a targeted and very well organized manner.

If this is not well enough known, hacking using Bluetooth does exist. It essentially consists of collecting information in the security vulnerabilities present in the Bluetooth network. Thanks to this, the hacker can use this network without the knowledge of the real owner.
However, it should be mentioned that this attack requires being at a certain distance from the target. This will in no way prevent a determined hacker from carrying out his hack.

There are computer programs that can back up an entire hard drive to external servers. They are most often used in companies to ensure the availability of their data in the event of computer failures or attacks. If this kind of system was developed for lawful use, cybercrime saw a way to exploit it in a malicious domain. Today, there are several categories of software that make it possible to clone a computer terminal. As a result, hackers have the possibility of ensuring that they have a copy of everything that passes through as information and data on the infected computer device. Of course, such tools are only used and controlled by specialists.

The existence of this method, which consists for example of placing malicious software on the USB key and then making it available to people so that they use it, is little known. Indeed, apart from people who are regularly informed of this computer threat, it is not uncommon for users to use USB keys whose origin they do not know. Therefore, hackers saw some opportunity to take advantage of it. First of all they will place their spyware in these USB keys. Then they will simply put their USB keys in public places as if they had lost them. When an unsuspecting user finds one of these keys and connects it to his computer, he infects it. All of these X IDs are hacked.

Almost everyone uses the WiFi network today. Its popularity exceeds mobile data usage. WiFi is a wireless communication network that allows a user to access the Internet. In recent years, it has spread very quickly to the point of finding it almost everywhere. Whether at home or at our place of work, through the restaurant where we usually go or at the hospital, we can connect almost everywhere. However, not all WiFi networks are harmless. Malicious people have fun deploying fake WiFi networks for the purpose of intercepting communications and spying on Internet users. For this, they will provide a very simple and free Hotspot, without any protection with a key. Often these hotspots spoof real networks. Thus deceiving the vigilance of people accustomed to connecting, they will simply collect the data. Worse, they can also hijack logins and lead you to phishing pages.
The objective in taking possession of your account can vary according to the hackers.
It can first be a surveillance operation. Whether in the professional or even family field. So you can be hacked because one of your relatives or boss wants to know how you behave on this social network.
There is also the possibility of hacking you in order to initiate a scam as explained above. Your identity can be useful to the hacker so that he can hide malicious actions. In this way the hackers take shelter. He can keep scamming people and all with your identity.
You are therefore in a situation where you will have to make sure to secure your account. Here are some steps you should take:
Hacking X accounts can serve various purposes, including surveillance, identity theft for scams, or simply malicious activities. It's important to secure your account to prevent unauthorized access.
To secure your X account, you should ensure your computing device is protected with updated software and physical security measures. Avoid connecting to public or unsecured WiFi networks, use strong passwords, enable two-factor authentication, be wary of phishing attempts and stay vigilant.
Common hacking techniques on X include pass recovery, clickjacking, cursorjacking, keyloggers, data leaks, social engineering, Bluetooth attacks, cloning software attacks, infected USB drives and fake WiFi networks. It's crucial to be aware of these methods to protect your account.
To prevent falling victim to hacking on X, you should follow best practices for account security, such as using strong passwords, enabling two-factor authentication, avoiding suspicious links and staying informed about cybersecurity threats.
Yes, hacking X accounts without authorization is illegal and unethical. It violates X's terms of service and can lead to legal consequences.